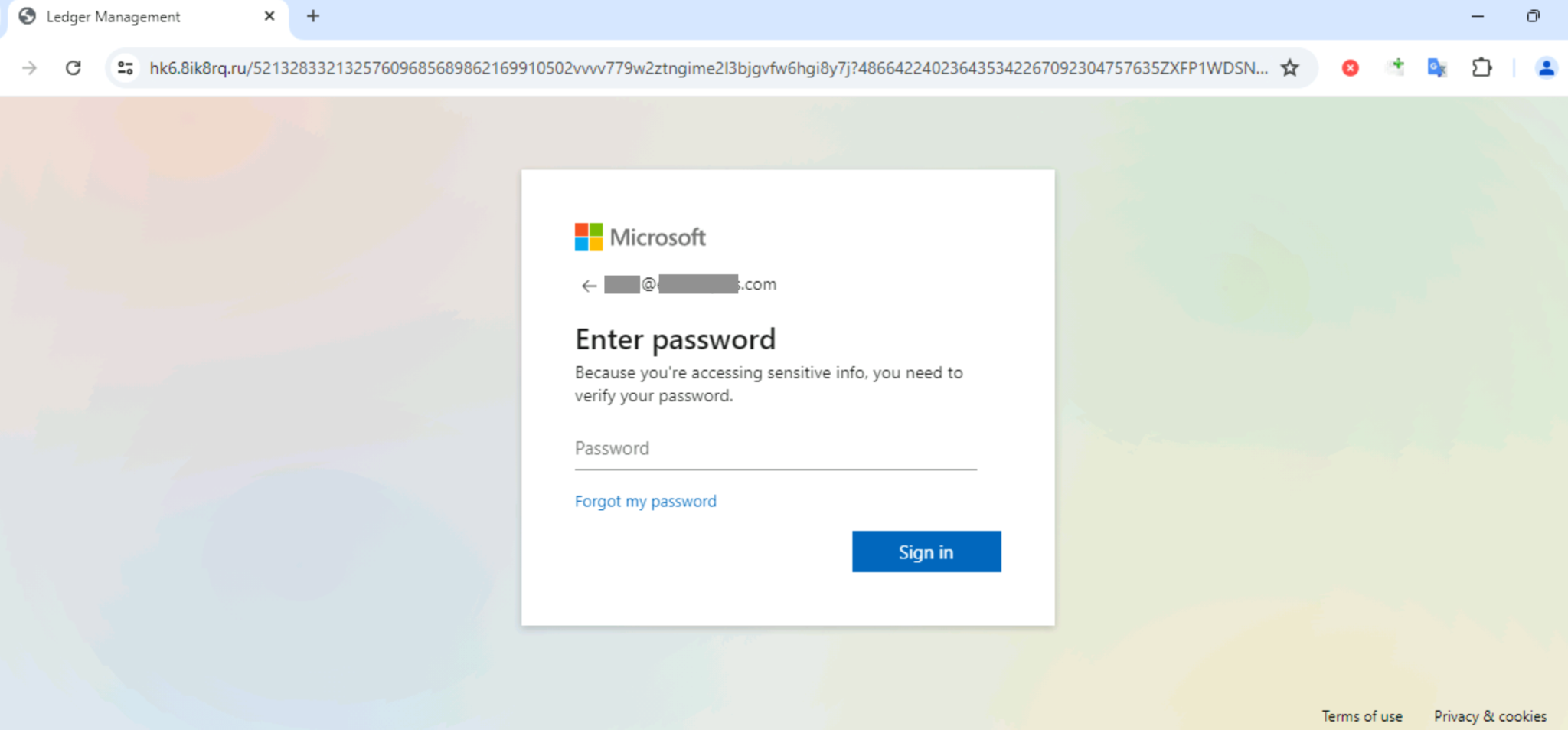
Phishing page, sent through a refresh entry in an HTTP response header | Image: Unit 42
Unit 42 researchers from Palo Alto Networks have uncovered a wave of large-scale phishing campaigns exploiting a lesser-known technique: phishing pages delivered through the HTTP Refresh Response Header. Unlike typical phishing tactics that rely on malicious HTML content, this method uses the response header sent by a server to redirect users to fraudulent sites before any HTML content is processed. From May to July 2024, researchers detected an average of 2,000 malicious URLs per day, signaling the widespread use of this method.
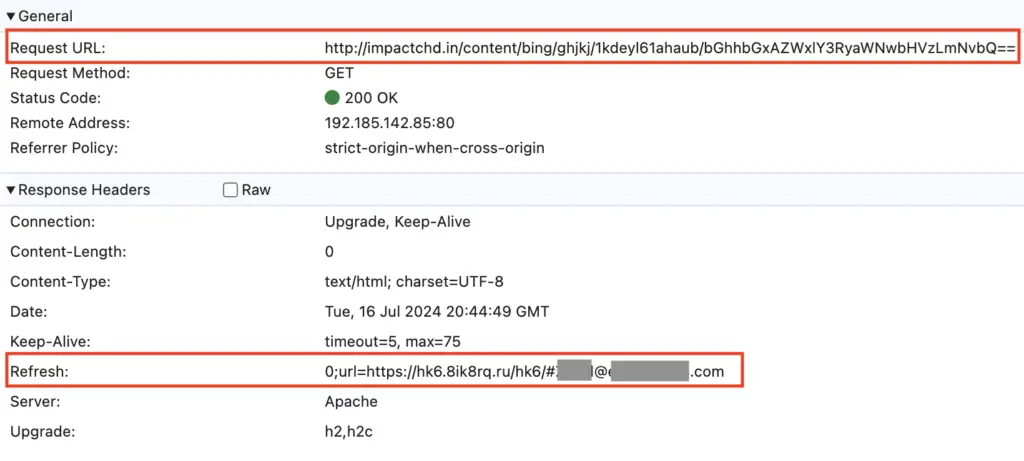
Phishing attacks using the HTTP refresh technique begin by embedding malicious links in the HTTP response header, a part of the server’s response to a browser request. When the user clicks on a phishing link, the browser automatically reloads or redirects to a phishing page—without any user interaction required. Attackers then use this method to load phishing pages that closely resemble legitimate webmail login portals or other trusted sites, tricking users into entering their credentials.
These attacks typically target recipients via phishing emails. Commonly, the emails include pre-filled information, such as the recipient’s email address, in the phishing page’s form fields, making the fraudulent site appear even more legitimate. This sophisticated level of personalization greatly increases the chances of successful credential theft.
The Unit 42 report highlights that these phishing campaigns primarily target organizations in the financial services, government, and business sectors, with recipients often working for global financial institutions, popular internet portals, and government domains. The use of legitimate or compromised domains to host the malicious URLs adds another layer of complexity, making it difficult for victims and security professionals to easily identify the threat.
One notable campaign observed from June 20-21, 2024, targeted large corporations in Korea and government agencies in the U.S. The phishing emails in this campaign were sent from a common spoofed sender (e.g., 2127394249@docusign[.]com) and consistently used subject lines like “Complete with DocuSign: ACH/EFT FORM”. This campaign targeted industries including finance, government, and education, with over 34% of the attacks aimed at people in the business sector.
The researchers also noted phishing campaigns using the “sf_rand_string_lowercase6” path in URLs, a tactic that further obscures the malicious intent behind the links.

What makes these phishing campaigns even more dangerous is the attackers’ use of deep linking and dynamic content generation. By embedding parameters in the URL, attackers pre-fill login forms with the victim’s email address, giving the phishing pages an air of authenticity. This personalized approach makes it more likely that users will trust the page and enter their credentials, ultimately exposing them to the risk of identity theft or unauthorized access to sensitive systems.
One of the key challenges in detecting these phishing attacks is that the original URLs often reside on legitimate or compromised domains, which makes them difficult to identify as malicious. Attackers also use techniques like URL shortening or leveraging marketing platforms to obscure the true destination of their phishing links.
Once users click the phishing link, they are redirected through a series of URLs, often landing on a malicious page hosted under obscure domains, such as hk6.8ik8rq[.]ru. These multi-step URL chains make it difficult for traditional security solutions to block the attacks before they reach their final destination.
The rise of phishing attacks using HTTP refresh headers is a concerning trend, as it represents a new layer of sophistication in phishing tactics. By leveraging server-side redirection before HTML content is processed, attackers can more effectively mask their intentions and trick unsuspecting victims. The Unit 42 report underscores the importance of staying ahead of these evolving threats, as organizations across industries remain at risk from this growing wave of cyberattacks.
Related Posts:
- Beware of Search Results: Hackers Using Fake Websites to Spread Malware
- Cybercriminals Mimic Slack in Sophisticated Malvertising Campaign
- Beware of Fake Sora AI: Cybercriminals Exploit Hype with Malware Attacks
- Beware! Fake Chrome App “Mamont” Steals Banking Details