Category: Password Attacks
brutespray Brutespray has been updated to golang. Without needing to rely on other tools this version will be extensible to bruteforce many different services and is way faster than its Python counterpart. Currently, Brutespray...
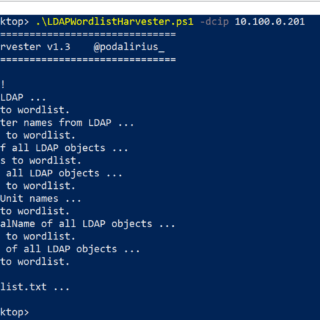
LDAPWordlistHarvester A tool to generate a wordlist from the information present in LDAP, in order to crack non-random passwords of domain accounts. Features The bigger the domain is, the better the wordlist will be....
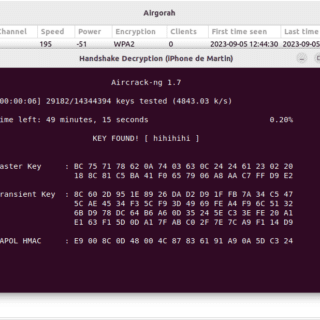
airgorah Airgorah is a WiFi auditing software that can discover the clients connected to an access point, perform deauthentication attacks against specific clients or all the clients connected to it, capture WPA handshakes, and crack...
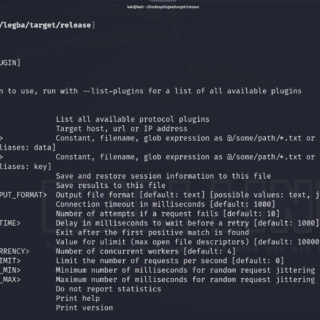
legba Legba is a multiprotocol credentials bruteforcer / password sprayer and enumerator built with Rust and the Tokio asynchronous runtime in order to achieve better performances and stability while consuming fewer resources than similar...
unshackle – Password Bypass Tool Unshackle is an open-source tool to bypass Windows and Linux user passwords from a bootable USB based on Linux. Feature Easy to use Support Windows Simple CLI Support Linux To...
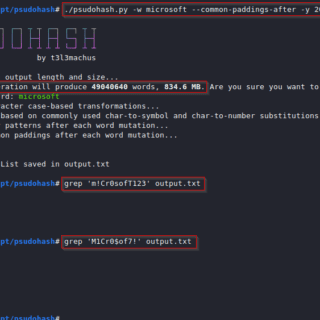
psudohash Psudohash is a password list generator for orchestrating brute force attacks and cracking hashes. It imitates certain password creation patterns commonly used by humans, like substituting a word’s letters with symbols or numbers...
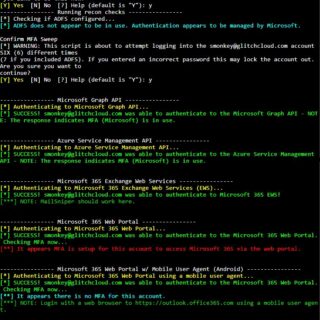
MFASweep MFASweep is a PowerShell script that attempts to log in to various Microsoft services using a provided set of credentials and will attempt to identify if MFA is enabled. Depending on how conditional...
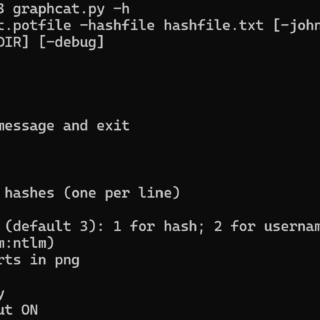
graphcat A simple script to generate graphs and charts on hashcat (and john) potfile and ntds. Install git clone https://github.com/Orange-Cyberdefense/graphcat cd graphcat pip install . Use Graphcat just needs a potfile with -potfile (default is...
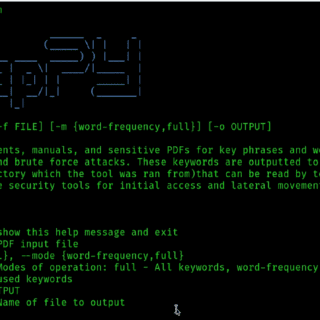
ScrapPY: PDF Scraping Made Easy ScrapPY is a Python utility for scraping manuals, documents, and other sensitive PDFs to generate targeted wordlists that can be utilized by offensive security tools to perform brute force,...
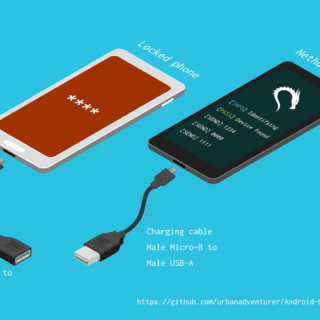
Android-PIN-Bruteforce Unlock an Android phone (or device) by bruteforcing the lockscreen PIN. Turn your Kali Nethunter phone into a bruteforce PIN cracker for Android devices! How it works It uses a USB OTG cable...
ShadowSpray A tool to spray Shadow Credentials across an entire domain in hopes of abusing long-forgotten GenericWrite/GenericAll DACLs over other objects in the domain. Why this tool In a lot of engagements, I see (in...
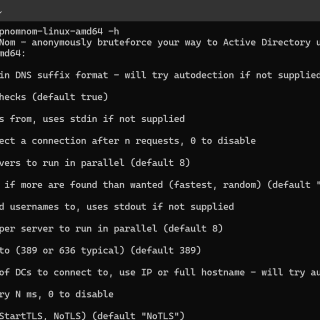
LDAP Nom Nom Anonymously bruteforce Active Directory usernames from Domain Controllers by abusing LDAP Ping requests (cLDAP) Looks for enabled normal user accounts. No Windows audit logs were generated. High-speed ~ up to 10K/sec...
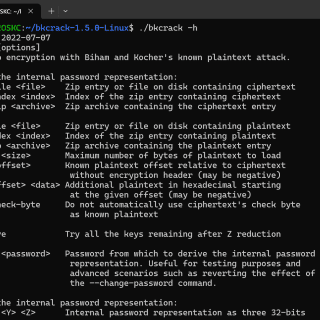
bkcrack Crack legacy zip encryption with Biham and Kocher’s known-plaintext attack. Overview A ZIP archive may contain many entries whose content can be compressed and/or encrypted. In particular, entries can be encrypted with a...
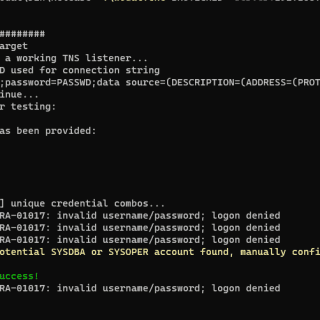
Windows Oracle Database Attack Tool (wodat) Simple port of the popular Oracle Database Attack Tool (ODAT) to C# .Net Framework. Perform password-based attacks e.g. username as password, username list against given password, password list against...
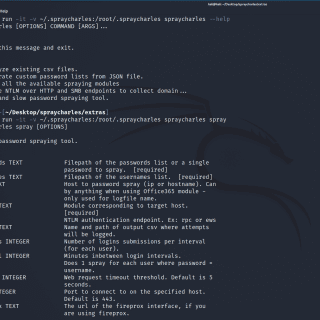
spraycharles Low and slow password spraying tool, designed to spray on an interval over a long period of time. Associated blog post by @sprocket_ed covering NTLM over HTTP, Exchange Web Services, and spraycharles. Usage Config File It...