Image Credit: Group-IB
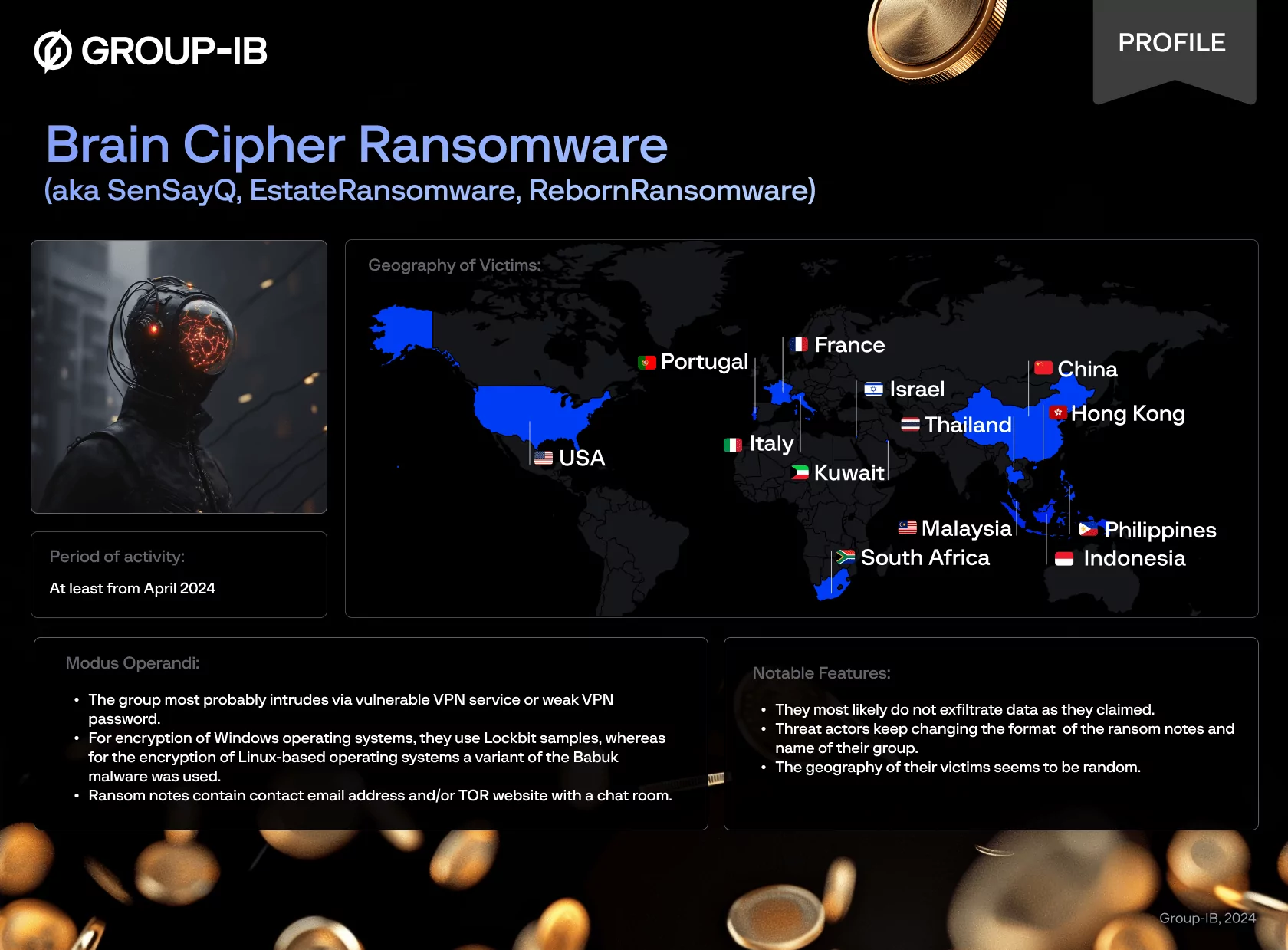
Indonesian government agencies have fallen victim to a large-scale cyberattack orchestrated by the Brain Cipher ransomware group. On June 20, 2024, hackers dealt a severe blow to the country’s critical infrastructure, crippling approximately 210 national and local government services. The customs and immigration services were particularly hard hit, leading to significant delays for travelers at airports.
Initially, the attackers demanded a ransom of 8 million USD. However, they later unexpectedly released the decryptor for free. This incident caught the attention of experts at Group-IB, who decided to conduct a thorough investigation into the group’s activities.
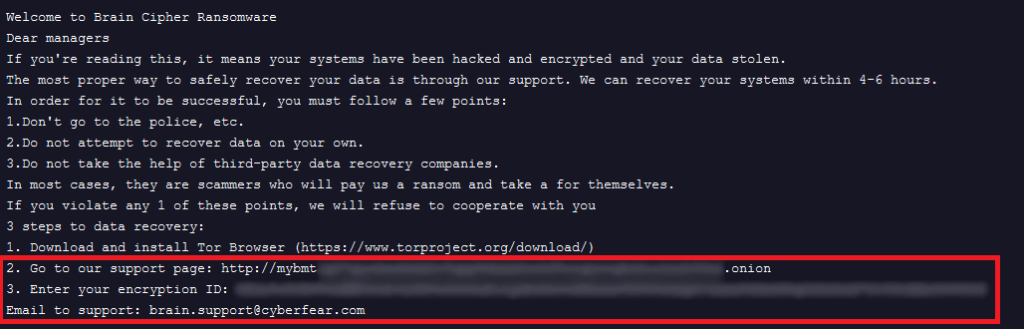
The hackers left distinctive ransom notes on infected systems, containing instructions on how to contact the group for data decryption. The contact information varied from email addresses to links to hidden services on the Tor network.
Researchers determined that the Brain Cipher ransomware group has been active since at least April 2024. Analyzing various ransom note variants allowed them to link this group with other hacking collectives, such as EstateRansomware and SenSayQ.
One of the key findings was the connection between Brain Cipher’s notes and samples of Lockbit malware. Experts also discovered similarities in style and content with the notifications used by the SenSayQ group. Furthermore, the online infrastructure of both groups, including their Tor sites, employed similar technologies and scripts.
Interestingly, the contact email addresses of SenSayQ, EstateRansomware, and another unnamed group were identical. The first traces of EstateRansomware’s activity were detected in April 2024. Based on these data, researchers speculated that the same individuals might be behind both Brain Cipher and EstateRansomware.
Brain Cipher did not confine its attacks to Indonesia. Victims of their onslaught were also found in the Philippines, Portugal, Israel, South Africa, and Thailand. The group operates its own data leak site (DLS), where, at the time of writing, the data of seven companies had been posted.
Most of the ransom notes left by Brain Cipher were linked to malware samples identified as Lockbit. Additionally, the group released a Linux decryptor for an Indonesian victim, which turned out to be a variant of the Babuk ransomware.
Analysis revealed that in July 2024, attacks with similar notes were carried out under the name RebornRansomware. Victims of this group were found in France, China, Kuwait, and Indonesia.
The peculiarities of Brain Cipher’s data leak site are also noteworthy. It hosted information about breached companies, with a countdown timer set for each leak. This tactic applied additional pressure on the victims, forcing them to make a quicker decision regarding payment.
Group-IB analysts compiled a timeline of events showing changes in the ransom notes of the supposedly connected ransomware groups. Some of Brain Cipher’s victims were identified even in August 2024, while some of SenSayQ’s victims were added to their leak site later in June 2024.
The similarities in notes, correlation of email addresses, and the chronological sequence of name changes suggest that EstateRansomware, SenSayQ, Brain Cipher, and RebornRansomware might be operated by the same individuals. However, researchers refrain from speculating on the reasons for the group’s constant rebranding in an era of intensified hunting for major ransomware programs.
Group-IB notes that their team will continue to monitor Brain Cipher’s activities, regardless of what new name the group may adopt in the future. Experts emphasize the importance of ongoing monitoring and analysis of such groups’ activities to develop effective countermeasures against their attacks.
In conclusion, Group-IB provided several recommendations for protection against such attacks. Among them: are regular monitoring and auditing of accounts, implementation of updated management policies, segmentation of critical systems, deployment of application control on hosts, and endpoint detection and response (EDR) solutions. They also recommend subscribing to a managed threat hunting (MTH) service.
Related Posts:
- EstateRansomware Exploits Veeam Vulnerability (CVE-2023-27532) in Sophisticated Attack
- Brain Food botnet spreads malicious PHP scripts and has found 5,000 websites
- The Cobalt hacker group is still active, although the leader was arrested
- Group-IB and other security firms assisted Ukrainian police in taking down on DDoS criminal gangs