Image: Apple
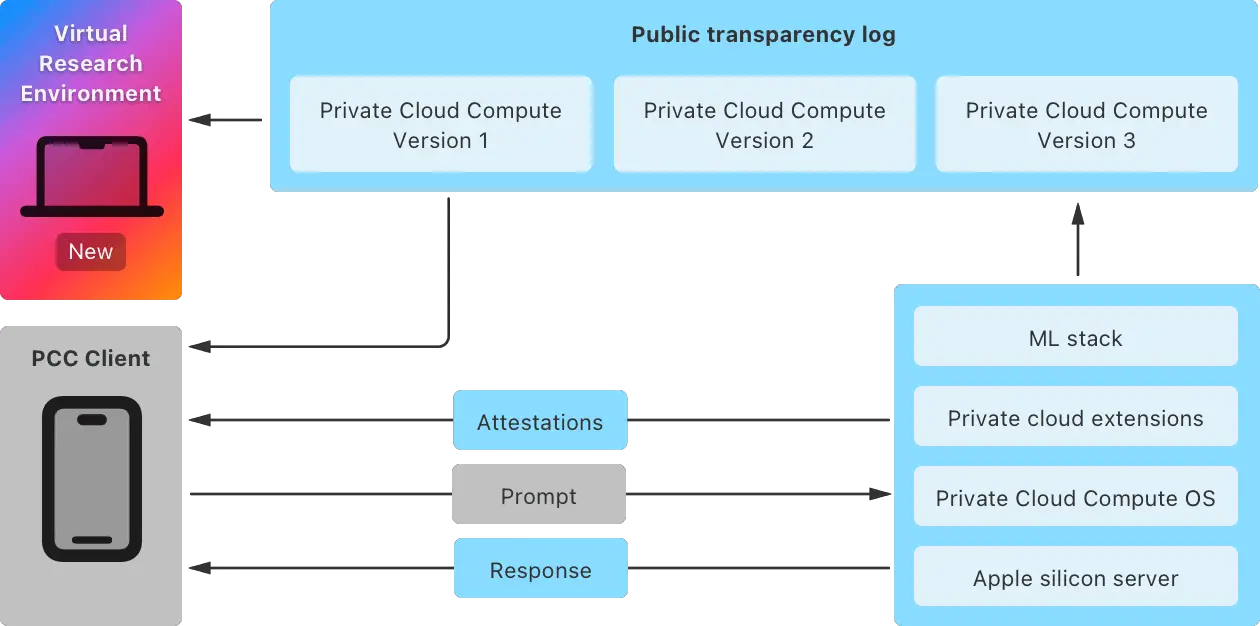
Apple has introduced a Virtual Research Environment (VRE) to provide public access for testing the security of its Private Cloud Compute (PCC) system. Additionally, the company has open-sourced several critical components for researchers to analyze, aiming to affirm the robustness of the architecture and its adherence to security and privacy standards.
PCC is a cloud-based system for processing data through artificial intelligence, safeguarded by end-to-end encryption. This ensures that data transmitted from Apple devices to PCC remains inaccessible to the company, available solely to the user.
Previously, access to PCC was limited to select researchers and auditors to verify its compliance with declared privacy standards. Now, anyone interested can explore this system and examine its claimed security features.
Alongside the VRE, Apple released a security guide for Private Cloud Compute, detailing the system’s architecture and its core components. The virtual environment allows researchers to run a PCC node in a virtual machine, scrutinize the software, and identify potential vulnerabilities.
The following components’ source code is available to researchers:
- The CloudAttestation project, which is responsible for constructing and validating the PCC node’s attestations.
- The Thimble project, which includes the privatecloudcomputed daemon that runs on a user’s device and uses CloudAttestation to enforce verifiable transparency.
- The splunkloggingd daemon, which filters the logs that can be emitted from a PCC node to protect against accidental data disclosure.
- The srd_tools project, which contains the VRE tooling and which you can use to understand how the VRE enables running the PCC code.
Apple has also expanded its bug bounty program, adding new categories specific to PCC. The maximum reward is $1 million for remote code execution with privileges based on a user’s data request. Disclosures of user data are rewarded up to $250,000, and network-based attacks with elevated privileges offer payouts ranging from $50,000 to $150,000.
The company states that any issues with a significant impact on PCC’s security will be considered for rewards, even if they do not align with the specified categories.
Apple asserts that Private Cloud Compute represents the most advanced security architecture for cloud computing with AI integration, yet it seeks researchers’ assistance to enhance its resilience further.
Related Posts:
- Apple Confirmed that All Mac and iOS Devices Are Affected by Chip Vulnerability
- Phishing Scam targets iOS user in India