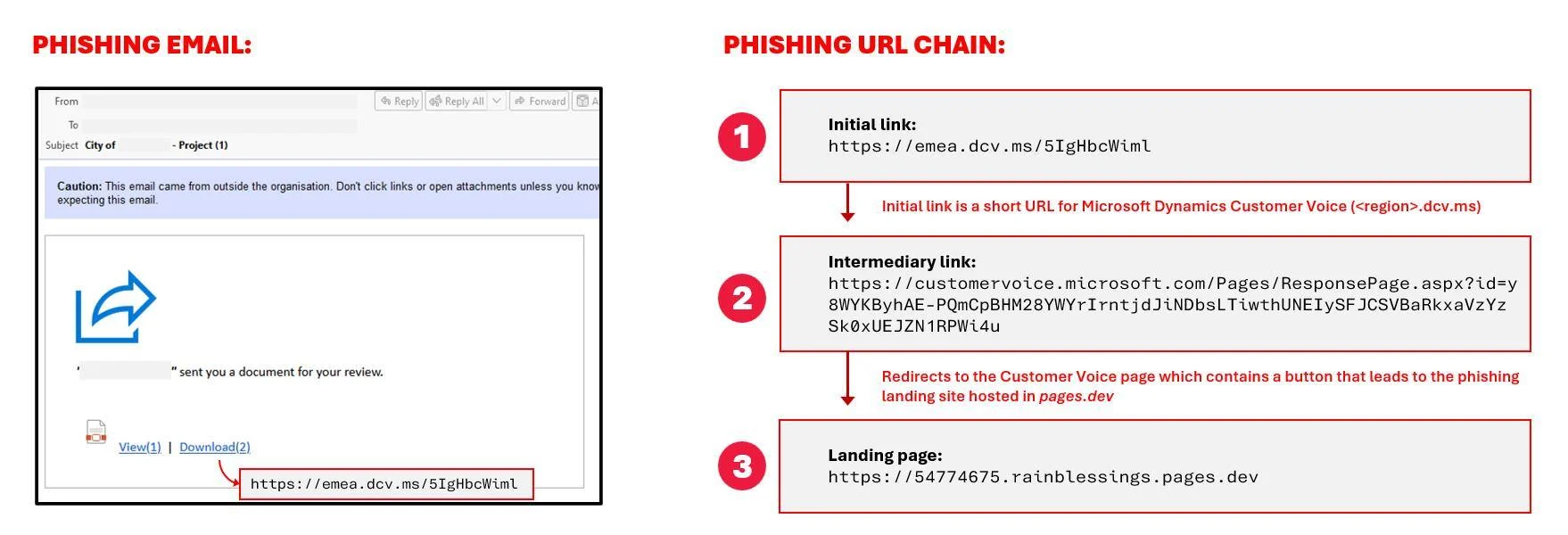
Malicious actors abuse Dynamics 365 Customer Voice in phishing attacks | Image: Trustwave
The Rockstar Phishing-as-a-Service (PaaS) kit has caught the attention of cybersecurity experts for its advanced and devious tactics to bypass email defenses. In a report from Trustwave SpiderLabs, Rockstar’s arsenal includes fully undetectable (FUD) links and multi-stage phishing techniques, exploiting trusted platforms like Microsoft OneDrive, Atlassian Confluence, and Google Docs to deliver convincing phishing campaigns.
Rockstar’s PaaS platform specializes in generating FUD links, bypassing traditional URL-based detection mechanisms. The report notes, “These FUD links are specifically crafted to evade URL-based detection systems, which usually only examine the initial link to determine malicious intent.” By leveraging legitimate services like Microsoft OneDrive, Google Docs, and Atlassian Confluence, these campaigns gain an aura of credibility that tricks unsuspecting victims.
Techniques and Platforms Abused
- Microsoft OneDrive: Phishers use
.urlshortcut files hosted on OneDrive to redirect victims to phishing landing pages. The files are disguised as project proposals or similar documents. Clicking the shortcut seamlessly opens a browser tab leading to malicious content. - Google Docs Viewer: Malicious actors abuse this service to embed harmful PDFs. According to the report, “This Google service acts as a loader for malicious PDFs” by linking users to external phishing websites.
- Atlassian Confluence: In one campaign, attackers created phishing emails resembling shared Excel document notifications. These emails redirected victims to a Confluence page, which hosted another malicious link impersonating an Office 365 login page.
- QR Code Phishing (Quishing): A growing trend involves embedding phishing URLs within QR codes. In a highlighted case, attackers impersonated DocuSign, urging users to scan a QR code in a fake document to access the phishing site.
- Microsoft Dynamics 365 Customer Voice: This feedback management platform was exploited as a link stager to hide phishing redirects behind seemingly legitimate URLs.
Rockstar campaigns also employ advanced obfuscation techniques. HTML attachments are split into tokens, and phishing URLs are fragmented across arrays with hidden elements interspersed. The report highlights, “These obfuscation techniques evade detection methods that rely on keyword matching.”
A hallmark of Rockstar’s PaaS campaigns is their multi-stage approach. Each phase uses a legitimate platform to host malicious content or redirect victims to the next stage. SpiderLabs observed, “PDF, HTML, and MS Office documents are the files most abused by this kit,” with these files containing embedded links or QR codes leading to final-stage phishing pages.
Related Posts:
- 0-day bug in Riot Games Grand Theft Auto V for PC
- QR Code Phishing Attacks Escalate: Sophisticated Campaign Targets Chinese Citizens
- The Hidden Danger of PDF Files with Embedded QR Codes, Researchers Warn
- QR Codes Coming to Linux Kernel Panics with 6.12 Release