Attackers Exploit Construction Site Trust, Deliver TrollAgent Malware
Security experts at the AhnLab Security Intelligence Center (ASEC) have recently uncovered a malware distribution campaign targeting a Korean construction-related association website. The attackers have compromised legitimate security software installers, turning them into vehicles for TrollAgent malware delivery.
Understanding the Attack Chain
-
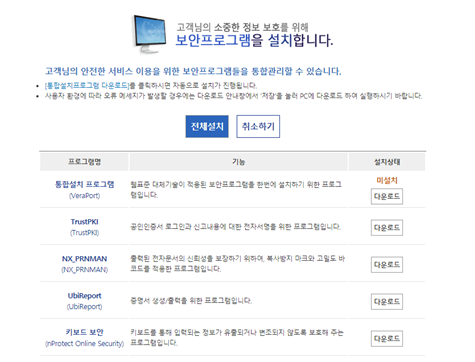
Deceptive Login Requirement: To access the website’s services, users first face the requirement to install several designated security programs. This common practice lowers suspicion at the initial attack stage. The infected installer, named “NX_PRNMAN,” served as the Trojan horse, masquerading as a necessary security tool. This method of attack was not static; it evolved. Initially, in December 2023, the malware was distributed through a different program, “TrustPKI,” but by January 2024, “NX_PRNMAN” became the new vessel for this deceit.

The login process of a certain Korean website | Image: AhnLab
-
Malicious Payload: One or more of these mandatory installers have been modified to include hidden malware strains, delivering both a backdoor and Infostealer component.
-
Strategic Distribution: The compromised installers seem to be uploaded to the website within specific timeframes. This could be a deliberate tactic to evade detection, infecting victims in waves.
-
Subverted Trust: The attackers have obtained a legitimate code signing certificate from ‘D2Innovation’, a Korean defense company. By digitally signing the malicious installers, they increase the chance of bypassing security software during download and execution.
Malware Capabilities and Implications
-
Infostealer (‘TrollAgent’): The primary malware, dubbed “TrollAgent,” was a data thief developed in GoLang and capable of stealing a wide array of information, including system data, credentials, and even browser histories and bookmarks. This Infostealer was not working alone; it was accompanied by backdoor malware strains that allowed the attackers to commandeer the infected systems remotely.
Troll Infostealer’s source code Image: AhnLab
-
Backdoor (GoLang/C++): Based on code similarities with previous attacks, this component grants attackers the ability to:
- Remotely control infected machines
- Execute arbitrary commands
- Plant additional malware
- Facilitate lateral movement within a compromised network
Call to Action and Security Implications
-
Assume Compromise: Users who have recently accessed the affected website and downloaded security programs should treat their systems as potentially compromised. This includes:
- Immediately running comprehensive scans with reputable antivirus and anti-malware software.
- Changing critical passwords (banking websites, work accounts, etc.)





