Security researchers found that an increasing number of malware samples are trying to capitalize on the Meltdown and Specter security vulnerabilities of Intel CPUs.
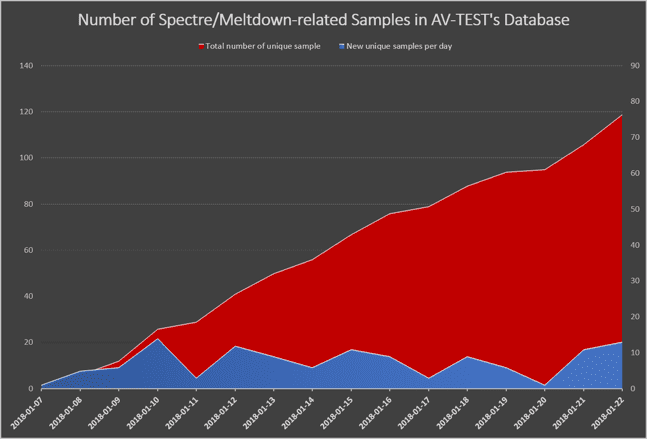
According to experts such as AV-TEST, Fortinet, and Minerva Labs, there are currently public announcements of vulnerabilities related to Meltdown (CVE-2017-5754) and Specter (CVE-2017-5715, CVE-2017-5753) Attack PoC code. Researchers from AV-TEST have now detected 119 malware samples related to the CPU vulnerabilities described above.
Shortly after the release of the PoC code for Meltdown and Specter vulnerabilities, researchers found a number of malware samples related to it at VirusTotal. The report released by Fortinet shows that most of these samples include PoC code or its variants directly.
All of the current evidence shows that most of these samples are intended for trial use by security researchers for PoC code, but experts do not rule out the possibility that some samples may come from genuine malware authors who want to turn PoC code into weaponized malicious tools.
Omri Moyal, co-founder and research vice president at Minerva Labs, said: “I actually haven’t seen real in-the-wild samples yet. Just a lot of PoC/research/tests.”
Meltdown and Specter are serious security vulnerabilities that, once exploited by an attacker, will allow them to gain vast amounts of information from kernel memory space and from other applications. Mozilla has confirmed the concern that attackers will be able to take advantage of Specter vulnerabilities remotely by embedding attack code into common JavaScript files delivered through web pages.
It is now widely accepted that these two vulnerabilities are likely to first appear in the malware mix of state-backed attackers before they are gradually introduced into other exploits and spam emails.
However, considering the large number of new samples that appear daily, one can conclude that research on PoC code is currently underway. In addition, not all samples will be uploaded to VIrusTotal or other malware libraries for testing. This means that professional malware authors may also be using the results of these codes, but most security researchers are still unable to determine exactly what they want to achieve.