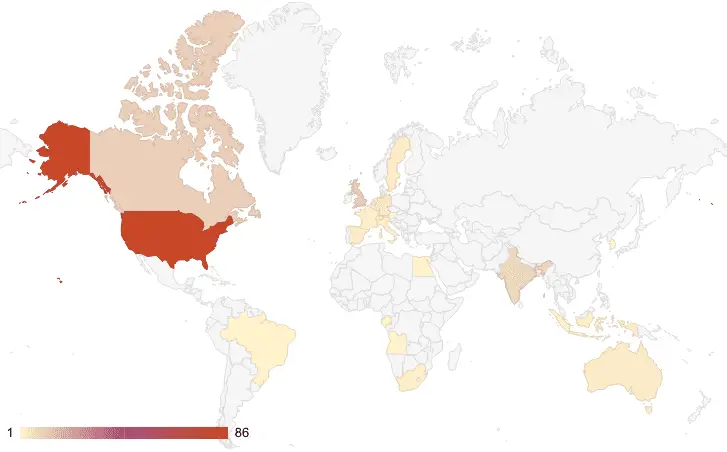
A map showing the countries impacted by BianLian in 2023
The BianLian ransomware group, first identified in 2022, has quickly ascended the ranks to become one of the most formidable extortion groups. Unit 42 researchers have meticulously tracked BianLian’s activities, revealing a group that not only targets but adapts and evolves, reflecting the dynamic nature of cyber threats today.
BianLian‘s method of operation is both sophisticated and alarming. Initially adopting a double-extortion tactic, the group has recently pivoted to a more sinister strategy: extortion without encryption. Rather than encrypting the victim’s data, BianLian goes straight for the jugular, stealing sensitive information and demanding ransom under the threat of public disclosure.
The sectors most affected by BianLian’s malfeasance are healthcare and manufacturing, with significant impacts also seen in professional and legal services. The geographical footprint of their attacks spans North America, Europe, and India, with the United States bearing the brunt of their activities. One chilling example is the group’s claim to have exfiltrated 1.7 TB of data from a California-based hospital in January 2023, underscoring the dire consequences of their attacks on critical infrastructure and the potential risk to human lives.

An intriguing facet of BianLian’s operation is the shared use of a small custom .NET tool with the Makop ransomware group. This shared arsenal hints at a potential collaboration or shared lineage between these nefarious entities, suggesting a complex web of alliances within the cybercriminal underworld. The use of publicly available tools like the Advanced Port Scanner further indicates a sophisticated understanding of network vulnerabilities, enabling BianLian to navigate and exploit their targets’ digital defenses with precision.

Unit 42’s analysis, mapped to the MITRE ATT&CK framework, reveals BianLian’s multi-stage attack lifecycle. From initial access via stolen Remote Desktop Protocol (RDP) credentials and exploitation of vulnerabilities to credential dumping and persistence through backdoor components, BianLian exhibits a comprehensive strategy to infiltrate, dominate, and exploit their victims’ networks.
As BianLian continues to adapt its tactics, techniques, and procedures (TTPs), the call for vigilance has never been louder. The group’s shift towards a steal-and-extort scheme, coupled with its technical prowess and strategic evolution, marks a significant point of concern for cybersecurity professionals and organizations worldwide.