Bashark: Bash post exploitation toolkit
Bashark
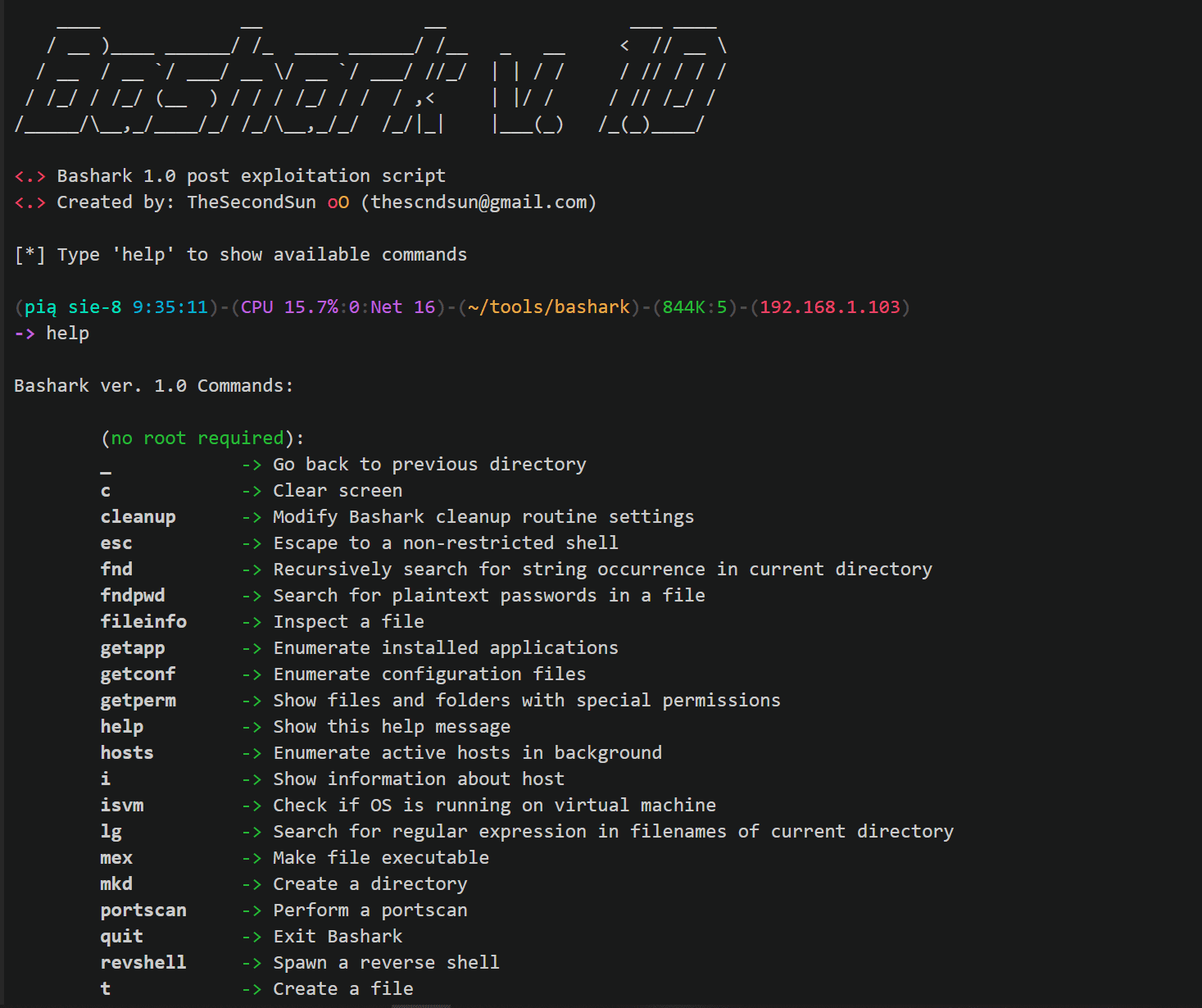
Bashark aids pentesters and security researchers during the post-exploitation phase of security audits.
Features
- Single Bash script
- Lightweight and fast
- Multi-platform: Unix, OSX, Solaris etc.
- No external dependencies
- Immune to heuristic and behavioral analysis
- Built-in aliases of often used shell commands
- Extends system shell with post-exploitation oriented functionalities
- Stealthy, with custom cleanup routine activated on exit
- Easily extensible (add new commands by creating Bash functions)
- Full tab completion
Download
git clone https://github.com/TheSecondSun/Bashark.git
Use
To launch Bashark on the compromised host, simply source the bashark.sh script from a terminal:
$ source bashark.sh
Then type help to see the help menu

Copyright (c) 2018 Jakub Lutczyn
Source: https://github.com/TheSecondSun/