Beware the New TrickMo Banking Trojan: Enhanced Features, Increased Danger
In a recent report, the Cleafy Threat Intelligence Team uncovered a new variant of the infamous TrickMo banking trojan, which now carries even more dangerous capabilities than its predecessors. TrickMo, part of the TrickBot malware family, has evolved significantly since its initial discovery in 2019 by CERT-Bund. Originally designed to target banking credentials on Android devices, TrickMo’s latest iteration is equipped with enhanced anti-analysis mechanisms and dangerous new features, posing severe threats not only to banking security but also to users’ personal privacy and security.
While TrickMo was initially known for its ability to intercept One-Time Passwords (OTPs) and bypass Two-Factor Authentication (2FA) systems, this new variant introduces capabilities that extend far beyond traditional banking fraud. By incorporating features such as screen recording, keylogging, and remote control, TrickMo enables attackers to conduct On-Device Fraud (ODF)—a method of financial fraud where the attack happens directly on the victim’s device, bypassing even the most secure banking apps.
However, the Cleafy researchers discovered an even more troubling dimension of TrickMo’s operation: data leaks from compromised devices. The stolen data, which includes personal photos, credentials, and potentially sensitive documents, was found to be stored on exposed Command-and-Control (C2) servers with no authentication requirements, allowing third parties easy access to the exfiltrated data. This misconfiguration highlights serious operational flaws by the threat actors, but it also puts victims at risk of further exploitation.
TrickMo’s evolution has made it a highly sophisticated and stealthy threat. Here are the key features of this new variant:
- Interception of OTPs: TrickMo can intercept OTPs from SMS messages or authentication apps, allowing attackers to bypass 2FA and authorize fraudulent transactions.
- Screen Recording and Keylogging: The malware can record the victim’s screen and capture keystrokes, giving attackers access to login credentials, PINs, and other sensitive information.
- Remote Control of Devices: TrickMo allows attackers to remotely control the infected device, enabling them to perform unauthorized transactions, modify account settings, and even control the victim’s device without their knowledge.
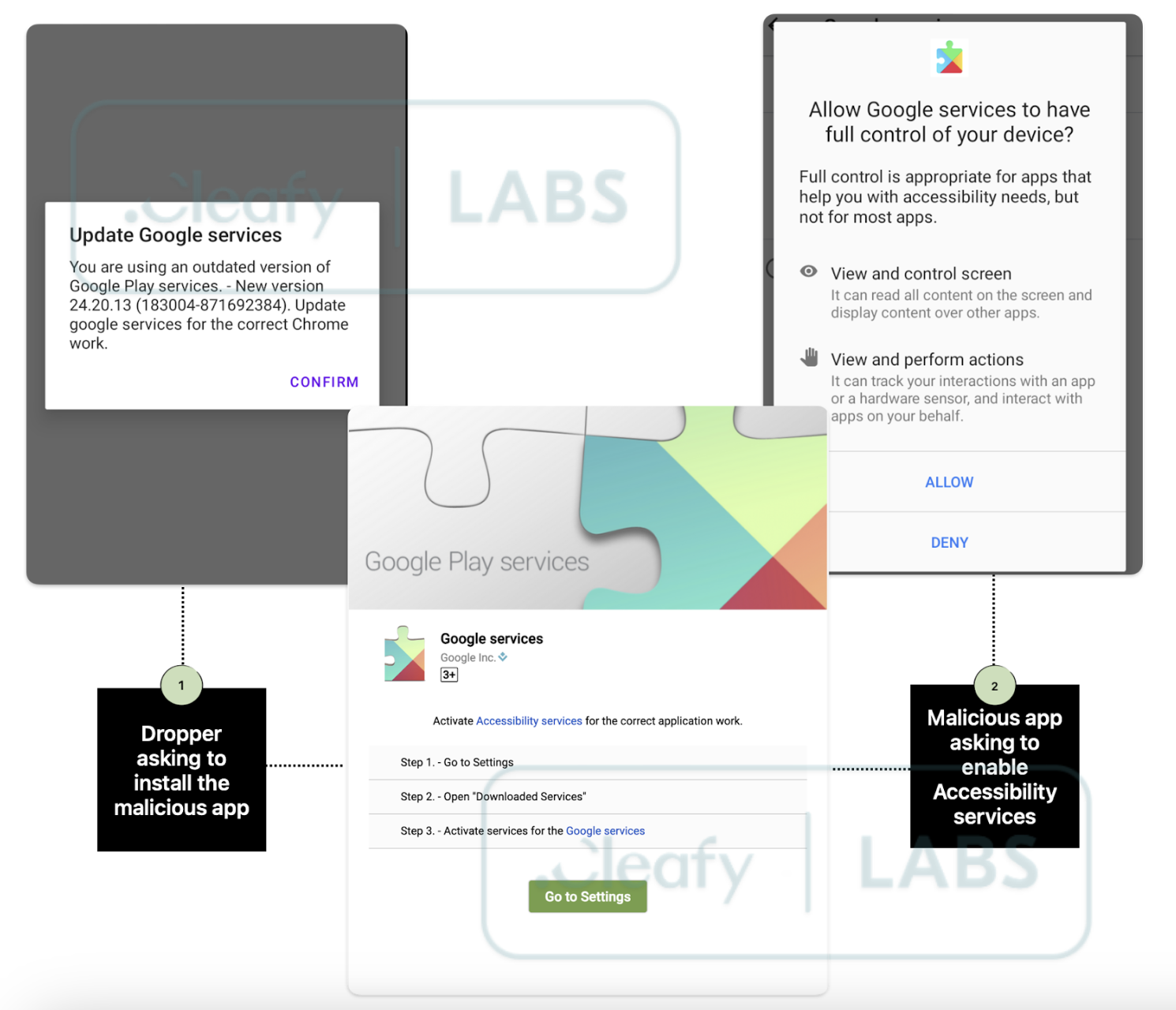
- Abuse of Accessibility Services: By exploiting Android’s Accessibility Services, TrickMo gains elevated permissions to manipulate user inputs, intercept communications, and carry out attacks without detection.
- Advanced Obfuscation and Anti-Analysis Mechanisms: TrickMo trojan employs sophisticated techniques like malformed ZIP files, JSONPacker, and dropper apps to hide its malicious payload, making it harder for security professionals to analyze and mitigate the threat.
The real danger of this new TrickMo variant lies in its ability to exfiltrate sensitive data from infected devices, including personal photos, credentials, and documents. The data is stored on a poorly secured C2 server, where anyone with knowledge of the server’s endpoints can access the information. Cleafy’s analysis revealed over 12 GB of stolen data, including personal identification documents, financial information, and even intimate photos of the victims.
This publicly exposed data not only leads to identity theft and fraud, but also makes victims vulnerable to extortion and blackmail. The threat actors behind TrickMo trojan have left this data accessible to other cybercriminals, opening the door for a range of additional malicious activities beyond the original intent of banking fraud.
With TrickMo’s ability to intercept banking information and leak personal data, victims are exposed to multiple risks. Financial fraud, identity theft, and extortion are just a few of the threats posed by this malware. Compromised email accounts can be leveraged to reset passwords for other services, and stolen photos can be used in highly targeted phishing or social engineering attacks.
TrickMo’s misuse of Android’s Accessibility Services adds another layer of complexity, allowing the malware to perform automated actions, such as accepting permissions, blocking system updates, and disabling security features—all without the user’s awareness.





