Image: GDATA
In a recent discovery, cybersecurity researchers have unveiled a sophisticated new backdoor, dubbed “BadSpace,” that poses a significant threat to internet users. First brought to the community’s attention by threat intelligence analyst Gi7w0rm on May 19, this backdoor was initially discovered by the researcher @kevross33. The cybersecurity firm G DATA has provided an in-depth analysis of the infection chain and functionality of this backdoor, revealing a multi-stage attack that involves several high-ranking infected websites.
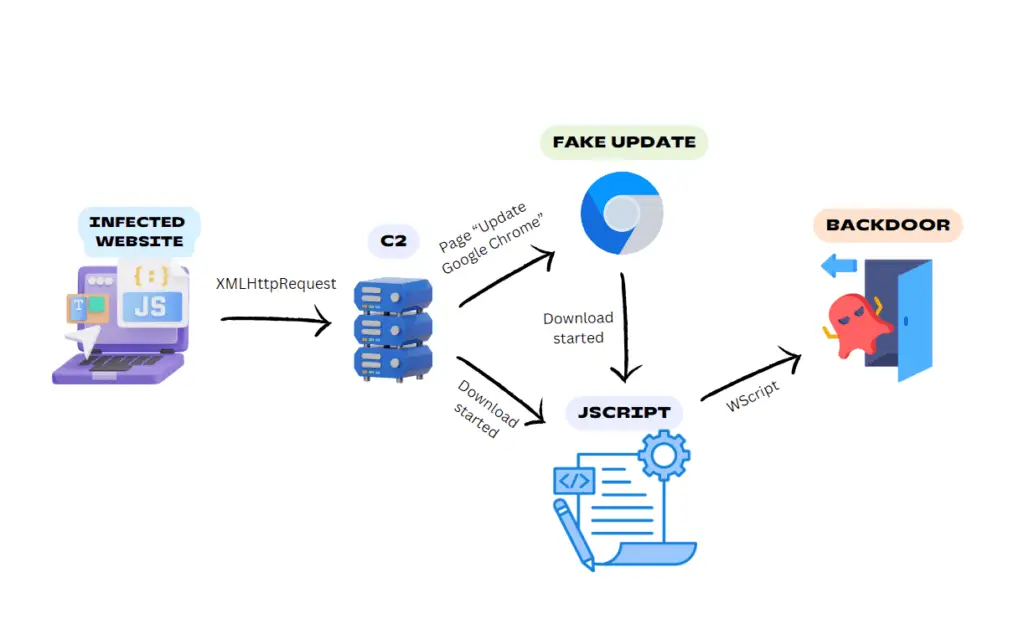
BadSpace is delivered through a complex infection chain, starting with infected websites. The malicious campaign begins by setting a cookie to track if a user has visited the site before. On a first visit, the website constructs a URL with various query parameters including device type, IP address, referrer, user agent, domain, and location. This URL sends a GET request, and the response payload can overwrite the initial webpage, unless it returns an error message.
The threat actor behind BadSpace predominantly targets WordPress websites, injecting malicious code into JavaScript libraries like jQuery or directly into the index page. G DATA researchers acquired several JScript files that drop and run the BadSpace backdoor, often using extension spoofing such as “.pdf.js” to disguise the payload.
A notable aspect of the BadSpace campaign involves fake Google Chrome update prompts. When users download the supposed update, it installs either the malicious backdoor directly or a JScript file that facilitates the download. The domains serving as Command and Control (C2) servers have been linked to the threat actor SocGholish, known for using similar techniques in past campaigns.
The JScript downloader uses various obfuscation techniques to evade detection. It starts with three functions and an array of strings to obscure its operations. The functions perform multiple shifts and subtractions to generate new arrays that replace obfuscated variable and function names. Additionally, the script uses JavaScript Compressor by Dean Edwards to obfuscate a final function that constructs a PowerShell downloader. This downloader silently downloads the BadSpace backdoor and executes it using rundll32.exe.
The BadSpace backdoor is a PE32+ DLL that, although not packed, is heavily obfuscated. It encrypts strings, Windows API DLL names, and function names using RC4. The backdoor dynamically resolves APIs via LoadLibraryW and GetProcAddress, using decrypted function names from its strings table. G DATA created an IDA Python script to automatically decode these strings and APIs within the IDA database, streamlining the analysis process.
BadSpace employs several anti-sandbox techniques to avoid detection. It counts the number of folders in %TEMP% and %APPDATA%, checks registry entries, and monitors system specifications such as the number of processors and global memory status. Upon passing these checks, it creates a unique mutex and establishes persistence via scheduled tasks, using rundll32.exe to execute the backdoor.
The backdoor’s initial C2 communication involves sending a cookie containing encrypted system information. This cookie, likely the source of its alias “WarmCookie,” includes data such as the computer name, DNS domain, OS version, and username. Communication with the C2 server is encrypted using a hardcoded RC4 key unique to each sample. The backdoor uses a modified user agent for these communications, which features extra spaces that inspired the name BadSpace.
As cyber threats continue to evolve, it’s important to stay informed about the latest malware and attack techniques.