Security researchers Ofek Itach and Yakir Kadkoda from Aqua Security’s Team Nautilus uncovered a critical vulnerability in the AWS Cloud Development Kit (CDK) that could lead to a full account takeover. This vulnerability, which affects AWS users deploying infrastructure through CDK, poses a significant risk if certain conditions are met, specifically related to a missing S3 staging bucket.
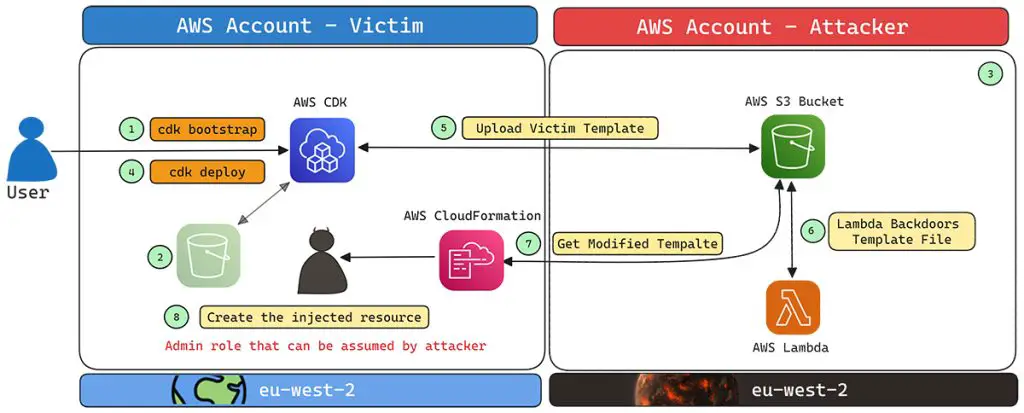
The AWS CDK allows developers to define cloud infrastructure using familiar programming languages, automating the deployment of cloud resources. However, during the bootstrapping process, an S3 bucket is automatically created to store deployment assets. If this bucket is deleted or not created by the user, attackers can exploit the situation by creating a bucket with the same predictable name. This process is known as “S3 bucket namesquatting” or “bucket sniping.”
According to Aqua’s research, “predicting someone else’s CDK staging bucket name only requires knowing their AWS Account-ID and the Region where the CDK was deployed”. With this information, an attacker could claim the missing bucket, enabling a partial denial of service (DoS) or, in more severe cases, manipulating deployment processes.
The real danger arises when a compromised S3 bucket is used to store CloudFormation templates during a CDK deployment. If an attacker controls the staging bucket, they can backdoor these templates, injecting malicious code or adding privileged roles. As noted in the report, “the attacker could add an admin role that they could later assume,” gaining administrative access to the victim’s AWS account.
This potential for an account takeover is particularly severe because the CloudFormationExecutionRole in AWS CDK, which handles the deployment of resources, is assigned administrative privileges by default. This would allow any malicious resource deployed through a backdoored template to have full access to the AWS account.
One key scenario identified by Team Nautilus involves the deletion of the CDK staging S3 bucket. Users may delete this bucket to free up resources or meet account quotas. If the bucket is later recreated by an attacker with the same name, the CDK deploy command would unknowingly push sensitive templates and resources to the attacker’s bucket. The attacker could then inject malicious payloads into these templates, effectively taking over the victim’s AWS account.
Aqua’s research highlighted that “out of 38,560 accounts analyzed, 81 were found to be vulnerable to this attack vector”, with several having multiple buckets exposed across different regions.
After Aqua’s team reported the issue, AWS responded promptly. On July 12, 2024, AWS released a fix in CDK version v2.149.0, ensuring that the FilePublishingRole only trusts S3 buckets within the user’s account. Additionally, AWS notified impacted customers and updated their documentation to encourage the use of custom qualifiers during bootstrapping, which would make bucket names less predictable.
However, users who bootstrapped their environments with CDK v2.148.1 or earlier remain vulnerable unless they take action. “User action is required if you’ve used CDK version v2.148.1 or earlier,” warns the report.
To mitigate this risk, Aqua recommends two immediate actions:
- Upgrade to CDK version v2.149.0 or later and re-run the cdk bootstrap command.
- Alternatively, apply an IAM policy condition to the FilePublishingRole to ensure it only interacts with buckets owned by the user’s account.
Related Posts:
- Openfire Bug (CVE-2023-32315) Exploited to Deploy Kinsing Malware and Cryptominer
- Gafgyt Botnet: Now Exploiting GPU Power in Cloud-Native Environments