aws-security-benchmark: CIS Amazon Web Services Foundations Benchmark 1.1
aws-security-benchmark
create-benchmark-rules.yaml is an AWS CloudFormation template for establishing CIS AWS 1.1 benchmark governance rules (download the benchmarks here).
cis-benchmark-matrix.xlsx is a spreadsheet that maps the CIS Amazon Web Services Foundations benchmarks to the specific security controls provisioned in the CloudFormation template.
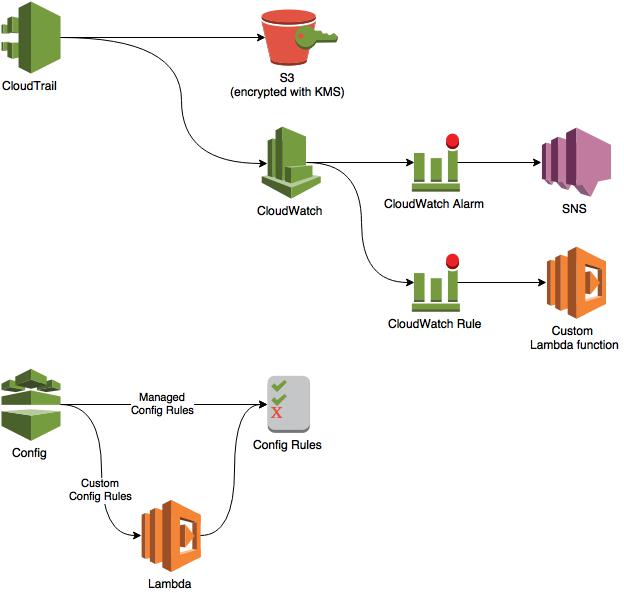
The AWS services used for these benchmarks are used in the following relationship:

The following preconditions must be met before the stack can be launched:
- AWS Config must be running in the region where this template will be run. This is needed for Config Rules.
- Amazon CloudTrail must be delivering logs to CloudWatch Logs. This is needed for CloudWatch metrics and alarms.
- AWS Lambda must be supported in the region where this template will be launched. See this page for region support.
The controls are a combination of AWS Config Rules (both AWS-managed and custom), Amazon CloudWatch rules, and Amazon CloudWatch alarms. Please note that these resources will incur costs in your account; please refer to the pricing model for each service.
For example, an estimate in us-east-1:
- Config Rules: 17 rules @ $2.00/rule/month = $34.00/month
- CloudWatch Alarms: 6 alarms @ $0.10/alarm/month = $0.60/month
- CloudWatch Metrics: 6 metrics @ $0.30/metric/month = $1.80/month
- CloudWatch Logs: 17 logs @ $0.50/GB ingested = based on usage
- Lambda: variable (first 1 million requests per month are free)
aws-cis-foundation-benchmark-checklist
Script to evaluate your AWS account against the full CIS Amazon Web Services Foundations Benchmark 1.1
The script have a number of different outputs, all optional by changing the settings inside the script.
All outputs will generate a single report of all supported controls in short format, full JSON or HTML.
Delivery of the report is console output for JSON structure, S3 SignedURL for HTML file and optional publish to SNS for the S3 SignedURL if you wish to receive an email or trigger other functions any time a new report is done.
You can also store the reports in a central S3 bucket if you run this for multiple accounts
Config Rules
By adding the script to your AWS account as a Lambda function you can tie it to a Config Rule.
You don’t need to change or enable anything in the script when using with Config Rule, the script will autosense it and automatically start reporting compliance status at the account level.
The script will also report back a short-form version of the result using the annotation field. You can see this value using the Config API:
aws configservice get-compliance-details-by-config-rule –config-rule-name
Keep in mind that the lambda function needs to have timeout set to max time.
Local execution
You can also run this script from an admin console using python and AWS SDK.
It will use the credentials you have stored in your profiles.
Run without parameters to use default profile:’)
python aws-cis-foundation-benchmark-checklist.py
Specify profile by using the -p or –profile
python aws-cis-foundation-benchmark-checklist.py [-p|–profile] <profile>
IAM Policy
The IAM policy required to run the script is located in the file
aws-cis-foundation-benchmark-checklist-lambdarole.json





