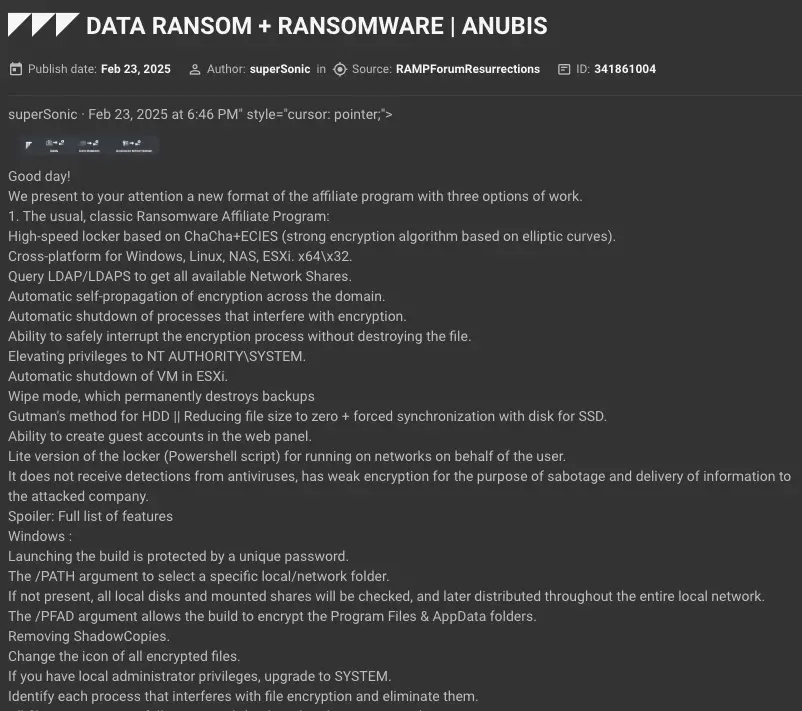
A post showing part of Anubis’s ransomware capabilities (source: KELA platform)
A new ransomware group, dubbed Anubis, has emerged, deploying double extortion tactics and operating under a ransomware-as-a-service (RaaS) model. According to a report from KELA, the group has been active since at least November 2024, with their presence observed on RAMP and XSS cybercrime forums.
Anubis first gained attention when a victim reported a cybersecurity incident on November 13, 2024, indicating that the group had already been conducting attacks before their official emergence in December. Since then, Anubis has expanded its operations, offering multiple affiliate programs to cybercriminals, including:
- Anubis Ransomware (80/20 split) – A classic RaaS model where affiliates receive 80% of ransom payments.
- Data Ransom (60/40 split) – Monetizing stolen data by threatening exposure.
- Access Monetization (50/50 split) – Selling corporate access credentials to ransomware operators.
According to the KELA report, Anubis ransomware possesses advanced functionalities, including:
- Encryption Algorithm: Uses ChaCha+ECIES encryption.
- Cross-Platform Targeting: Affects Windows, Linux, NAS, and ESXi environments.
- Privilege Escalation: Gains NT AUTHORITY\SYSTEM privileges.
- Lateral Movement: Self-propagates across domains.
- Management Interface: Controlled via a web-based panel.
These features indicate that Anubis is not an amateur operation, but rather a highly structured ransomware service.
Beyond encryption-based attacks, Anubis employs sophisticated extortion mechanisms, including:
- Investigative Journalism Approach:
- Writes ‘investigative articles’ based on stolen corporate data.
- Publishes them on a hidden, password-protected page.
- Notifies affected regulatory bodies (GDPR, HHS, ICO, etc.) to increase pressure.
- Negotiation and Threats:
- Victims receive direct calls informing them of the attack.
- If they refuse to pay, all stolen data is leaked publicly
Anubis has already claimed four victims across multiple industries, including healthcare and construction:
- Pound Road Medical Centre (PRMC, Australia) – Reported a data breach on November 13, 2024, involving medical records and Medicare information.
- Summit Home Health (Canada) – Anubis leaked stolen medical data for free on December 29, 2024.
- Comercializadora S&E Perú – A Peruvian construction company whose data was leaked in December 2024.
- Unnamed U.S. Engineering Firm – The latest victim, revealed on February 25, 2025.
Notably, two of the four victims belong to the healthcare sector, highlighting Anubis’ potential focus on critical industries.
KELA’s analysis suggests that Anubis’ operators may be former affiliates of other ransomware groups, based on their:
- Well-structured extortion methods.
- Technical sophistication in ransomware development.
- Use of detailed investigative-style victim exposure tactics.
The group operates in Russian-language cybercrime forums, further supporting the theory that Anubis could have ties to previous ransomware syndicates.
Related Posts:
- A new bank Trojan, BankBot Anubis was found PhishLabs
- Cybercriminals have been earned over $16 million by distributing ransomware for 2 years
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected
