Image: Xlabs
Xlab uncovered a new threat emerging from the notorious “8220” mining gang, also known as “Water Sigbin.” This gang, originating from China and active since 2017, has been a persistent menace in the cybersecurity landscape. Their latest creation, dubbed “k4spreader,” represents a significant evolution in their arsenal, combining advanced persistence mechanisms and sophisticated malware delivery techniques.
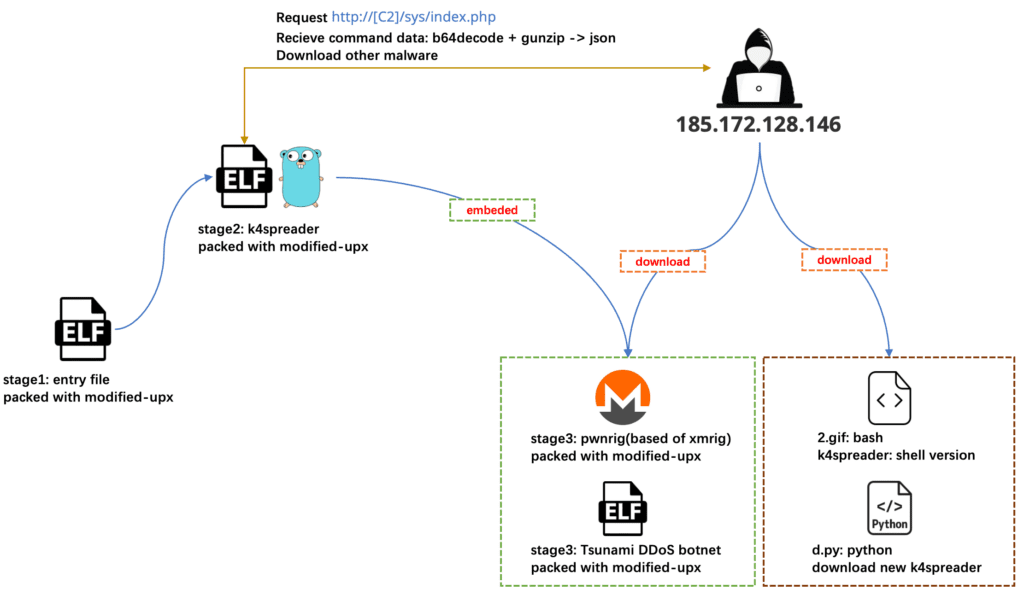
The discovery of k4spreader began with an ELF sample written in C, which exhibited a detection rate of zero on VirusTotal (VT). This sample was packed using a modified UPX packer. After unpacking, analysts found another UPX-packed ELF file, written in CGO mode, a blend of C and Go languages. This revealed the k4spreader installer, designed to deploy other malware, notably the Tsunami DDoS botnet and the PwnRig mining program.
Key Features of k4spreader
- Persistence and Self-Update Mechanisms:
- System Persistence: k4spreader modifies the bash startup configuration file and system services to ensure it remains active and re-executes upon system reboot. It uses techniques like modifying
.bash_profileand creating services in/etc/init.dand/etc/systemd/system. - Self-Update: The tool can download and execute updated versions of itself, ensuring it remains current and effective against new defenses.
- System Persistence: k4spreader modifies the bash startup configuration file and system services to ensure it remains active and re-executes upon system reboot. It uses techniques like modifying
- Malware Deployment:
- Tsunami DDoS Botnet: Tsunami uses IRC protocol for command and control, enabling remote control and DDoS attacks, indicating an expansion of 8220’s activities beyond cryptomining.
- PwnRig Mining Program: A customized version of the open-source XMRig, designed for Monero mining, illustrating 8220’s continued interest in cryptomining.
- Stealth and Evasion:
- Modified UPX Packer: k4spreader uses a modified UPX packer to evade static antivirus detection. The latest version, v3, employs dual layers of packing to further obfuscate its code.
- C2 Communication: The tool communicates with command and control (C2) servers, utilizing base64, gzip compression, and JSON formats to standardize and obscure its data transfers.
- System Interference:
- Firewall Manipulation: k4spreader disables firewalls and allows all network traffic, increasing the system’s vulnerability to further attacks.
- Malware Cleanup: It detects and removes competing malware, ensuring its operations are unimpeded.
Analysis of k4spreader samples has revealed a pattern of continuous improvement and adaptation. The gang is actively developing and refining the tool, with three variants already identified. Each version incorporates new features and evasion techniques, making detection and mitigation increasingly challenging. Notably, version 3 of k4spreader employs a double layer of modified upx packing, a technique designed to evade antivirus detection.
This escalating sophistication underscores the gang’s dedication to their malicious endeavors and highlights the need for increased vigilance among cybersecurity professionals and organizations. The potential impact of k4spreader is far-reaching, as it enables the 8220 mining gang to compromise a wider range of systems and deploy a variety of payloads, posing a significant threat to both individuals and businesses.
In addition to the deployment of k4spreader, the 8220 gang has been observed exploiting several known vulnerabilities, including CVE-2020-14882, JBoss_AS_3456_RCE, and YARN_API_RCE, to gain unauthorized access to systems. Furthermore, passive DNS analysis has revealed a network of command-and-control (C2) servers associated with k4spreader and other malicious activities linked to the gang, suggesting a well-organized and coordinated operation.
The emergence of k4spreader marks a significant development in the tactics of the 8220 mining gang. By expanding their toolkit to include advanced DDoS capabilities alongside cryptomining, they pose a broader threat to cybersecurity. Organizations must remain vigilant, ensuring systems are updated and defenses are robust against such evolving threats.
For a detailed analysis and indicators of compromise (IoCs), visit Xlab’s official report.