Hackers are exploiting 0-day baseStriker vulnerability in Office 365

On May 1st, Avanan researchers discovered a 0-day vulnerability called baseStriker in Office 365. An attacker can use this vulnerability to send malicious emails, bypassing Office 365’s account security mechanism.
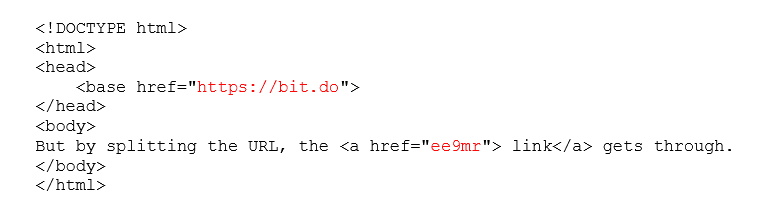
The code for the baseStriker exploit uses the less commonly <base> HTML tag to create a base URL for relative links.
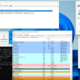
| I am using: | Am I Vulnerable to baseStriker? |
| Office 365 | Yes – you are vulnerable |
| Office 365 with ATP and Safelinks | Yes – you are vulnerable |
| Office 365 with Proofpoint MTA | Yes – you are vulnerable |
| Office 365 with Mimecast MTA | No – you are safe |
| Gmail | No – you are safe |
| Gmail with Proofpoint MTA | We are still in testing and will be updated soon |
| Gmail with Mimecast MTA | No – you are safe |
| Other configurations not here? | Contact us if you want us to help you test it |
Only a week after the exposure of the baseStriker vulnerability, researchers have discovered relevant examples of use in the wild. Hackers use this vulnerability to send phishing attacks and distribute ransomware, malware, and other malicious content. Avanan has contacted Microsoft and reported the findings, but Microsoft has not yet given feedback.
Source: bleepingcomputer