bishop: Hunt for vulnerable websites as you browse
Bishop
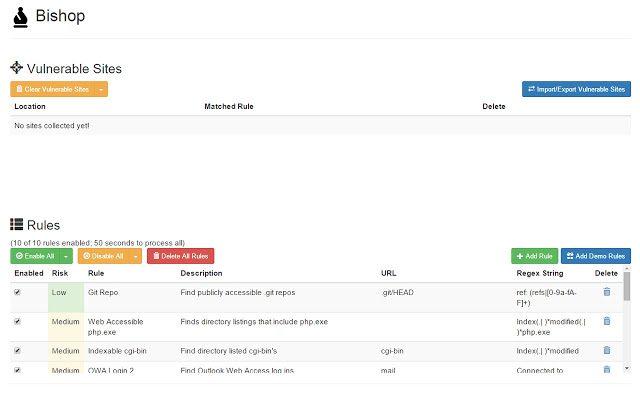
Bishop is a vulnerability scanner that searches websites in the background while you browse, looking for exposed version control systems, misconfigured administrative tools, and more.
It works by searching for files with a given path on the current URL path and all parent paths, applying given regex to the results to check for proof positive of a vulnerable location. If the path returns 200 and matches the regex, it’s flagged as vulnerable and alerts you. All rules are run on all directories in a set of time-staggered background XHR requests, so network throughput remains high at all times.
Bishop comes with a set of rules that hunt for the lowest hanging fruit, but the rule system is entirely extensible – rules are regular expressions that are run on specified directories, so if you can turn it into a regex, Bishop will look for it. Try loading Bishop with the demo ruleset and see how it works. The risk classification allows you to set different tiers of vulnerability so applications can be tested to stricter or looser security guidelines.
Bishop is intended SOLELY for legal use on web servers that you control or are permitted to scan, and the developers are not responsible for how you choose to use this software. Be safe and legal with this tool.
Installation
Download from the Chrome Web Store.
Adding Rules to the Code
If you have a general rule that you think others could find helpful, feel free to PR it. The fields are pretty self-explanatory and match the GUI rule addition interface. The uid field can be left as is; it’s just adding the unique ID for the rule. The risk is intended to describe the relative risk that such a vulnerability would indicate, allowing you to include stricter or looser security requirements for different applications.
Copyright (c) 2016 jack.kingsman@gmail.com
Source: https://github.com/jkingsman/





