Researchers from Kaspersky Lab stated in an article published on June 13th that they discovered continuous cyber espionage against a data centre in Central Asia in March this year. The goal is for a Watering Hole Attack was implemented on the government’s government website to obtain a wide range of government resources.
The researchers said they believe the event can be traced back to the fall of 2017 and attributed it to an APT27, a hacking group supposed to be made up of Chinese.
APT27, commonly known as LuckyMouse, is also known as Iron Tiger, EmissaryPanda, and Threat Group-3390. The organisation is believed to have been active since 2010, targeting hundreds of organisations around the world, including US defence contractors, financial services companies, European drone manufacturers, and a French energy management company’s subsidiary in the United States.
The article points out that the compromised data centre is only a springboard for actual attacks. The ultimate goal of the attacker is to inject malicious JavaScript code into its associated official government website to implement a waterhole attack – the site visitors from the legal government. The site is redirected to a page that provides malware.

The researchers said that they are currently unable to determine how the data center was compromised, but believe that the attacker may use two methods: The first method is the above-mentioned water pit attack, some of the internal data center employees may account So it was hijacked; the second method, which may involve phishing attacks, based on malicious Office documents. For example, a publicly disclosed Office remote code execution vulnerability, CVE-2017-11882, has been used by the APT27 since December 2017.
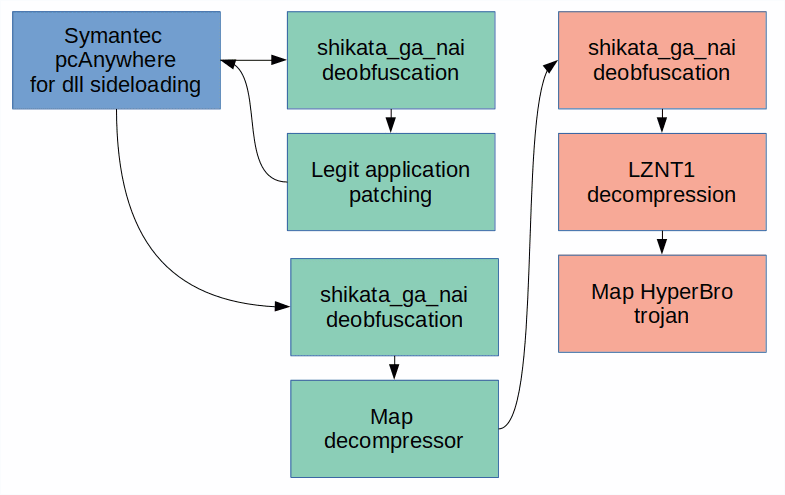
Besides, the APT27 accused of using the HyperBro Trojan in this attack to establish persistence on infected systems and create a path for remote management. The time stamp of the sample ranges from December 2017 to January 2018. The traces found by the researchers indicate that the HyperBro Trojan entered the data centre system in mid-November 2017.
The initial module will deploy three files (which are considered to be commonly used by Chinese hackers): a legitimate Symantec pcAnywhere (IntgStat.exe) for DLL loading, a .DLL launcher (pcalocalresloader.dll) and final stage decompression Program (thumb.db). After all these steps have been completed, the final stage Trojan will be injected into the process memory of svchost.exe.
The infected government website redirects the country’s visitors to the browser using the framework BeEF or the scan box reconnaissance framework ScanBox that performs the same tasks as the keylogger.
The article concludes that the National Data Center is a valuable source of data, but it can also be abused to harm government websites. The APT27 has been very active recently, and it has been shown that the National Data Center as a springboard for attacks suggests that they may have found a newer, more covert method to infect victims in Central Asian countries.
Source, Image: securelist