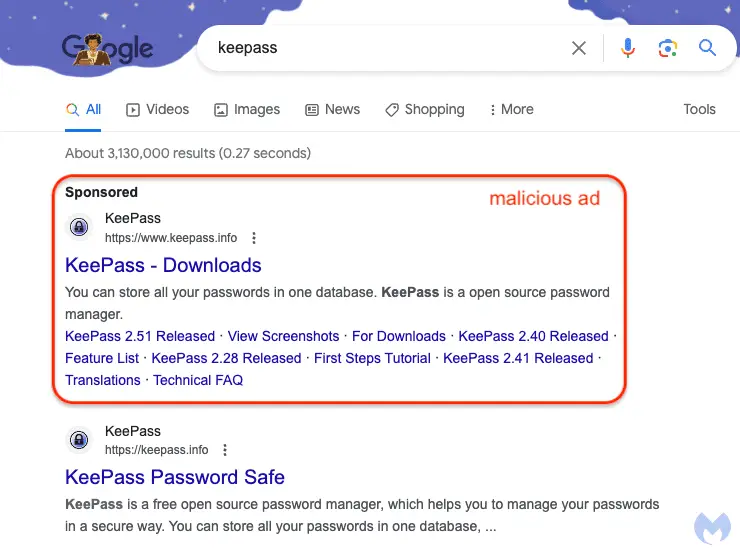
Malicious ad for KeePass followed by legitimate organic search result | Source: Malwarebytes
According to Malwarebytes, malefactors are promoting a counterfeit KeePass official website through Google advertisements. This spurious site employs Punycode to masquerade as the official domain of the KeePass password manager, with the intent of disseminating malicious software.
Punycode is an encoding scheme used to handle non-ASCII characters (such as Cyrillic, Arabic, Greek letters, and Chinese characters) in domain names on the internet. Its primary objective is to convert non-ASCII characters into pure ASCII characters, facilitating proper resolution and processing within the Domain Name System (DNS).

From captured images, it is evident that the falsified KeePass official website emerges prominently in Google search results. Google’s ad system has been manipulated, showcasing what appears to be KeePass’s legitimate domain (https://www.keepass.info), exhibiting profound deception. Even the most security-conscious users might struggle to detect the discrepancy.
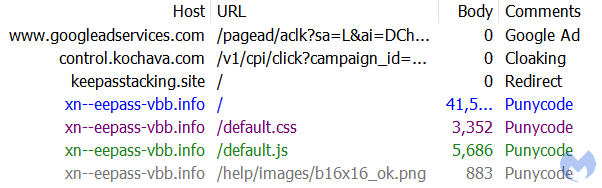
After filtering out bot traffic and sandboxes, users who click on the malicious link will be redirected to the counterfeit KeePass site with a Punycode URL (https://xn--eepass-vbb[.]info/).
In essence, the real domain of this phishing website is “ķeepass.info”—seemingly indistinguishable from the KeePass official site, isn’t it? Upon meticulous observation, one can discern a subtle diacritic below the character “ķ.” Alas, most individuals, without a prompt, would remain oblivious, leading one to ponder the multitude that could be ensnared.

Users who venture to click on any embedded download link on this phishing site will be presented with a digitally signed MSI installer named “KeePass-2.55-Setup.msix”, which contains a PowerShell script affiliated with the FakeBat malware loader.
This incident serves as a stark reminder of the necessity for meticulous discernment when downloading software. Within corporate environments, it’s prudent for IT administrators to provision an internal software repository, ensuring employees can safely acquire software installation packages.