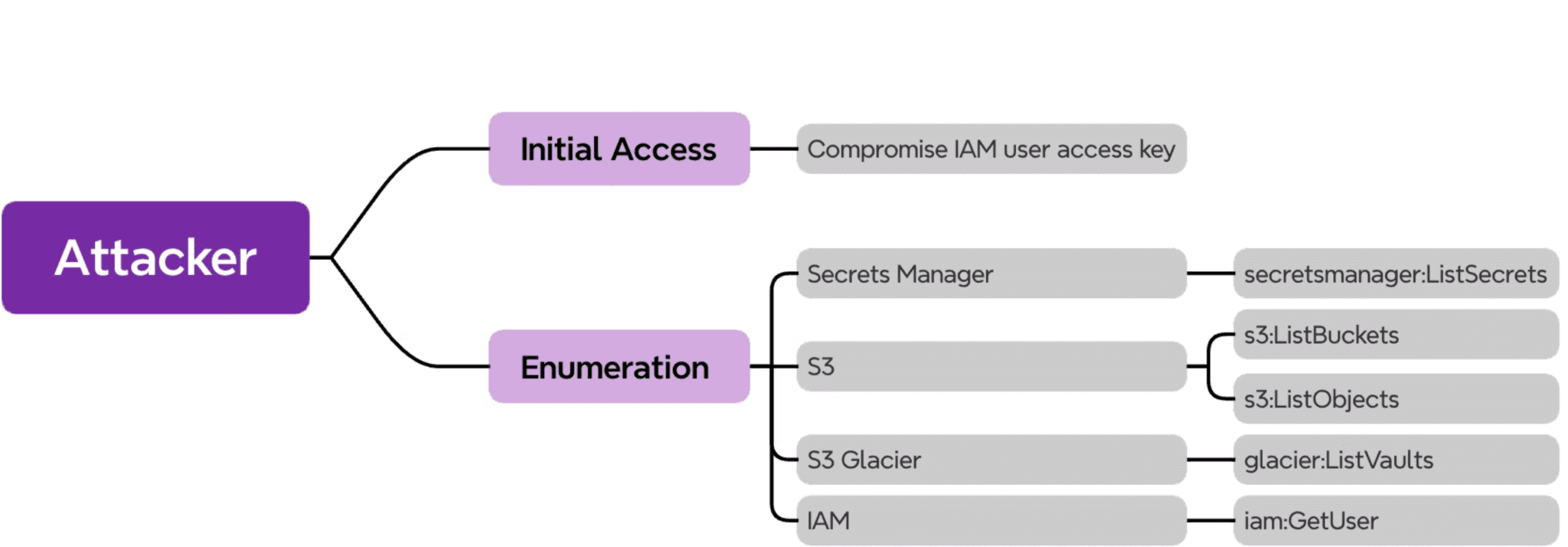
DataDog Security Labs has uncovered a concerning campaign targeting Amazon Web Services (AWS) environments, revealing a new wave of malicious activity aimed at compromising valuable cloud resources. The attackers are employing a multi-pronged approach, focusing their efforts on enumerating and potentially exfiltrating data from AWS Secrets Manager, S3 buckets, and even the relatively untapped S3 Glacier vaults.
This campaign, observed between May 23rd and 27th, 2024, highlights the persistent and evolving nature of cyber threats targeting cloud infrastructure. The attackers’ use of leaked access keys, residential proxies, and the Cloudflare WARP VPN to mask their activities underscores their sophistication and determination.
What sets this campaign apart is the unusual user agent employed by the attackers, indicating that they manually sign their AWS API requests using the Python library requests-auth-aws-sigv4. This deviation from typical automated attack patterns raises suspicions and could serve as a valuable indicator for detecting similar malicious activity.
While DataDog’s research did not observe successful data exfiltration attempts, the widespread enumeration of AWS resources suggests a calculated and potentially large-scale operation. The attackers may be assessing the value of available data before initiating exfiltration or testing the level of access they possess for potential resale in underground markets.
The inclusion of S3 Glacier vaults in this campaign represents a notable shift in attacker tactics. Traditionally, S3 buckets have been the primary target, but the focus on Glacier vaults, often used for backup storage, demonstrates the attackers’ expanding reach and their willingness to explore less conventional avenues for potential exploitation.
DataDog’s report provides valuable insights into the tactics, techniques, and procedures (TTPs) employed in this campaign, offering organizations crucial information to bolster their AWS security posture. By monitoring for the indicators of compromise (IOCs) outlined in the report and implementing proactive security measures, organizations can mitigate the risk of falling victim to similar attacks.
Identifying and mitigating such sophisticated attacks requires a multifaceted approach:
- Indicators of Compromise (IoCs): Utilize the provided IoCs to detect this specific campaign. Enrich IP addresses for the WARP client if Cloudflare API calls are expected.
- API Call Monitoring: Monitor
ListSecretandListVaultAPI calls across multiple regions within short timeframes. The attackers executed these API calls across 17 regions in under a minute, which can serve as a detection marker. - Access Denied Error Spikes: Look for unusual spikes in
AccessDeniederrors for API calls likeListSecrets,ListBuckets, andListObjects. This could indicate attempted unauthorized access by attackers.
As the cyber threat landscape continues to evolve, the targeting of AWS resources emphasizes the importance of robust cloud security practices. Organizations must remain vigilant, adopt a defense-in-depth approach, and leverage threat intelligence to stay ahead of emerging threats and protect their valuable cloud assets.