Experts Boris Larin, Leonid Bezvershenko, and Georgy Kucherin from Kaspersky Lab presented a report titled “Operation Triangulation: What You Get When Attack iPhones of Researchers” at the 37th Chaos Communication Congress (37C3 hacker conference. They summarized their extensive research and publicly disclosed details about the vulnerabilities and exploits used in the notorious attack.
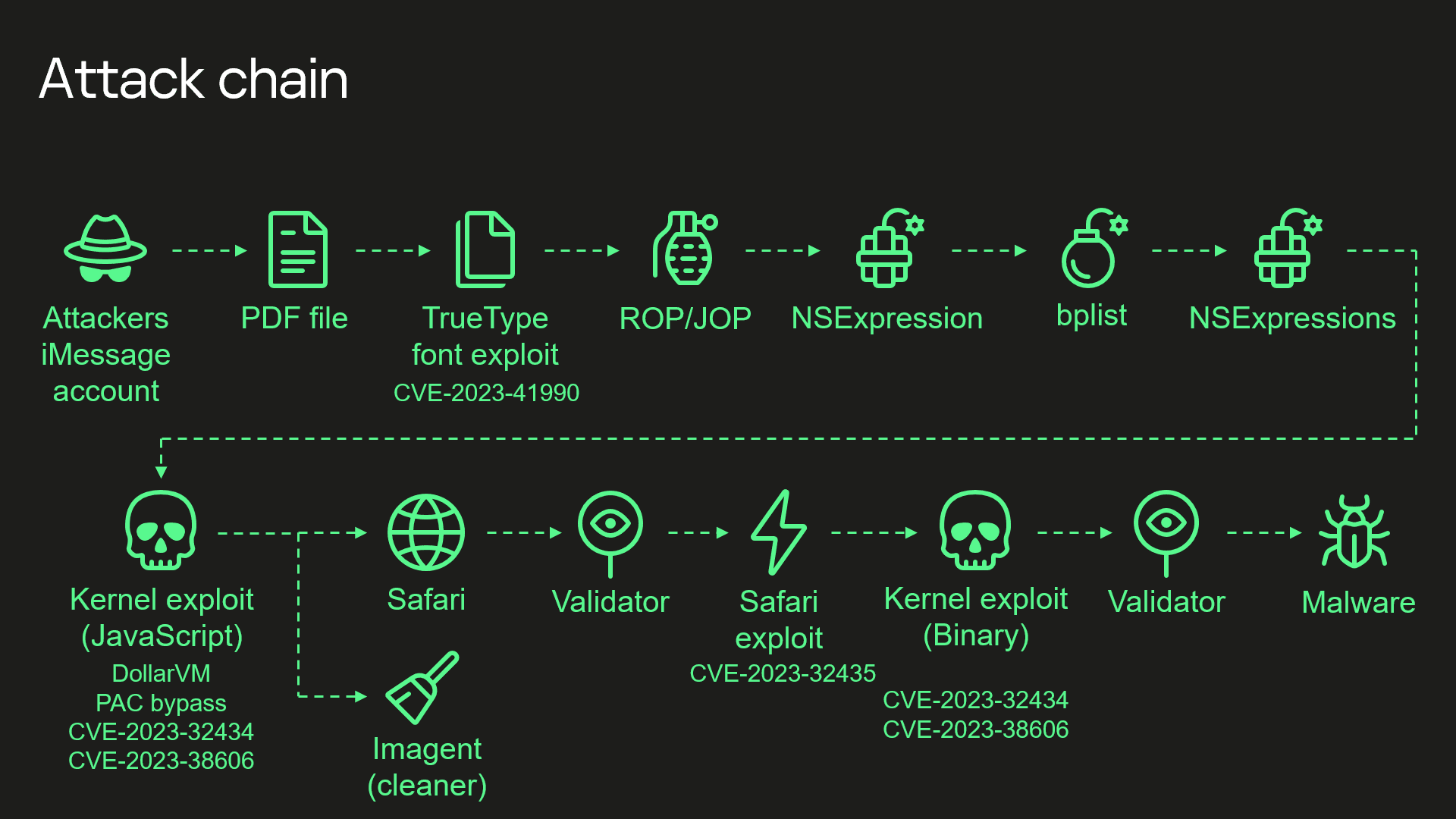
The attack chain revealed that espionage attacks targeting iPhones since 2019 exploited undocumented Apple chip functions to bypass hardware security measures. Experts describe “Operation Triangulation” as “the most sophisticated attack chain we have ever seen.”

This campaign, named “Operation Triangulation,” aimed, according to researchers, to stealthily embed a spy module in iPhones of company employees, including top management and mid-level managers. These attacks reportedly began as early as 2019.
A complex method of distributing exploits through iMessage messages, which required no user interaction, was used for these attacks.
Experts had previously released a detailed report on the TriangleDB malware, written in Objective-C, explaining how the implant was loaded onto devices after attackers gained root access by exploiting a vulnerability in the iOS kernel.
A separate report focused on the stealth and tools hackers used to achieve it, and dissected the implant’s activity post-compromise. Another report addressed five vulnerabilities (including CVE-2023-32434, CVE-2023-32435, CVE-2023-38606, and CVE-2023-41990) used in these attacks, which Apple hastily patched.
- CVE-2023-32434 – An integer overflow was addressed with improved input validation. This issue is fixed in watchOS 9.5.2, macOS Big Sur 11.7.8, iOS 15.7.7 and iPadOS 15.7.7, macOS Monterey 12.6.7, watchOS 8.8.1, iOS 16.5.1 and iPadOS 16.5.1, macOS Ventura 13.4.1. An app may be able to execute arbitrary code with kernel privileges.
- CVE-2023-32435 – A memory corruption issue was addressed with improved state management. This issue is fixed in macOS Ventura 13.3, Safari 16.4, iOS 16.4 and iPadOS 16.4, iOS 15.7.7 and iPadOS 15.7.7. Processing web content may lead to arbitrary code execution.
- CVE-2023-38606 – This issue was addressed with improved state management. This issue is fixed in macOS Monterey 12.6.8, iOS 15.7.8 and iPadOS 15.7.8, iOS 16.6 and iPadOS 16.6, tvOS 16.6, macOS Big Sur 11.7.9, macOS Ventura 13.5, watchOS 9.6. An app may be able to modify sensitive kernel state.
- CVE-2023-41990 – The issue was addressed with improved handling of caches. This issue is fixed in tvOS 16.3, iOS 16.3 and iPadOS 16.3, macOS Monterey 12.6.8, macOS Big Sur 11.7.9, iOS 15.7.8 and iPadOS 15.7.8, macOS Ventura 13.2, watchOS 9.3. Processing a font file may lead to arbitrary code execution.
Analysts report that they have nearly completed reverse engineering all aspects of this attack chain and plan to release a series of articles next year detailing each vulnerability and its exploitation. However, some aspects of one particular vulnerability, CVE-2023-38606, remain elusive.
CVE-2023-38606 was addressed on July 24, 2023, with the release of iOS and iPadOS 16.6. Experts explain that new iPhone models have additional hardware protection for sensitive kernel memory areas, preventing attackers from gaining full control of the device, even with read-write access to the kernel memory, as in the case of CVE-2023-32434. However, they discovered that hackers bypassed this hardware protection using another Apple SoC hardware function.
This function allows attackers to write necessary data to a specific physical address, bypassing memory hardware protection, by writing data, the destination address, and the data hash into undocumented, firmware-unused hardware registers of the chip.
It is assumed that this undocumented hardware function was likely intended for debugging or testing by Apple engineers or at the manufacturing plant, or included by mistake. Since this function is not active in the firmware, researchers admit they have “no idea” how attackers figured out its use, given the lack of instructions for its application.
In the technical part of the report, researchers explain that the CVE-2023-38606 vulnerability targets unknown MMIO (memory-mapped input/output) registers in Apple A12-A16 Bionic, which turned out to be linked to the GPU coprocessor but were absent in the device tree.