
Examples of ApateWeb’s Layer 3 payload
In the ever-evolving landscape of cybersecurity threats, researchers from Unit 42 have uncovered a menacing large-scale campaign, aptly named ApateWeb, that’s been operating under the radar. ApateWeb employs a labyrinthine network of over 130,000 domains to distribute scareware, potentially unwanted programs (PUPs), and other deceptive content. While these programs may not fit the traditional definition of malware, they serve as gateways for cybercriminals, exposing victims to more severe threats.
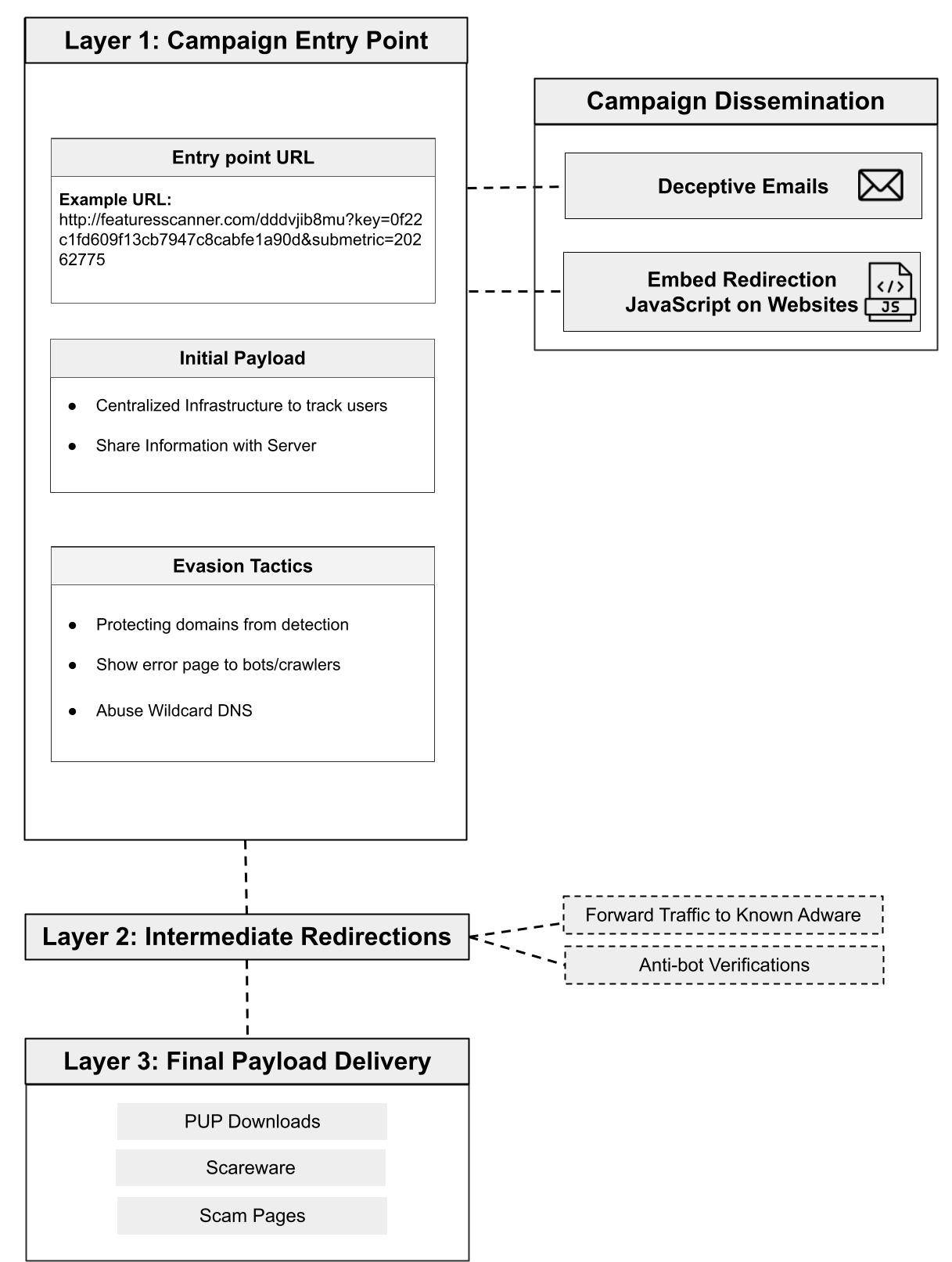
At the heart of ApateWeb lies a sophisticated infrastructure, meticulously designed to deceive security defenders and ensnare unsuspecting victims. The campaign operates through a multi-layered system comprising three primary layers:
- Layer 1: The Campaign Entry Point:
ApateWeb begins its operation with the creation of a custom URL that serves as the entry point for victims. This initial payload leverages centralized infrastructure to track victims and share critical information with the campaign’s servers, paving the way for subsequent redirections. To thwart defenders, Layer 1 employs various safeguards, including redirection to search engines, displaying error pages to bots/crawlers, and exploiting wildcard DNS patterns to generate a multitude of subdomains.
- Layer 2: Intermediate Redirections:
Following the initial entry, Layer 2 takes over, orchestrating a series of intermediate redirections. The unique aspect of this layer is its unpredictability, as the same entry URL may lead to different redirections during various test runs. These redirections can either point to adware sites, such as tracker-tds[.]info and jpadsnow[.]com, or halt the process with anti-bot verifications.
- Layer 3: Redirection to Final Payload:

The final phase of the ApateWeb campaign, Layer 3, is where victims encounter the malicious payload. This payload can manifest as scareware, PUPs, or scam notifications. The payload often includes rogue browser executables like Artificus Browser or intrusive browser extensions like Browse Keeper and Go Blocker.
ApateWeb’s ability to evade detection is central to its success. The campaign employs several ingenious tactics to protect its domains and maintain operational security:
- Protecting Domains from Detection: ApateWeb conceals its attacker-controlled domains from detection by presenting benign content to direct visitors. This approach ensures that security crawlers, performing routine scans, do not block these domains.
- Displaying Error Pages to Bots/Crawlers: When security crawlers attempt to access the entry URL, ApateWeb responds by displaying custom error pages. These error pages help the campaign evade detection by mimicking a legitimate website.
- Large Number of Registered Domains and Wildcard DNS: ApateWeb controls a vast network of over 10,000 registered domains, exploiting wildcard DNS patterns to create an extensive array of subdomains. This tactic makes it challenging for defenders to identify and block the campaign.
To attract victims, ApateWeb employs two primary methods:
- Embedded Redirection JavaScript on Websites: The threat actors behind ApateWeb insert malicious JavaScript code on various websites. This code creates an overlay on the webpage, leading victims to ApateWeb entry URLs when they click on the page.
- Deceptive Emails: ApateWeb leverages email as another distribution channel. Deceptive subject lines lure victims into opening emails and clicking on ApateWeb URLs, thus expanding the campaign’s reach.
ApateWeb is a testament to the ever-evolving sophistication of cyber threats. With its intricate infrastructure, elusive tactics, and capacity to exploit vulnerabilities, it poses a significant risk to internet users. While its primary payload may not be traditional malware, it serves as a gateway for cybercriminals to launch more severe attacks. Vigilance, robust security measures, and awareness are crucial in combating such campaigns and safeguarding against their deceptive strategies.