Border Gateway Protocol (BGP) is an autonomous system routing protocol that runs on TCP. It is the basis for the operation of the Internet. However, due to the design time (born in 1989, BGP) is too long, it is inevitable that there is a security risk.
System administrators sometimes incorrectly configure the BGP protocol, causing traffic to be hijacked into advertisements. In some cases, malicious traffic is routed and normal user traffic is hijacked, affecting the user experience.
To this end, a group of researchers from Europe and the United States created a framework called ARTEMIS, which enables service providers to solve BGP hijacking problems in minutes. Researchers say ARTEMIS makes it possible to provide public BGP monitoring services for real-time streaming.

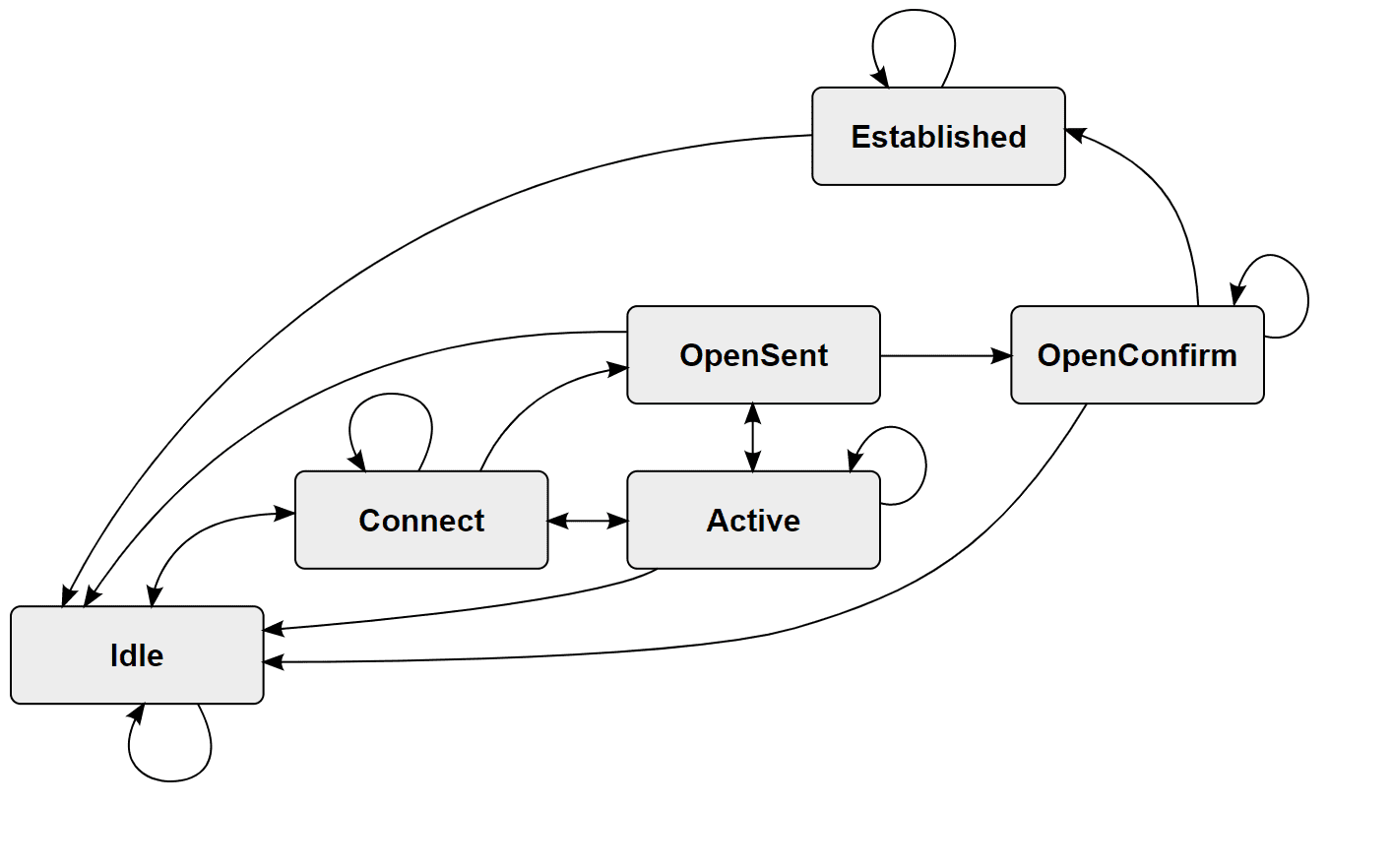
By Johannes Rössel (Self-made, after Image:Bgp-fsm.jpg) [GFDL or CC-BY-SA-3.0], via Wikimedia Commons
Using such infrastructures as RouteViews Project and RIPE Routing Information Services (RIS), ARTEMIS allows operators to ease BGP hijacking in their own infrastructure without having to rely on third-party services. In the view of researchers, this means that network operators using BGP to monitor traffic can respond to BGP hijacking without having to wait for manual verification of the alert.
Network operators can configure ARTEMIS using information from the Autonomous System (AS) to observe external feeds that affect AS-PATH events, which means that the system can detect any type of hijacking event and generate alerts.
The alarms generated by ARTEMIS include various outputs, such as the prefixes affected, the type of hijacking attempts, the observed effects, the AS numbers involved, and the test confidence.
When a BGP hijacking event occurs, ARTEMIS, though it does not let the network operator lose contact with other operators, will split the affected prefixes in response, which is an automatically generated step by the system. When it detects the hijacking of the 10.0.0.0/23 prefix, the network performs prefix splitting and announces two other sub-prefixes: 10.0.0.0/24 and 10.0.1.0/24. These sub-prefixes will be split on the Internet, BGP will prioritize more specific prefixes, and contaminated ASs will re-establish legitimate routes.
BGP MOAS announcements are another part of the ARTEMIS mitigation strategy where mitigation companies use BGP/MOAS or DNS to redirect traffic to their location and cleanup centers, remove malicious traffic, and forward legitimate traffic to victims By.
If BGP hijacking is detected, the ARTEMIS system sends an alert to the enterprise responsible for mitigating the router hijacking the location or prefix, which means that the enterprise is attracting traffic from the Internet and can, therefore, pass the traffic back to the legitimate network.
The researchers said that in the experiment, they could detect BGP hijacking in as little as five seconds and most ASs recovered from hijacking within 60 seconds.