AWS Pen-Testing Laboratory
PenTesting laboratory deployed as IaC with Terraform on AWS. It deploys a Kali Linux instance accessible via ssh & wireguard VPN. Vulnerable instances in a private subnet.
NOTE:
- Ids only defined for region “eu-west-1”
- For other regions, kali ami id must be specified and metasploitable3 id (after building it)
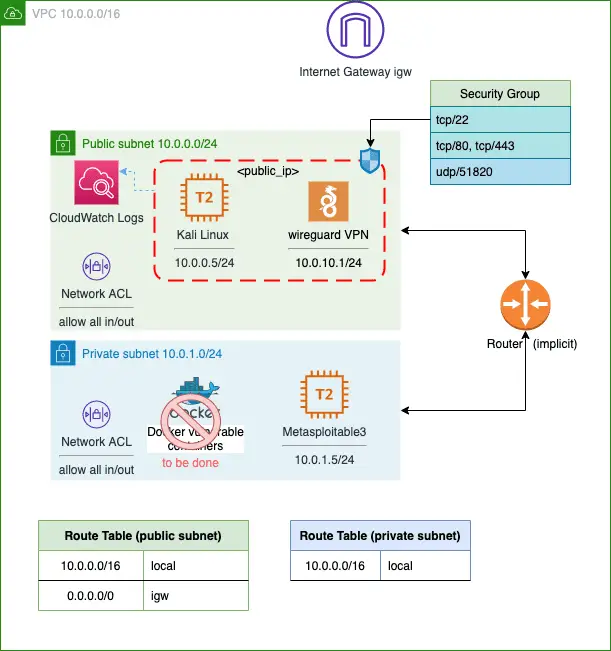
Diagram
Components
- Kali instance (the private key is saved into kali.pem)
- Wireguard VPN service: client file client_vpn.wg
- Accessible via ssh/scp
- Public Subnet 10.0.0.5/24
- Infection Monkey running on port 5000 (only accessible via vpn or ssh)
- Vulnerable machine “Metasploitable” (ami build is public)
- Private subnet 10.0.1.5/24
- More vulnerable labs/machines/docker (to-be-done)
Features added
- User management
- Automatically create nonprivileged users in kali instance with rsa
- Wireguard VPN client file per user
- Command-line audit logging in syslog
- auditd enabled with sudo_log and users_log keys for auditing user actions (see also ausearch command)
- ToDO: Forward terminal audit to CloudWatch or an S3 Bucket with write-once policy
Changelog
- [2021-12-26]
- set automatically first availability zone
- new metasploitable ami’s created with packer
- initial integration of log4jshell vulnerability to metasploitable3 machine (but it is not usable)
Instal & Use
Copyright (c) 2021, juanjoSanz
All rights reserved.