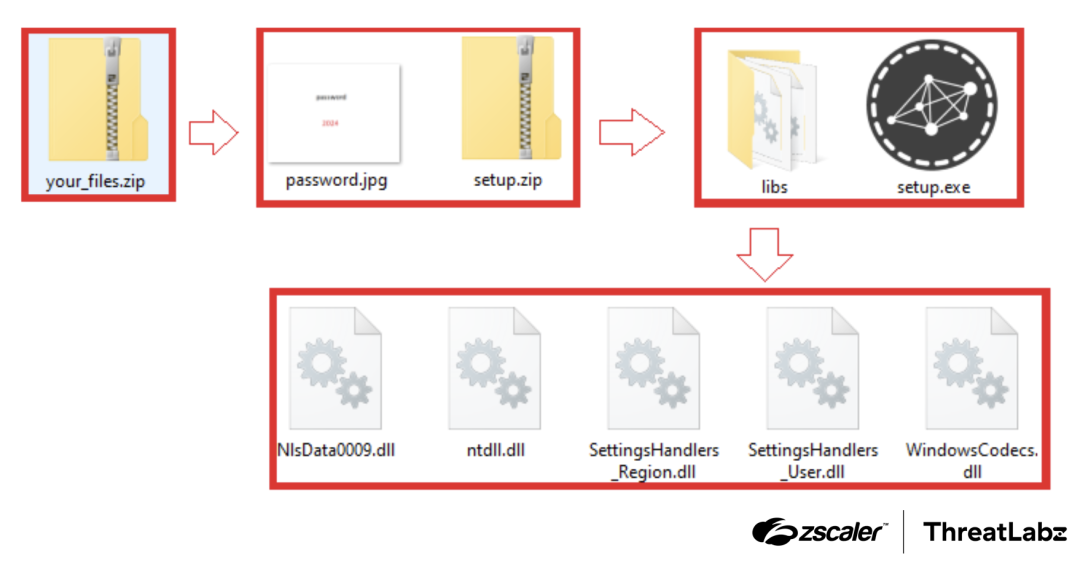
The files after extracting two ZIP archives
Security experts at Zscaler ThreatLabz have revealed a widespread campaign where hackers are hijacking legitimate web hosting platforms to distribute dangerous malware. By mimicking legitimate websites and using fraudulent search engine optimization (SEO) tactics, these attackers are tricking users into downloading malware disguised as free software, cracked games, or even enticing deals.
These nefarious sites cover a wide range of topics—from pirated software and gaming to travel and cooking—making them more likely to appear in search results across various interests. Once a user lands on one of these sites, the malware delivery process begins, cleverly disguised and often involving multiple stages to evade detection.
The primary method of attack involves the deployment of malicious payloads through multi-level zipped files, which seem benign but contain dangerous executables. Upon execution, these files launch sophisticated attacks that include techniques such as process hollowing, DLL sideloading, and the execution of PowerShell commands to download further malicious payloads and establish communication with command-and-control (C2) servers.

The malware is particularly invasive, gathering extensive data from the infected systems, including system information, browser data, credentials, and browsing history. It also targets emails related to cryptocurrency exchanges, potentially altering email content and stealing authentication codes.
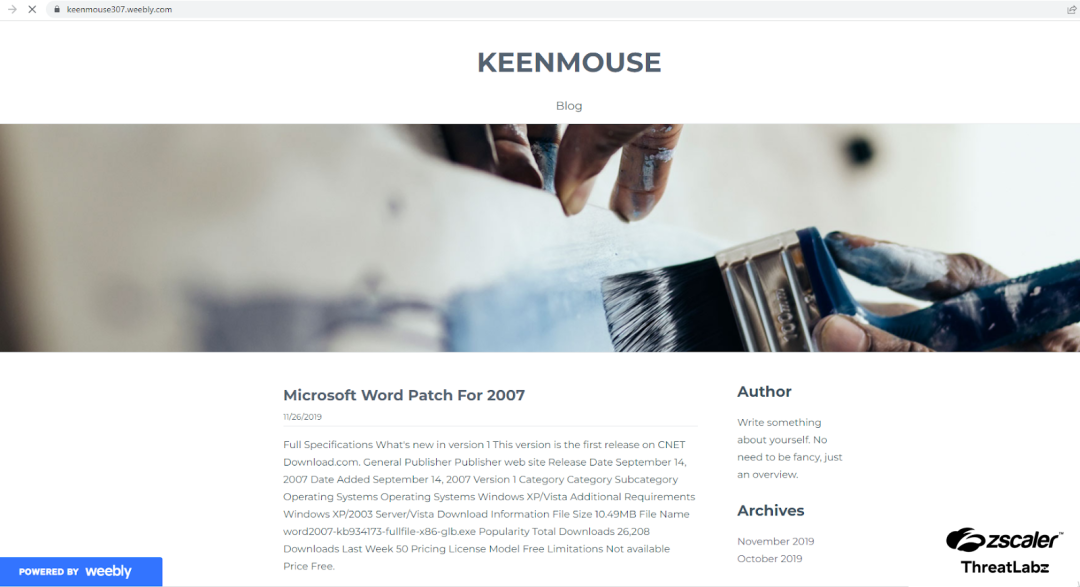
One example highlighted by the researchers was a fraudulent website hosted on Weebly. It appeared in Google search results as a legitimate site due to its “Powered by Weebly” label, but was a front for distributing malware. This misuse of reputable hosting services complicates users’ ability to distinguish between safe and unsafe sites.
The attackers have developed sophisticated methods to avoid detection. For instance, they employ scripts that check the referring URL; if the traffic comes from a search engine, the script redirects the user to a malicious page. However, if the URL is entered directly—potentially by a security researcher examining the site—it does not redirect, thereby evading further analysis.
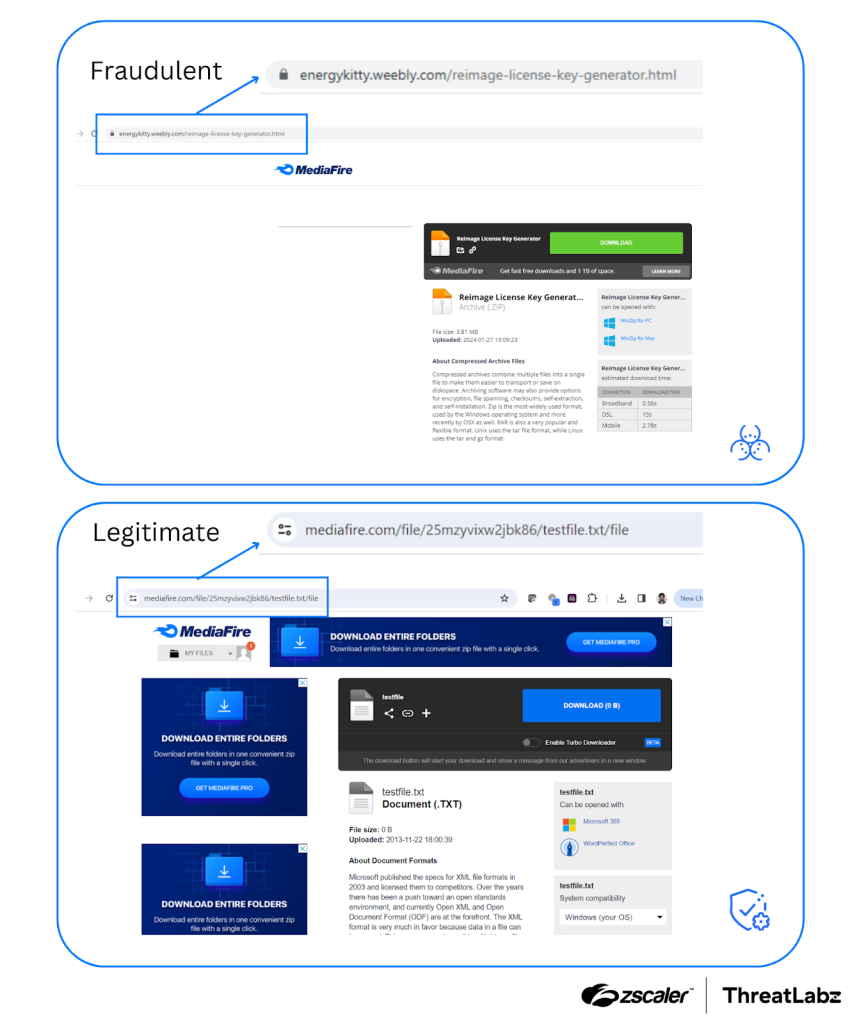
In an example of payload delivery, users searching for cracked software might be directed to a fake MediaFire page that looks convincingly legitimate but hosts malware instead. The payload files are intricately concealed within two levels of zipped archives, with the second zip file password-protected and the password cleverly hidden within an image file in the first archive.
Upon downloading and executing the supposed setup file, what seems to be a regular installation of legitimate software like the GNU Privacy Guard, actually results in the simultaneous installation of a malicious DLL. This DLL then uses DLL sideloading to perform malicious activities under the guise of legitimate processes.
This Zscaler report underscores how cybercriminals constantly refine their attacks. By staying informed about their methods and exercising caution online, we can significantly lower our risk of falling victim to these digital traps.