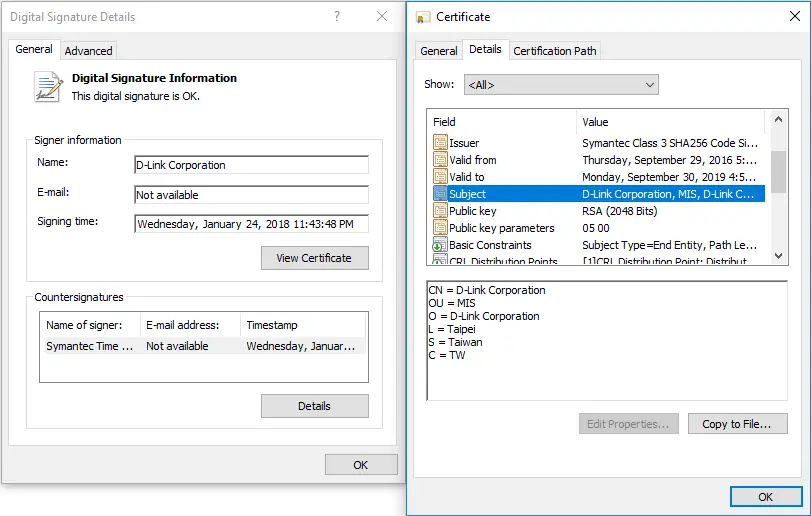
Security researchers from ESET have discovered a new malware activity related to APT organisation BlackTech, which is abusing a valid digital certificate stolen from D-Link network equipment manufacturer and Taiwan security company Changing Information Technology. Its malware disguised as a legitimate application.
A digital certificate issued by a trusted certification authority (CA) is used to sign computer applications and software cryptographically, and the computer will trust the execution of these digital certificate programs without issuing any warning messages. In recent years, some malware authors and hackers looking to circumvent security scheme technologies have been abusing trusted digital certificates. They use their compromised code signing certificates associated with trusted software vendors to sign their malicious code to avoid being targeted. Detected on the network and user devices.
According to security researchers, this cyber espionage organisation is highly skilled, and most of them are targeting East Asia, especially Taiwan. ESET identified two malware families. The first malware called Plead. It is a backdoor for remote control designed to steal confidential files and monitor users. Plead has signed its code with a valid certificate since at least 2012. The two malware are password stealers intended to collect saved passwords from Google Chrome, Microsoft Internet Explorer, Microsoft Outlook, and Mozilla Firefox.

Image: welivesecurity
The researchers notified D-link and Changing Information Technology of the problem, and the damaged digital certificates were revoked on July 3 and July 4, 2018, respectively.
This is not the first time a hacker has used a valid certificate to sign their malware. A valid digital certificate also used in 2003 for the Stuxnet worm for Iranian nuclear processing facilities.
Source: TheHackerNews, Security affairs