BingoMod Malware: Android Banking Trojan Empties Accounts, Wipes Devices

The cybersecurity company Cleafy has discovered a malicious software named BingoMod targeting Android platforms. This malware attempts to access device-based bank accounts and transfer the deposits. After completing the theft, it wipes the affected device to eliminate activity data.
Cleafy indicates that BingoMod is a remote access Trojan (RAT), enabling attackers to remotely control the compromised device and obtain bank account details through fraudulent means, such as prompting users to enable accessibility services and acquire relevant control permissions.
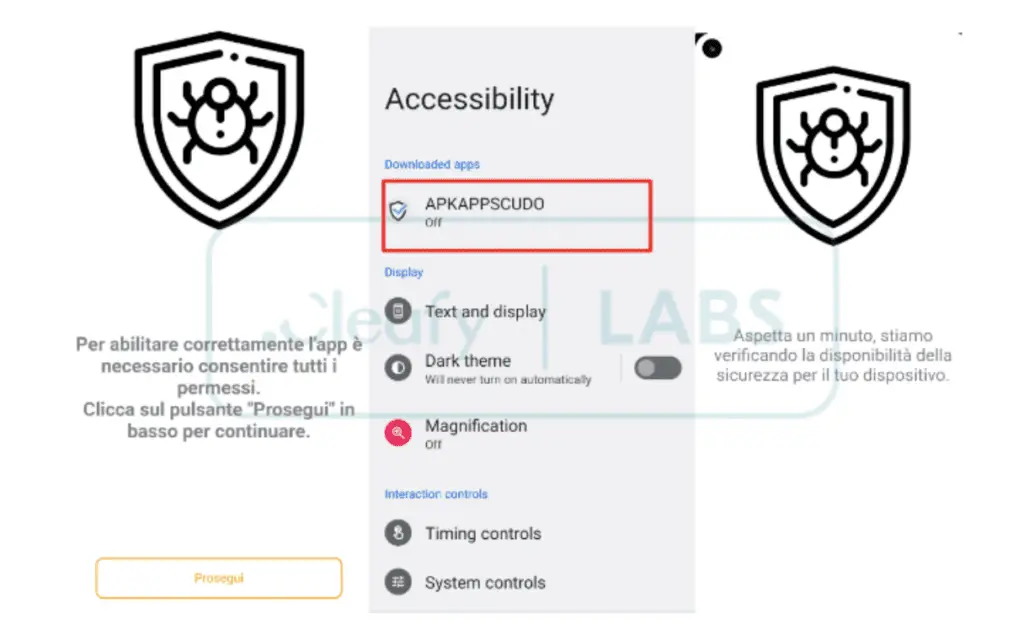
Starting phase of BingoMod
Once the necessary permissions are obtained, BingoMod self-extracts and installs, using the acquired permissions to activate the keyboard operation logging feature of accessibility services. This allows it to steal user credentials entered during banking services. Additionally, it intercepts SMS messages to capture verification codes for financial transactions, facilitating the transfer of funds from the user’s bank account in the background.
During the attack, BingoMod also utilizes the system media projection API to capture screen content and transmit it back to the attackers for verification. Upon completing the attack, BingoMod further erases external storage devices on the affected device, typically additional memory cards. Attackers can even remotely control and manually wipe all stored content on the device, making it difficult for the victim to trace.
Therefore, Cleafy advises against installing unknown apps on Android devices and being cautious of suspicious permission requests. They also recommend installing security protection software, enabling two-factor authentication, and regularly checking all banking transaction records to ensure no malicious attacks have occurred.




