Image: Trend Micro
In June 2024, Trend Micro identified a new spear-phishing campaign targeting political organizations, research institutions, and think tanks in Japan. This operation, attributed to the cyber-espionage group Earth Kasha, marks the resurgence of the ANEL backdoor, a tool previously associated with the APT10 group and dormant since 2018. The campaign also employs NOOPDOOR, a modular backdoor used for high-value targets, underscoring Earth Kasha’s adaptive tactics and evolving capabilities.
The campaign’s primary intrusion vector involved carefully crafted spear-phishing emails. These messages, often sent from compromised or free email accounts, contained links to malicious OneDrive-hosted ZIP files. These lures, written in Japanese, carried enticing subjects like:
- Interview Request Form
- Japan’s Economic Security in Light of Current US-China Relations
- [List of Government and Public Institutions]
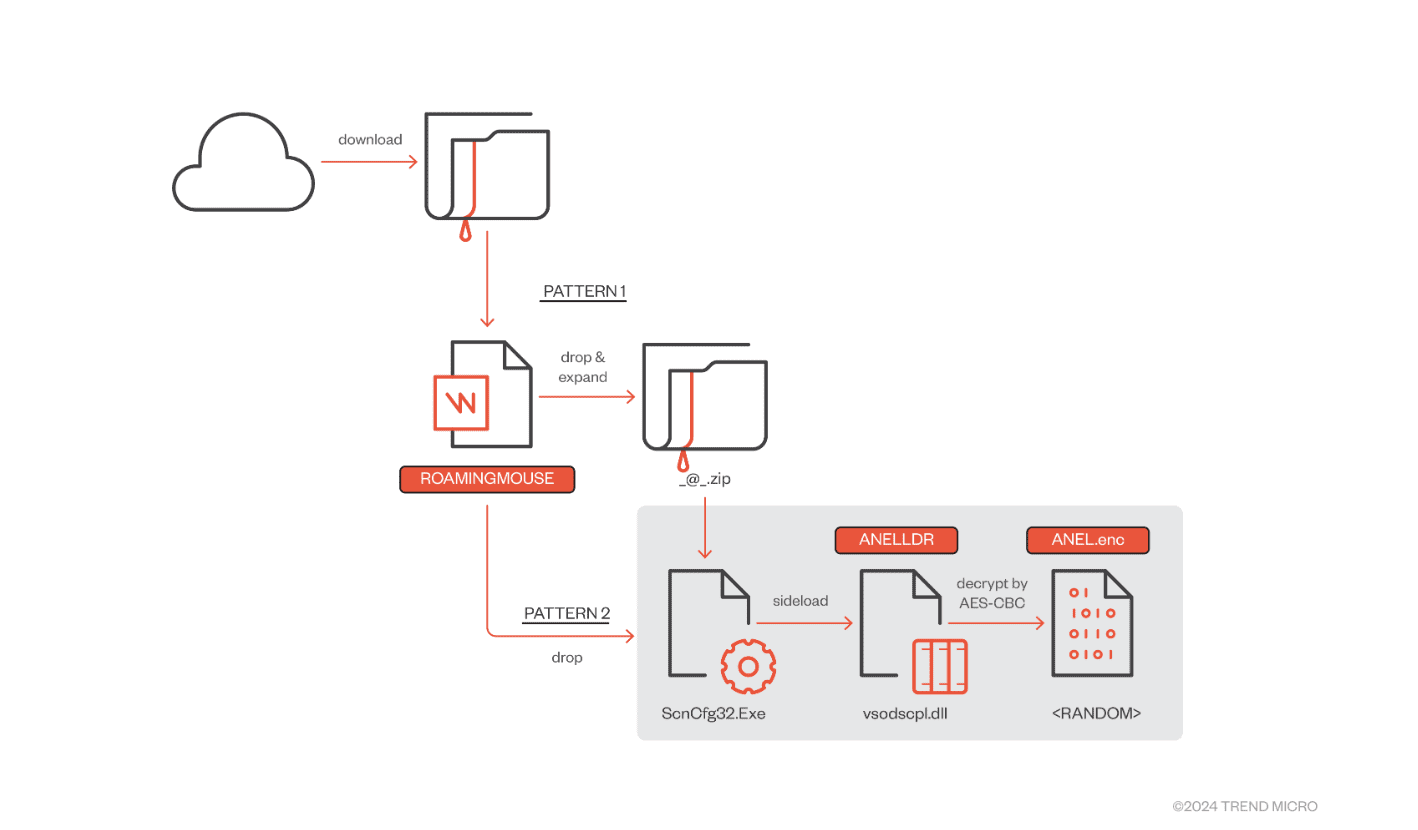
Upon download, victims encountered a variety of infection methods, including macro-enabled documents, shortcut files, and PowerShell-based payloads. The macro-enabled documents introduced a malware dropper named ROAMINGMOUSE, which extracted and executed ANEL-related components while evading detection through sandbox-aware tactics.
ANEL, a 32-bit HTTP-based backdoor, has re-emerged with versions such as “5.5.4 rev1” and “5.5.6 rev1,” showcasing improvements since its last appearance in 2018. One update in version “5.5.6 rev1” included a new backdoor command leveraging a UAC bypass technique for executing programs with elevated privileges.
The report highlights ANEL’s reliance on evasion techniques, such as:
- Custom Base64 and HEX-encoded payloads.
- Dynamic DLL sideloading using legitimate applications.
- Control Flow Flattening and junk code insertion for anti-analysis
Post-compromise, ANEL facilitated information gathering, such as taking screenshots, retrieving network details, and executing system commands. For high-value targets, Earth Kasha deployed NOOPDOOR, a modular backdoor with advanced capabilities, cementing the campaign’s espionage motives.
Trend Micro’s analysis attributes the campaign to Earth Kasha, citing similarities in tactics, techniques, and procedures (TTPs) with previous operations. The reuse of ANEL, along with code overlaps between ANELLDR (ANEL’s loader) and NOOPDOOR, suggests a connection to former APT10 developers. The resurgence of ANEL aligns with Earth Kasha’s “are particularly interested in topics related to Japan’s national security and international relations,” the report states.
Related Posts:
- Earth Kasha Expands Operations: New LODEINFO Malware Hits Government and High-Tech
- North Korean Cyberattacks Persist: Developers Targeted via npm
- Cyber-Espionage Campaign Unveiled: Operation Cobalt Whisper Hits Sensitive Industries
- Earth Estries’ Evolving Toolkit: A Deep Dive into Their Advanced Techniques