Asyncshell: The Evolution of APT-K-47’s Cyber Arsenal
The Knownsec 404 Advanced Threat Intelligence team has uncovered a sophisticated and evolving threat from the APT-K-47 group, also known as Mysterious Elephant. This South Asia-based Advanced Persistent Threat (APT) group has been linked to a series of malicious campaigns since 2022, with its latest iteration revolving around an upgraded version of its Asyncshell malware, dubbed Asyncshell-v4.
APT-K-47’s recent campaign used a Hajj-themed decoy to deliver a malicious payload through a CHM (Compiled HTML Help) file. The payload, designed for asynchronous command execution, connects to a Command and Control (C2) server masquerading as a normal web service request. The Knownsec team noted, “this sample is an upgraded version of Asynshell,” exhibiting characteristics such as base64 variant encoding, disguised C2 addresses, and reduced log messages for stealth.

Decoy File
The Asyncshell malware has undergone multiple iterations since its discovery in early 2024, each introducing new features and techniques to evade detection:
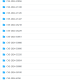
- Asyncshell-v1 (January 2024):
Initially exploiting CVE-2023-38831, this version targeted victims in Pakistan, Bangladesh, and Turkey. It supported cmd and PowerShell commands but relied on TCP for communication. The decoys included documents on civil servant remuneration. - Asyncshell-v2 (April 2024):

Decoy File
A transition from TCP to HTTPS communication made this version harder to detect. Attackers used decoy PDFs with matching filenames to lure victims. The malicious payload executes, displaying the decoy document while silently connecting to the C2 server.
- Asyncshell-v3 (July 2024):
Marked by the introduction of AES-encrypted configurations, this version decrypted server details from a file named license. A scheduled task named “WinNetServiceUpdate” was used to maintain persistence, with decoys including documents on policy formulation. - Asyncshell-v4 (October 2024):
The latest iteration continues to refine its methods, leveraging asynchronous programming for flexible C2 connections. It employs base64 variant encoding to hide strings and mimics legitimate web service requests to ensure prolonged access.
APT-K-47’s Asyncshell campaigns rely on layered obfuscation and deception techniques:
- Encrypted Payloads: Use of AES and custom base64 algorithms to mask C2 details.
- Decoy Documents: Tailored themes like religious events and policy discussions to increase credibility.
- Disguised Persistence: Files mimicking system utilities (e.g., cal.exe) and scheduled tasks for stealthy execution.
- Web-Based C2 Communication: Transition to HTTPS to blend in with normal web traffic and avoid detection.
APT-K-47’s activities highlight the increasing sophistication of South Asian APT groups. By combining obfuscation, strategic decoys, and advanced communication methods, Asyncshell serves as a potent tool for espionage and data exfiltration.