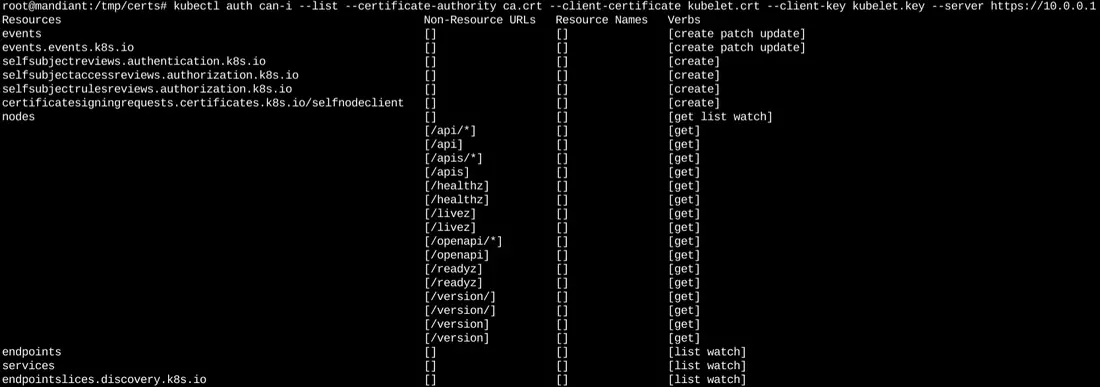
Permissions granted to the embedded TLS certificates
A newly discovered vulnerability in Azure Kubernetes Services (AKS) has been revealed by Mandiant, a leading cybersecurity firm. The vulnerability, dubbed “WireServing,” could have allowed attackers to escalate privileges within a compromised cluster and gain unauthorized access to sensitive credentials.
Kubernetes, the popular container orchestration platform, is known for its complexity and the challenges associated with securing it. The vulnerability, uncovered in AKS clusters using the “Azure CNI” for network configuration and “Azure” for network policy, exploited a gap in the cluster’s security that allowed attackers to perform a TLS bootstrap attack. This attack granted unauthorized access to sensitive data, including secrets stored within the cluster.
The attack did not require the Pod to be running with elevated privileges or host networking enabled, making it a significant threat in environments where Pods are routinely deployed without strict security controls.
The attack exploited a weakness in the way AKS clusters handled TLS bootstrap tokens—critical components used to securely join a node to a Kubernetes cluster. By executing commands within a compromised Pod, an attacker could download the configuration files used to provision the cluster node. These files contained the TLS bootstrap tokens and other credentials, which the attacker could then use to escalate privileges and access sensitive information across the cluster.
The attack was particularly dangerous because it bypassed several of the typical security controls in place within Kubernetes environments. Even without root access or host networking privileges, the attacker could access the Kubernetes API, list all nodes in the cluster, and read secrets associated with workloads running on those nodes.
A key element of this attack involved Azure WireServer, an undocumented Azure component, and its associated HostGAPlugin. These tools, typically used for provisioning and managing Azure VMs, were found to be vulnerable to exploitation. By accessing these services, the attacker could retrieve and decrypt sensitive configuration settings, including the TLS bootstrap tokens needed to perform the attack.
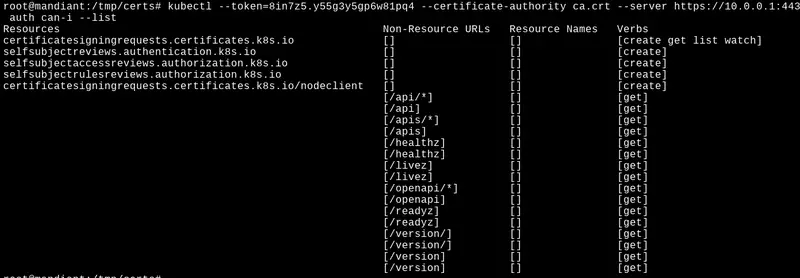
The process involved requesting a decryption key from the WireServer, which was then used to decrypt the settings provided by HostGAPlugin. This revealed the provisioning script for the Kubernetes nodes, which contained the necessary credentials for escalating privileges within the cluster.
The implications of this vulnerability are far-reaching. Attackers who successfully exploited this issue could have gained access to sensitive information, leading to data theft, financial losses, and potentially catastrophic damage to the affected organizations’ reputations. The ability to escalate privileges within a Kubernetes cluster opens the door to a wide range of malicious activities, from unauthorized access to critical data to full-blown ransomware attacks.
The vulnerability also highlights the risks associated with cloud environments where complex configurations and undocumented services can create unexpected security gaps. The attack demonstrated that even well-secured environments could be vulnerable if certain services are not properly protected.
Upon receiving the report from Mandiant, Microsoft quickly moved to address the issue. The patch involved updating the way AKS clusters handle TLS bootstrap tokens, ensuring that these credentials could no longer be exploited in the manner described. Specifically, the patch prevents unauthorized access to the metadata server and blocks the exploitation of TLS bootstrap tokens.