authoscope v0.8.1 releases: Scriptable network authentication cracker
authoscope
authoscope is a scriptable network authentication cracker. While the space for common service bruteforce is already very well saturated, you may still end up writing your own python scripts when testing credentials for web applications.
The scope of authoscope is specifically cracking custom services. This is done by writing scripts that are loaded into a Lua runtime. Those scripts represent a single service and provide a verify(user, password) function that returns either true or false. Concurrency, progress indication, and reporting are magically provided by the authoscope runtime.
Changelog v0.8.1
- Dependencies have been updated to resolve a build issue with openssl 3.0, #82 (thanks for reporting @loqs!)
git clone https://github.com/kpcyrd/authoscope.git
cargo install
Usage
base64_decode
Decode a base64 string.
base64_decode("ww==")
base64_encode
Encode a binary array with base64.
base64_encode("\x00\xff")
clear_err
Clear all recorded errors to prevent a requeue.
if last_err() then
clear_err()
return false
else
return true
end
execve
Execute an external program. Returns the exit code.
execve("myprog", {"arg1", "arg2", "--arg", "3"})
hex
Hex encode a list of bytes.
hex("\x6F\x68\x61\x69\x0A\x00")
hmac_md5
Calculate an hmac with md5. Returns a binary array.
hmac_md5("secret", "my authenticated message")
hmac_sha1
Calculate an hmac with sha1. Returns a binary array.
hmac_sha1(“secret“, “my authenticated message“)
hmac_sha2_256
Calculate an hmac with sha2_256. Returns a binary array.
hmac_sha2_256(“secret“, “my authenticated message“)
hmac_sha2_512
Calculate an hmac with sha2_512. Returns a binary array.
hmac_sha2_512(“secret“, “my authenticated message“)
hmac_sha3_256
Calculate an hmac with sha3_256. Returns a binary array.
hmac_sha3_256(“secret“, “my authenticated message“)
hmac_sha3_512
Calculate an hmac with sha3_512. Returns a binary array.
hmac_sha3_512(“secret“, “my authenticated message“)
html_select
Parses an html document and returns the first element that matches the css selector. The return value is a table with textbeing the inner text and attrs being a table of the element’s attributes.
csrf = html_select(html, 'input[name="csrf"]')
token = csrf["attrs"]["value"]
html_select_list
Same as html_select but returns all matches instead of the first one.
html_select_list(html, 'input[name="csrf"]')
http_basic_auth
Sends a GET request with basic auth. Returns true if no WWW-Authenticate header is set and the status code is not 401.
http_basic_auth("https://httpbin.org/basic-auth/foo/buzz", user, password)
http_mksession
Create a session object. This is similar to requests.Session in python-requests and keeps track of cookies.
session = http_mksession()
http_request
Prepares an http request. The first argument is the session reference and cookies from that session are copied into the request. After the request has been sent, the cookies from the response are copied back into the session.
The next arguments are the method, the url and additional options. Please note that you still need to specify an empty table {} even if no options are set. The following options are available:
query– a map of query parameters that should be set on the urlheaders– a map of headers that should be setbasic_auth– configure the basic auth header with{"user, "password"}user_agent– overwrite the default user agent with a stringjson– the request body that should be json encodedform– the request body that should be form encodedbody– the raw request body as string
req = http_request(session, 'POST', 'https://httpbin.org/post', {
json={
user=user,
password=password,
}
})
resp = http_send(req)
if last_err() then return end
if resp["status"] ~= 200 then return "invalid status code" end
http_send
Send the request that has been built with http_request. Returns a table with the following keys:
status– the http status codeheaders– a table of headerstext– the response body as string
json_decode
Decode a Lua value from a json string.
json_decode(“{\”data\”:{\”password\”:\”fizz\”,\”user\”:\”bar\”},\”list\”:[1,3,3,7]}“)
json_encode
Encode a Lua value to a json string. Note that empty tables are encoded to an empty object {} instead of an empty list [].
last_err
Returns nil if no error has been recorded, returns a string otherwise.
if last_err() then return end
ldap_bind
Connect to a LDAP server and try to authenticate with the given user.
ldap_escape
Escape an attribute value in a relative distinguished name.
ldap_escape(user)
ldap_search_bind
Connect to a LDAP server, log into a search user, search for the target user and then try to authenticate with the first DN that was returned by the search.
md5
Hash a byte array with md5 and return the results as bytes.
hex(md5("\x00\xff"))
mysql_connect
Connect to a mysql database and try to authenticate with the provided credentials. Returns a mysql connection on success.
sock = mysql_connect("127.0.0.1", 3306, user, password)
mysql_query
Run a query on a mysql connection. The 3rd parameter is for prepared statements.
Prints the value of a variable. Please note that this bypasses the regular writer and may interfer with the progress bar. Only use this for debugging.
rand
Returns a random u32 with a minimum and maximum constraint. The return value can be greater or equal to the minimum boundary, and always lower than the maximum boundary. This function has not been reviewed for cryptographic security.
rand(0, 256)
randombytes
Generate the specified number of random bytes.
randombytes(16)
sha1
Hash a byte array with sha1 and return the results as bytes.
hex(sha1(“\x00\xff“))
sha2_256
Hash a byte array with sha2_256 and return the results as bytes.
hex(sha2_256(“\x00\xff“))
sha2_512
Hash a byte array with sha2_512 and return the results as bytes.
hex(sha2_512(“\x00\xff“))
sha3_256
Hash a byte array with sha3_256 and return the results as bytes.
hex(sha3_256(“\x00\xff“))
sha3_512
Hash a byte array with sha3_512 and return the results as bytes.
hex(sha3_512(“\x00\xff“))
sleep
Pauses the thread for the specified number of seconds. This is mostly used to debug concurrency.
sleep(3)
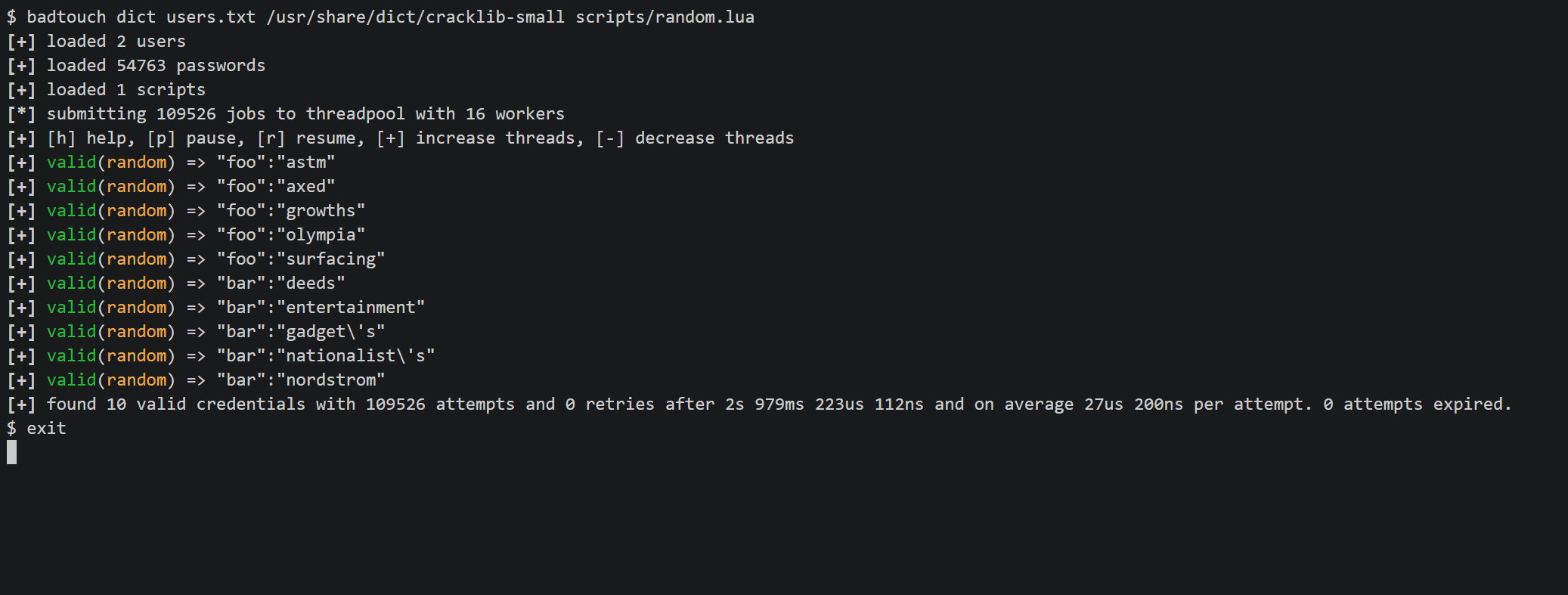
Demo
Copyright (C) kpcyrd
Source: https://github.com/kpcyrd/






