Beware: Malware Disguised as CPU-Z on Fake Windows News Site
Recently, researchers at Malwarebytes Labs have unearthed a sophisticated campaign aimed at distributing malware through a counterfeit Windows news site. This cloned portal, masquerading as the legitimate WindowsReport.com, is ensnaring users with a tainted version of the esteemed CPU-Z utility.
These cyber swindlers aren’t playing small; their net is cast wide, with other reputable utilities like Notepad++, Citrix, and VNC Viewer also in their crosshairs. The mimicry is so convincing that even the discerning eyes of geeks and system administrators, the usual patrons of such news portals, could be fooled.
The alarm was raised when the malefactors replicated Windows Report, a credible source for tech enthusiasts to snag the latest software utilities. The legitimate site remains uncompromised, but that hasn’t stopped these imposters from using its likeness as bait.
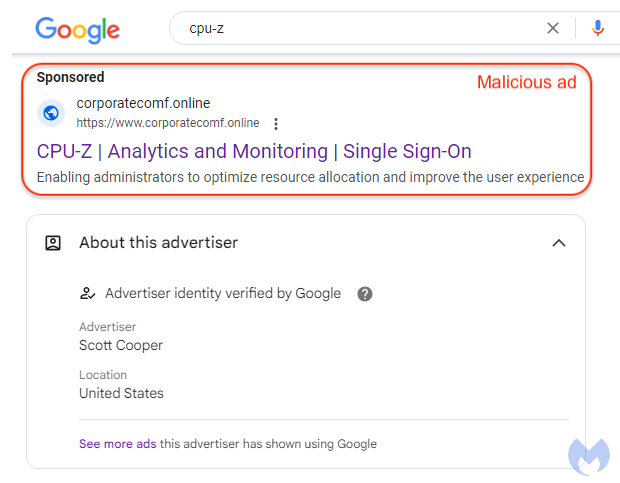
The trickery extends to the advertisement itself, supposedly from one ‘Scott Cooper’, a name that reeks of compromise or outright fabrication. The ad, designed to attract Windows aficionados seeking the CPU-Z tool, is a trapdoor to malware.

When a victim takes the bait, clicking the ad, they’re whisked away—not to enlightenment, but to a duplicitous domain. There, the familiar facade of Windows Report awaits, but with one fatal flaw—the download on offer is a malicious wolf in sheep’s clothing, a digitally signed MSIX installer laden with a treacherous PowerShell script.
Malwarebytes’ defense mechanisms are in full swing, blocking the associated malvertising domains and bolstering their arsenal against these new threats. Yet, the real kicker lies in the payload’s disguise—an MSI installer, bearing a digital signature to hoodwink both operating systems and antivirus defenses alike.
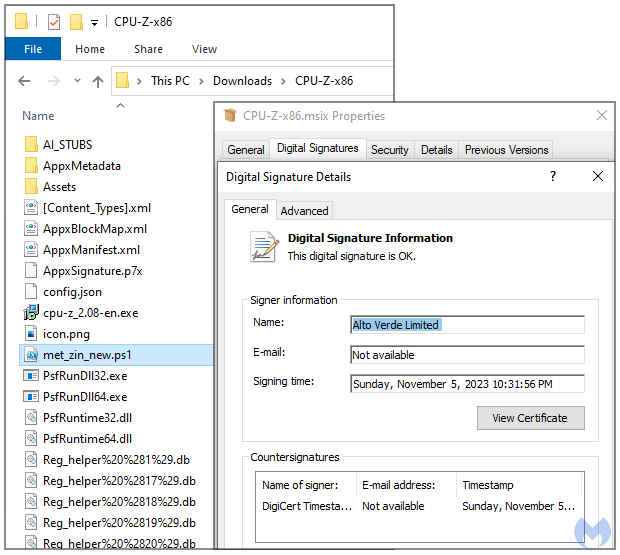
“The download is also a signed MSI installer, which increases the chances for it to look legitimate from the operating system and antivirus software. These MSI loaders are quite common and allow threat actors to update the final payload by simply swapping a PowerShell script,” the researcher wrote.
This incident serves as a sobering reminder of the guile of online criminals. They’ve upped the ante in the software download arena, skillfully weaving deception to serve their malware masterpieces. It’s a cautionary tale for the enterprise realm, where a file’s checksum might be the thin line between safety and compromise.





