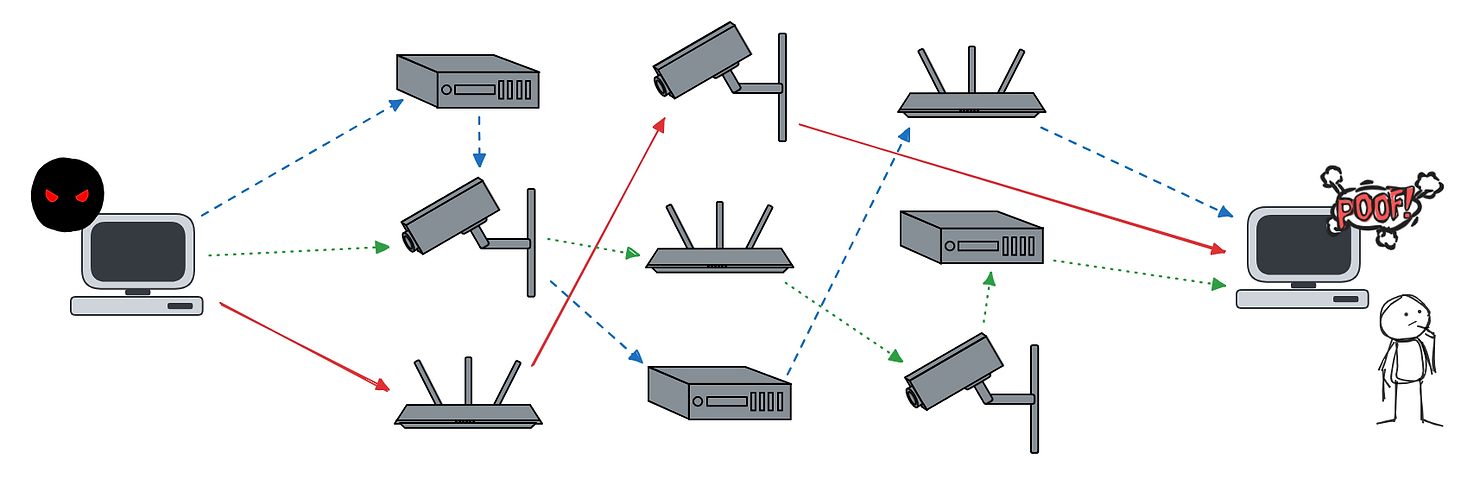
Simplified ORB Network Diagram | Image: Team Cymru
The S2 Research Team at Team Cymru has recently shed light on an escalating threat in the cybersecurity landscape: Operational Relay Box (ORB) networks. Defined as a hybrid between a Virtual Private Network (VPN) and a botnet, ORB networks represent a new level of sophistication in attack obfuscation, enabling threat actors to operate with enhanced anonymity and resilience. The report states that “ORB networks—often referred to as ‘covert,’ ‘mesh,’ or ‘obfuscated’ networks—are becoming increasingly prevalent as threat actors continuously refine their evasion techniques.”
At its core, an ORB network uses a combination of Virtual Private Server (VPS) hosts and compromised Internet of Things (IoT) devices to create a decentralized, multi-node infrastructure. Threat actors use these “operational relay boxes” to route malicious traffic, making it challenging for defenders to trace activity back to its origin. Team Cymru’s report explains, “the botnet aspect of ORB networks provides a means of distributing malicious traffic, while the VPN-like architecture enhances the attacker’s ability to remain undetected by enabling anonymized communication across multiple nodes.”
Such networks are hazardous because they evade traditional detection methods. By creating a mesh network with connections primarily between the relay boxes themselves, attackers effectively mask their entry points, further complicating any attempts to trace or block malicious activity. As Team Cymru warns, “this layer of ‘bots’ grants the attacker a level of anonymity, as the victim only sees connections from the bots, not the attacker’s actual machine.”
A unique aspect of ORB networks is their broad, decentralized structure. By leveraging VPS and IoT devices globally, these networks avoid concentration within specific regions or Internet Service Providers (ISPs), making them nearly impervious to takedowns. The report highlights how this approach “significantly complicates efforts to disrupt the network through remediation of infected devices,” as these compromised nodes are often scattered worldwide.
Furthermore, ORB networks present a risk of collateral damage. Since a substantial portion of the network is made up of compromised IoT devices without dedicated IP addresses, legitimate traffic can mix with malicious activity. As noted by Team Cymru, “blocking such traffic may lead to numerous issues, such as legitimate users being unable to access services or businesses experiencing a decline in genuine traffic.”
Team Cymru’s analysis highlights how ORB networks are used for malicious purposes and as a means of general internet access. In many cases, “normal” traffic such as social media and messaging activity is routed through the same infrastructure as the threat actors’ traffic. This “hiding in the noise” tactic adds another layer of obfuscation, as the legitimate traffic further masks malicious operations.
ORB networks provide capabilities for each stage of the Cyber Kill Chain, from reconnaissance and weaponization to data exfiltration. By using these networks, attackers can conduct covert reconnaissance, probing targets without exposing their true location. They can then proceed to exploit vulnerabilities, establish dynamic command-and-control (C2) channels, and exfiltrate data via rotating exit nodes to obscure the data’s final destination. As Team Cymru observes, “this decentralized approach makes it difficult to track the data’s final destination, slowing down incident response and making it harder to mitigate the attack.”
Defending against ORB networks requires more than conventional perimeter defenses. Proactive threat hunting, behavioral analytics, and network traffic analysis are essential tools for identifying potential ORB network activity. Team Cymru emphasizes that “adopting a Zero Trust approach” is vital, as this model assumes that no device should be trusted by default, regardless of its network location.
Related Posts:
- China’s Cyber Espionage Actors Employ ORB Networks to Evade Detection
- Watch Out for Latrodectus: New Malware from Suspected IcedID Developers Targeting Businesses
- Cisco: 95% of all data centre traffic by 2021 will come from cloud