A new report from the Unit 42 Incident Response team reveals a disturbing trend in cyber attacks: the increasing use of Microsoft OneNote files to deliver malicious payloads. Analyzing around 6,000 malicious samples, they found that attackers are increasingly leveraging OneNote’s embedding capabilities to execute phishing-like attacks.
With macros disabled by default in Office applications, cybercriminals have turned to OneNote as a new avenue for deploying malware. These malicious OneNote files often appear as legitimate notes, luring victims with enticing images and buttons. When clicked, these buttons trigger the execution of hidden payloads, leading to a variety of harmful outcomes.
The Unit 42 team discovered that almost all malicious OneNote samples contained at least one image used to trick users into clicking on embedded objects. These images often resemble buttons, enticing users to interact with them. When clicked, the embedded malicious payloads execute, compromising the victim’s system.
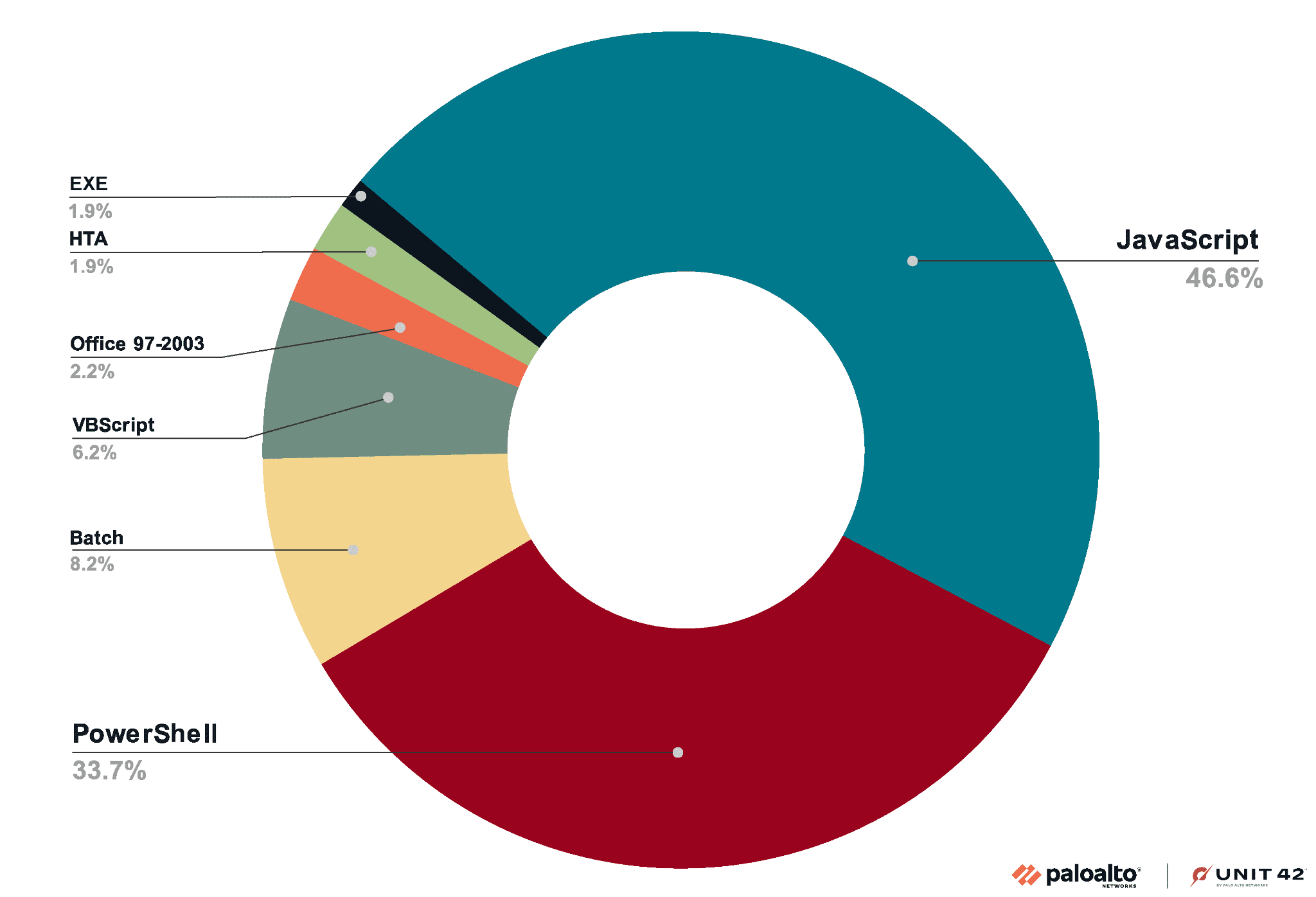
Attackers embed various payload types within OneNote files, including:
- JavaScript
- VBScript
- PowerShell
- HTML Application (HTA)
- Batch files
- Office 97-2003 files
- Executables (EXE)
While smaller payloads like JavaScript are more commonly used due to their size, larger binary payloads like EXE and Office 97-2003 files are less frequent but more capable. This is illustrated in the following figure, which shows the distribution of payload types and their sizes. Attackers prefer smaller payloads for ease of delivery through common methods like email attachments, which reduces suspicion.
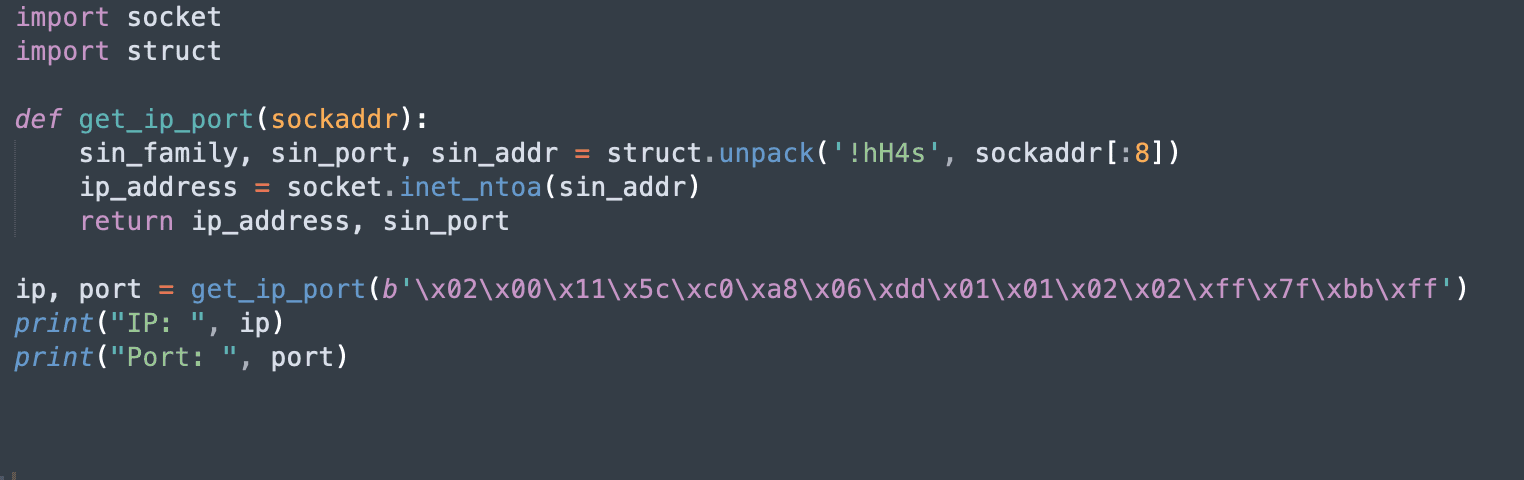
The report provides an in-depth analysis of an embedded EXE payload, revealing the malicious intent through code examination in tools like IDA Pro and x64dbg. The analysis uncovered shellcode designed to establish a network socket, likely for a reverse TCP shell to connect back to the attacker’s machine.

To protect themselves, users should exercise caution when opening OneNote files from untrusted sources. Hovering over buttons and images before clicking can reveal suspicious file names and extensions. Organizations can also consider blocking embedded payloads with dangerous extensions within OneNote files.