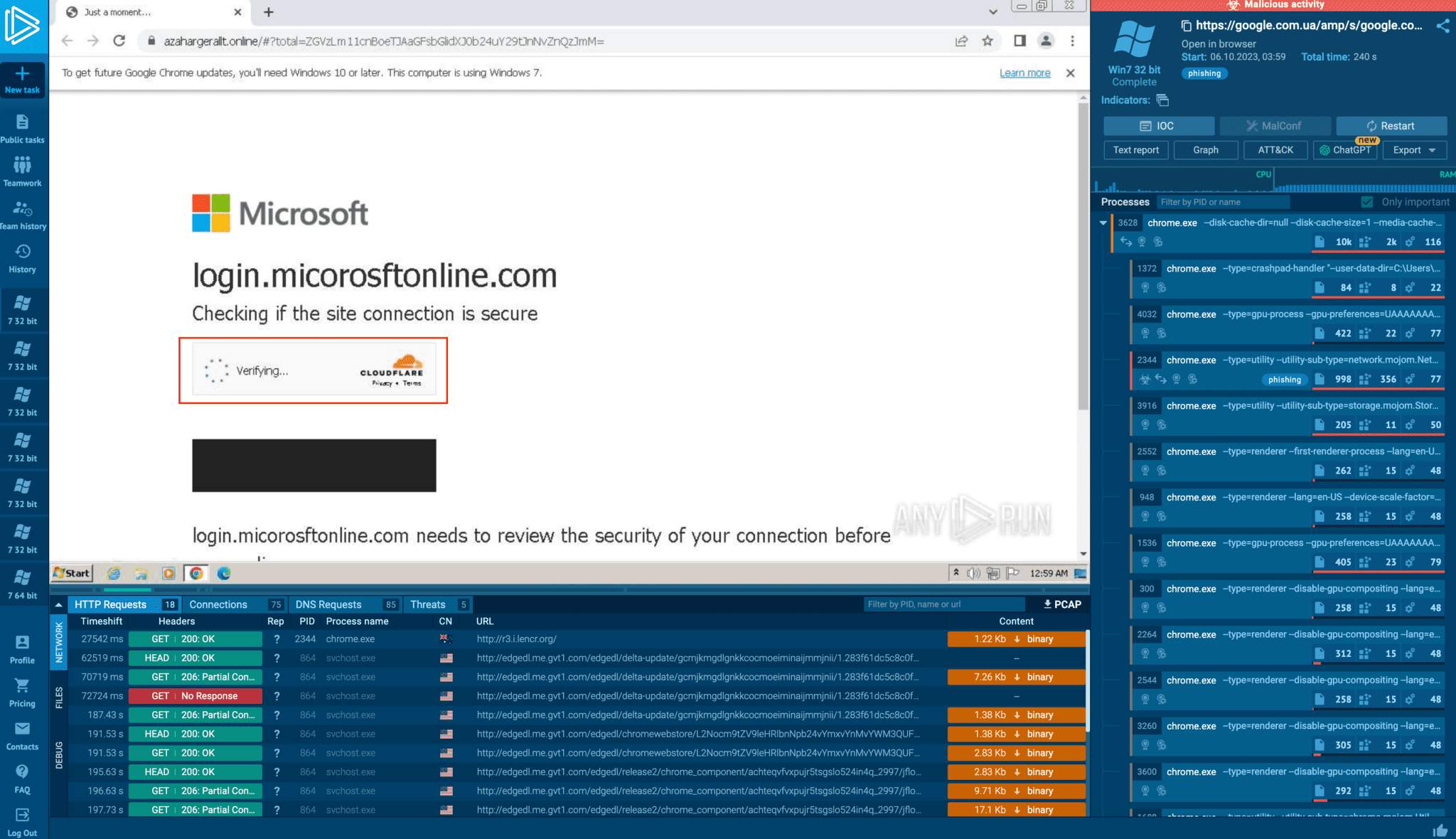
The credential harvesting forms are concealed behind CloudFlare’s captcha service | Image:
According to statistics from cybersecurity company ANY.RUN, the year 2023 witnessed the rise of QR codes, CAPTCHA, and steganography as popular phishing methods.
A novel phishing technique, Quishing (a blend of QR and phishing), involves concealing malicious links within QR codes. This method effectively evades detection by traditional anti-spam filters, which primarily focus on text messages. Due to many security tools’ inability to decipher the contents of QR codes, this method has proven particularly potent for cybercriminals.

Phishing attacks also exploit CAPTCHA, a security feature of websites. Criminals use CAPTCHA to disguise credential collection forms on counterfeit websites, creating hundreds of domain names through a Randomized Domain Generated Algorithm (RDGA) and incorporating CAPTCHA. For instance, during an attack on an employee of Halliburton Corporation, the victim is first asked to pass a CAPTCHA check before being redirected to a fake Office 365 login page.
Phishing campaigns also employ steganography – the art of hiding data within various media forms. For example, in a fraudulent email from a Colombian government organization containing a Dropbox link, an embedded VBS script covertly extracts an image with malicious code, infecting the victim’s system.
Given the evolution of phishing attacks and new methods such as the use of QR codes, CAPTCHA, and steganography, users and organizations must be more vigilant and informed about potential threats. It is crucial to employ modern tools and services for analyzing and preventing malicious attacks. Cybersecurity awareness and training also play a pivotal role in combating cybercrime.