Beware of Fake Google Chrome Update Pop-Ups: Malicious Campaign Targets Hundreds of Websites
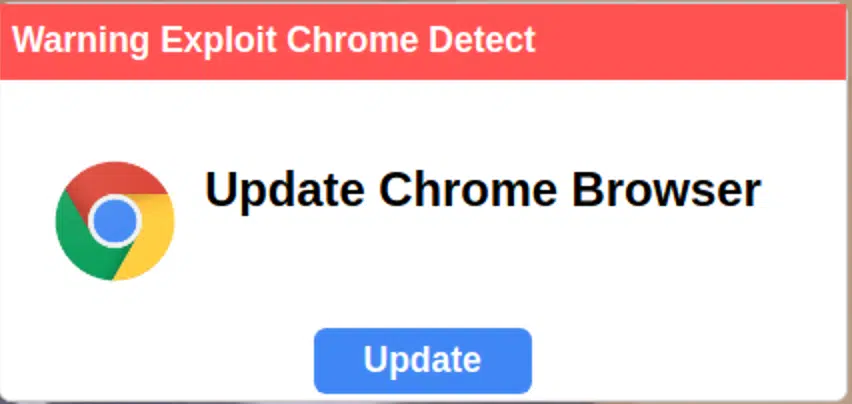
A new cyberattack campaign is underway, targeting hundreds of websites with deceptive pop-up messages urging users to update their Google Chrome browsers. This scheme, identified by security analyst Puja Srivastava at Sucuri, injects malicious code into vulnerable websites, even those not using the Chrome browser, to trick visitors into downloading harmful malware.

The attack begins with hackers compromising websites and inserting malicious code, often through the legitimate WordPress plugin “Hustle.” Upon visiting the compromised site, users encounter a pop-up warning of a Chrome exploit and urging an immediate update. Clicking the provided “Update” button redirects users to malicious URLs, leading to the download of malware disguised as a Chrome update file.
Upon clicking the update button, users are redirected to malicious URLs designed to initiate a malware download. Some of these URLs include:
- hxxps://photoshop-adobe[.]shop/download/dwnl.php
- hxxps://brow-ser-update[.]top/download/dwnl.php
- hxxps://tinyurl[.]com/uoiqwje3
While these URLs are now inactive, they previously served malware downloads named GoogleChrome-x86.msix from server 185.196.9[.]156. The malicious domains were created as early as March 2024, with brow-ser-update[.]top created on May 3, 2024, and photoshop-adobe[.]shop on March 14, 2024.
At the time of writing, PublicWWW finds this fake browser update pop-up on 341 websites. Sucuri’s SiteCheck remote website scanner detects this threat as malware.fake_update.3.
This campaign underscores a growing trend among hackers to leverage legitimate plugins for malicious purposes, evading detection and going unnoticed in environments with numerous plugins. Similar tactics have been seen in other WordPress infection campaigns, such as the VexTrio DNS TXT redirects using the WPCode plugin and the Sign1 malware exploiting the Simple Custom CSS and JS plugin.
Website owners are urged to take immediate action to protect their sites and users:
- Regularly review and remove unused plugins.
- Use strong, unique passwords for all accounts.
- Monitor websites for suspicious activity and unauthorized users.
- Consider implementing two-factor authentication and restricting access to sensitive areas.
- Keep all software updated, including CMS, plugins, and themes.
- Utilize a web application firewall to defend against vulnerabilities and attacks.
Users are advised to exercise caution when encountering browser update prompts, verify the legitimacy of the source, and avoid clicking on suspicious links or downloading files from unknown sources.





