Fake unlocking UI | Image: Zimperium
Aazim Yaswant, a Malware Analyst at Zimperium, has published a comprehensive analysis of the latest TrickMo samples, revealing alarming new capabilities in this banking trojan. Originally disclosed by Cleafy in early September, this new variant of TrickMo employs techniques designed to evade detection and analysis, including obfuscation and zip file manipulation. Yaswant’s team identified a staggering 40 variants of TrickMo, consisting of 16 droppers and 22 active Command and Control (C2) servers, many of which remain undetected by the broader security community.
While TrickMo’s core capabilities remain focused on banking credential theft, Yaswant’s analysis uncovered more advanced functionalities. “These capabilities enable the malware to effectively access any type of information stored on the device,” Yaswant explains. This includes OTP interception, screen recording, remote control, data exfiltration, and abuse of accessibility services to automatically grant permissions and execute actions without user consent. Moreover, TrickMo can display deceptive overlays to steal credentials and facilitate unauthorized financial transactions.
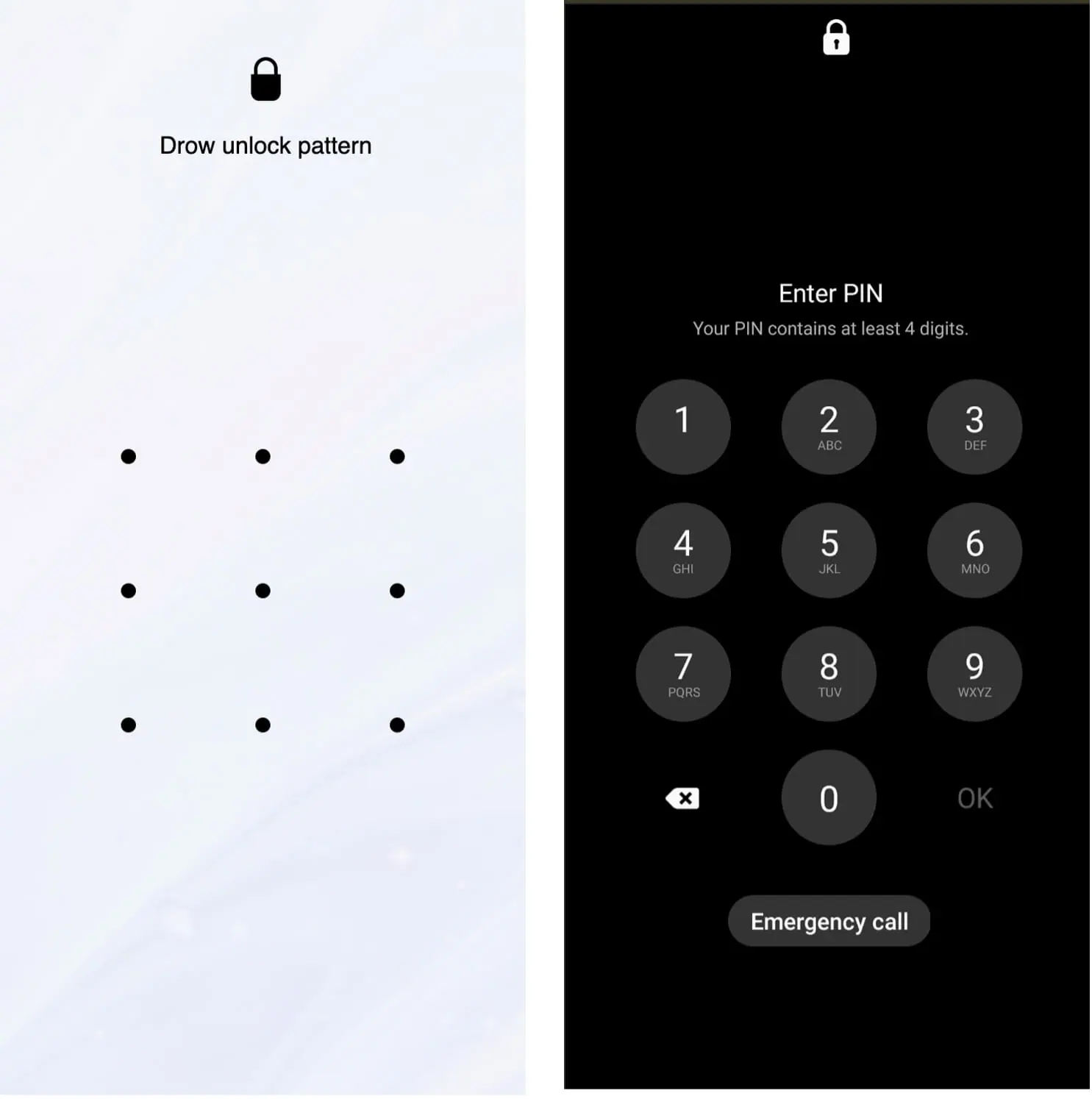
One of the more concerning findings in Yaswant’s analysis is a newly discovered feature in some of the TrickMo variants: the ability to steal the device’s unlock pattern or PIN. This functionality allows attackers to bypass the lock screen and operate on the device even while it is secured. The malware achieves this by displaying a deceptive user interface that mimics the legitimate unlock screen. “When the user enters their unlock pattern or PIN, the page transmits the captured PIN or pattern details, along with a unique device identifier,” Yaswant notes.
Zimperium’s team was able to gain access to several C2 servers, discovering approximately 13,000 unique IP addresses linked to victims of the malware. The analysis revealed that TrickMo primarily targets regions such as Canada, the United Arab Emirates, Turkey, and Germany. Yaswant’s investigation uncovered millions of compromised records, with the stolen credentials extending beyond banking information to include access to corporate VPNs and internal websites. This underscores the critical risk posed to organizations, as compromised mobile devices can serve as entry points for larger cyberattacks.
Related Posts:
- Beware the New TrickMo Banking Trojan: Enhanced Features, Increased Danger
- Attacker use DDoS attack to hit three major Dutch banks
- Stealthy New Android Trojan Disguised as Popular Apps Steals Your Data