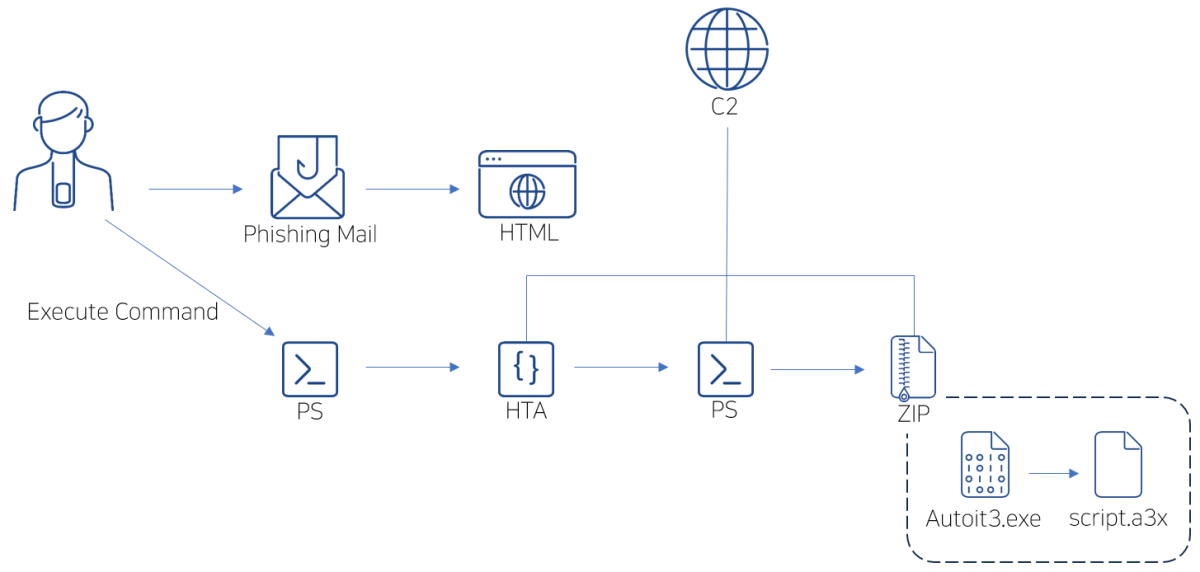
Overall flow | Image: ASEC
AhnLab SEcurity Intelligence Center (ASEC) has recently identified a phishing campaign leveraging HTML files distributed via email to execute malicious commands on targeted systems. This sophisticated method prompts users to paste commands directly from their clipboard, circumventing traditional security measures and making detection more challenging.
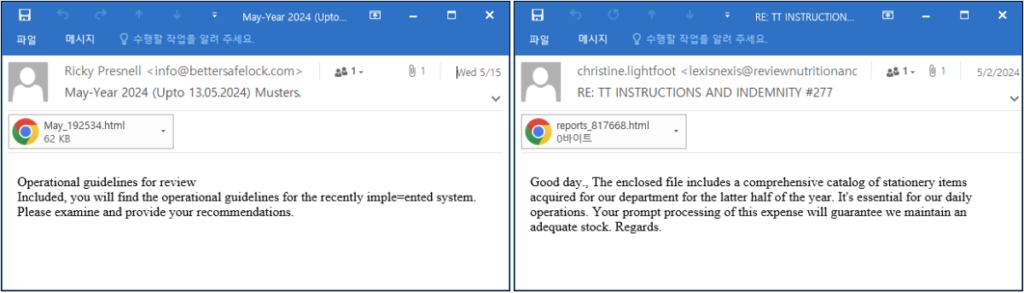
The phishing campaign begins with emails crafted to look like routine communications regarding fee processing or operational instructions. These emails contain HTML attachments designed to appear as Microsoft Word documents when opened. Users are instructed to click a “How to fix” button within the faux Word interface, ostensibly to view the document offline.
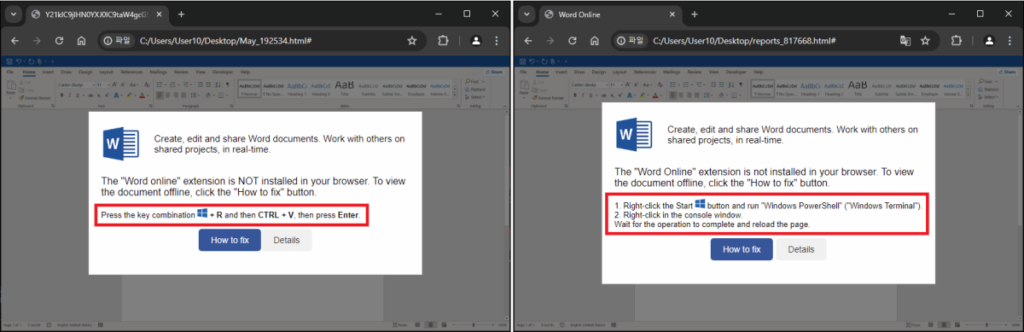
Upon clicking the button, the HTML file prompts users to press [Win+R], paste the command using [CTRL+V], and hit [Enter]. Alternatively, users can open the PowerShell terminal and manually input the command. Behind the scenes, a Base64-encoded PowerShell command is decoded by embedded JavaScript and copied to the clipboard.
Once pasted and executed, this PowerShell command initiates the download of an HTA (HTML Application) file from a command and control (C2) server. This HTA file then executes another PowerShell command, blanking out the clipboard to obscure the executed commands.
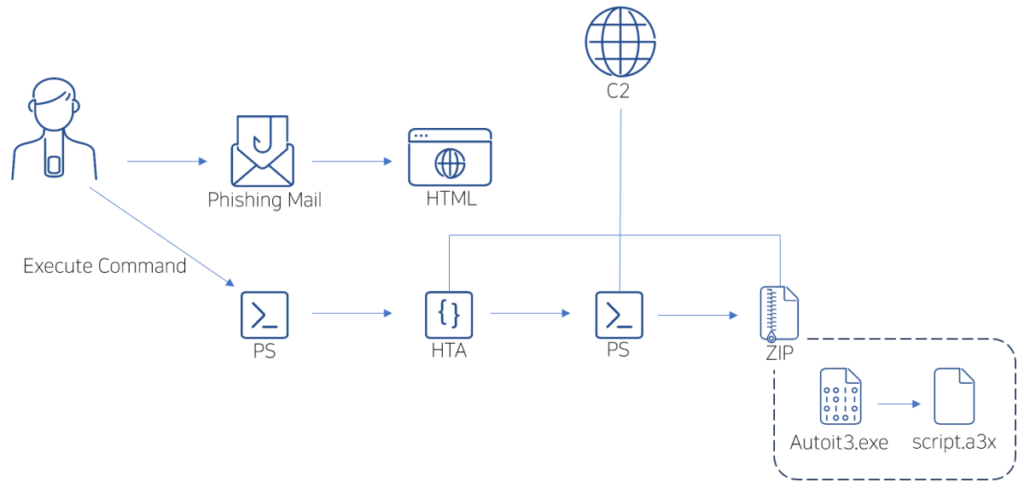
The final payload in this multi-stage attack is the DarkGate malware. Delivered through Autoit3.exe inside a ZIP file, the malware uses a compiled Autoit script (script.a3x) to infect the system. DarkGate, known for its versatility and stealth, can perform various malicious activities, from data theft to system hijacking.
The AhnLab Security Intelligence Center (ASEC), which discovered this new threat, warns users to exercise extreme caution when handling files from unknown sources, especially those received via email.