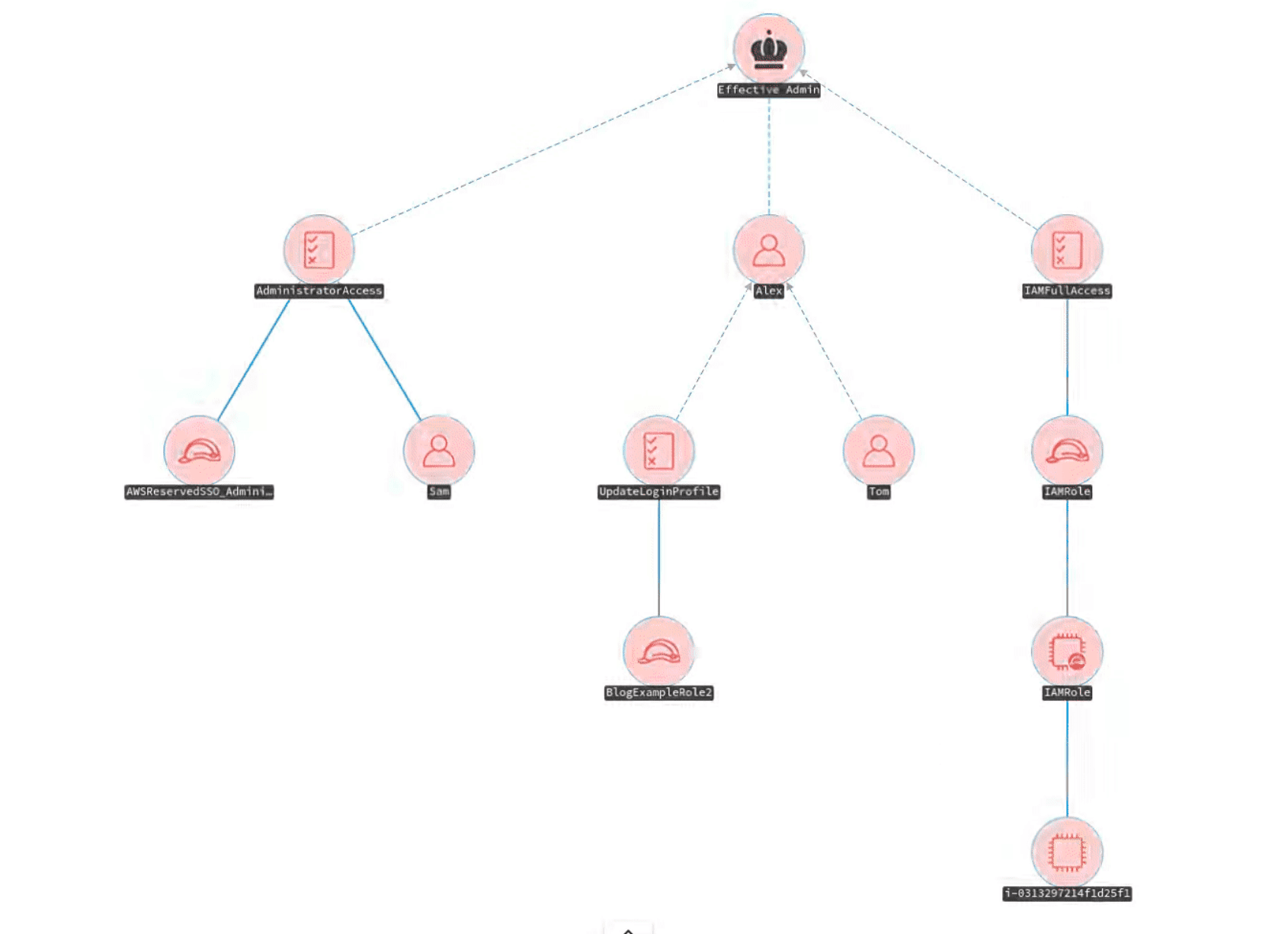
awspx
awspx is a graph-based tool for visualizing effective access and resource relationships within AWS. It resolves policy information to determine what actions affect which resources while taking into account how these actions may be combined to produce attack paths. Unlike tools like Bloodhound, awspx requires permissions to function — it is not expected to be useful in cases where these privileges have not been granted.
Changelog v1.3.4
Bug Fixes
- Fixes inoperable UI redact
selection
- Fixes UI database URI generation issue with non-standard ports
- Fixes UI search highlighting
- Fixes
profile --createcreation bug - Fixes unhandled IllegalLocationConstraintException and UnauthorizedOperation ingestion exceptions
- Fixes unhandled error when EC2 instance user data is unavailable (thanks @bytebutcher)
- Fixes inability to load multiline CSV data
- Fixes erroneous non-dependent source node attack exclusion
- Fixes Grants and CreateAction attack definition option interoperability
- Fixes attack computation off-by-one logic error
- Fixes ignored action conditions in attack definition Cypher values
- Fixes discovered attacks tally
- Fixes inadvertent Generic Policy deletion
- Fixes console message style overlap
Improvements
- Upgrades Neo4j from 3.5.13 to 4.3.2
- Adds Neo4j APOC support
- Updates Ingestor resource model logic
- Adds NatGateway EC2 ingestion support
- Adds EC2 PlacementGroup Instance associations
- Removes redundant RouteTable associations
- Adds explicit Admin relationship to all resources
- Adds UI search re-add and resource selection functionality
- Adds UI tag-based resource searching
- Adds UI PermissionsBoundary property resolution and edge stylization
- Updates dynamic graph stylization
- Adds AffectsGeneric attack definition option
- Adds ordering by
--only-attacksif specified - Adds support for list-based attack definition Descriptions
- Standardizes CreatePolicy attack logic
- Adds caching logic for attack definition translation
- Removes profile notice from
--verbose - Adds console tasklist support for function-based wait and done parameters
- Adds UI search visibility toggling using Ctrl + s
Other Changes
- Defaults ingestion to
--verbose(graphical output replaced with--pretty) - Updates UI graph defaults to display unknown nodes and edges
- Updates attack placeholder syntax from
${A}.Bto${A.B} - Updates attack pruning to remove patterns with outdegree 0
- Updates UI path searching to incorporate weight (deprecates some attack pruning logic)
- Removes Domain principal exclusion
- Removes legacy Grants option from CreateRole attack definition
- Removes User Depends from CreateGroup attack definition
- Updates attack definition placeholder regex
- Updates the ARN for Effective Admin
- Updates the hotkey for running an advanced query to Ctrl + enter
- Fixes spelling mistake in
cli.py(thanks @dmyates)
Install
awspx requires Docker.
git clone git@github.com:FSecureLABS/awspx.git
cd awspx && ./INSTALL
Use
awspx ingest
Browse to the local host and enjoy it!

Things to check
- SELinux may prevent the docker container from doing everything it needs to.
- As part of setting up, the docker container will add iptables rules. You may need to adjust your iptables configuration to get awspx to work.
- The docker container runs a Neo4j database and will forward the TCP ports 7687, 7373 and 7474 to the same ports on the host system. This will conflict with an existing Neo4j installation on the host (e.g. BloodHound) and you will need to disable that before running awspx.
- The docker container also forwards to TCP port 80.
AWS permissions
The following AWS-managed policies can be used.
- SecurityAudit will allow you to ingest everything except S3 objects.
- Add ReadOnlyAccess to also ingest S3 objects (warning: this can be very slow).
Data collection
Once awspx has been installed, the ingestor can be invoked by running awspx on the command line. You can then create a profile by running:
awspx profile --create profilename
This command will use aws configure to prompt you for your AWS access key ID and secret. Once that is set up, you can run the ingestor with this command:
awspx ingest --profile profilename
Further commands and arguments are provided for tweaking ingestion and attack path computation, and for managing AWS profiles and Neo4j databases. Run awspx -h and awspx {profile|ingest|attacks|db} -h to learn more.
Supported services: IAM, EC2, S3, Lambda
Examples
awspx ingest --profile my-account --services EC2
The ingestor will pull only IAM and EC2 data using the my-account profile and store it in a database named my-account.db.
awspx ingest --profile my-account --services S3 --database db-for-s3
The ingestor will pull only IAM and S3 data using the my-account profile and store it in a database named db-for-s3.db.
awspx ingest –profile my-account –except-types AWS::S3::Object \ –except-arns arn:aws:s3:::broken-bucket,arn:aws:ec2:eu-west-1:123456789012:instance/i-1234
awspx will pull data for all supported services using the my-account profile, but will not attempt to load S3 objects, and will also not load the bucket named broken-bucket or the EC2 instance named i-1234. A full list of recognized resource types can be found in lib/aws/resources.py.
awspx ingest --profile my-account --skip-attacks
awspx will pull data for all supported services using the my-account profile but will not compute attacks. This can be useful for large environments. Attacks can be computed separately later on by running awspx attacks.
awspx attacks --only-attacks AssumeRole,CreateGroup
Using the current database, awspx will only compute only the Assume Role and Create Group attacks.
awspx db --load-zip sample.zip
awspx will create a new database named sample from the CSVs in the provided ZIP file. Files must be placed in /opt/awspx/data so that they can be accessed by the docker container.
awspx db --use my-other-account
awspx will switch to displaying the specified database.
awspx is a graph-based tool for visualizing effective access and resource relationships in AWS environments. (C) 2018-2019 F-SECURE CYBER SECURITY LIMITED.
Source: https://github.com/FSecureLABS/