AzureHunter
A Powershell module to run threat hunting playbooks on data from Azure and O365 for Cloud Forensics purposes.
What is the UnifiedAuditLog?
The unified audit log contains user, group, application, domain, and directory activities performed in the Microsoft 365 admin center or in the Azure management portal. For a complete list of Azure AD events, see the list of RecordTypes.
The UnifiedAuditLog is a great source of cloud forensic information since it contains a wealth of data on multiple types of cloud operations like ExchangeItems, SharePoint, Azure AD, OneDrive, Data Governance, Data Loss Prevention, Windows Defender Alerts and Quarantine events, Threat intelligence events in Microsoft Defender for Office 365 and the list goes on and on!
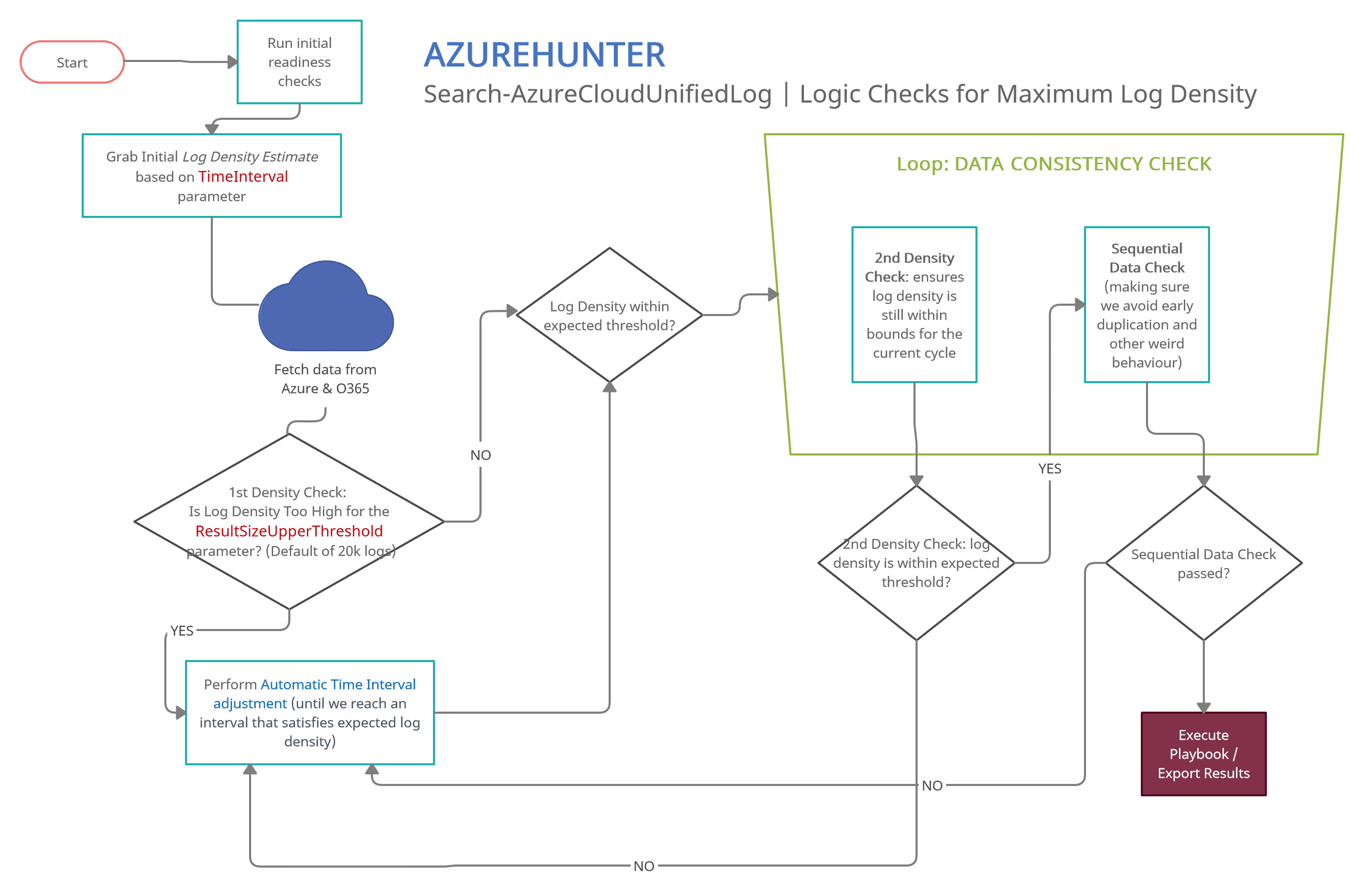
AzureHunter Data Consistency Checks
AzureHunter implements some useful logic to ensure that the highest log density is mined and exported from Azure & O365 Audit Logs. In order to do this, we run two different operations for each cycle (batch):
- Automatic Window Time Reduction: this check ensures that the time interval is reduced to the optimal interval based on the ResultSizeUpperThreshold parameter which by default is 20k. This means, if the amount of logs returned within your designated TimeInterval is higher than ResultSizeUpperThreshold, then an automatic adjustment will take place.
- Sequential Data Check: is returned Record Indexes sequentially valid?

AzureHunter has two main commands: Search-AzureCloudUnifiedLog and Invoke-HuntAzureAuditLogs.
The purpose of Search-AzureCloudUnifiedLog is to implement complex logic to ensure that the highest percentage of UnifiedAuditLog records are mined from Azure. By default, it will export extracted and deduplicated records to a CSV file.
The purpose of Invoke-HuntAzureAuditLogs is to provide a flexible interface into hunting playbooks stored in the playbooks folder. These playbooks are designed so that anyone can contribute with their own analytics and ideas. So far, only two very simple playbooks have been developed: AzHunter.Playbook.Exporter and AzHunter.Playbook.LogonAnalyser. The Exporter takes care of exporting records after applying de-duplication and sorting operations to the data. The LogonAnalyser is in beta mode and extracts events where the Operations property is UserLoggedIn. It is an example of what can be done with the playbooks and how easy it is to construct one.
When running Search-AzureCloudUnifiedLog, you can pass in a list of playbooks to run per log batch. Search-AzureCloudUnifiedLog will pass on the batch to the playbooks via Invoke-HuntAzureAuditLogs.
Finally, Invoke-HuntAzureAuditLogs can be used standalone. If you have an export of UnifiedAuditLog records, you can load them into a Powershell Array and pass them on to this command and specify the relevant playbooks.
Changelog v1.6
* Introduced Sylvan.Data.Csv .NET library for blazing fast processing of CSV files (only applied to one playbook so far)
* Added new Playbook AzHunter.Playbook.eDisco.SummaryReportCleaner to process Azure eDisco Summary Reports
* Added new Playbook AzHunter.Playbook.UAL.RecordTypeExporter to break down UAL logs into its individual RecordTypes to facilitate DFIR analysis
* Renamed Invoke-HuntAzureAuditLogs.ps1 to Invoke-AzHunterPlaybook.ps1 for better consistency
* Now you can pass in Playbook Parameters to a particular playbook using the “PlayBookParameters” parameter in Invoke-AzHunterPlaybook
Install
Copyright (c) 2017 Diego Perez (@darkquassar)