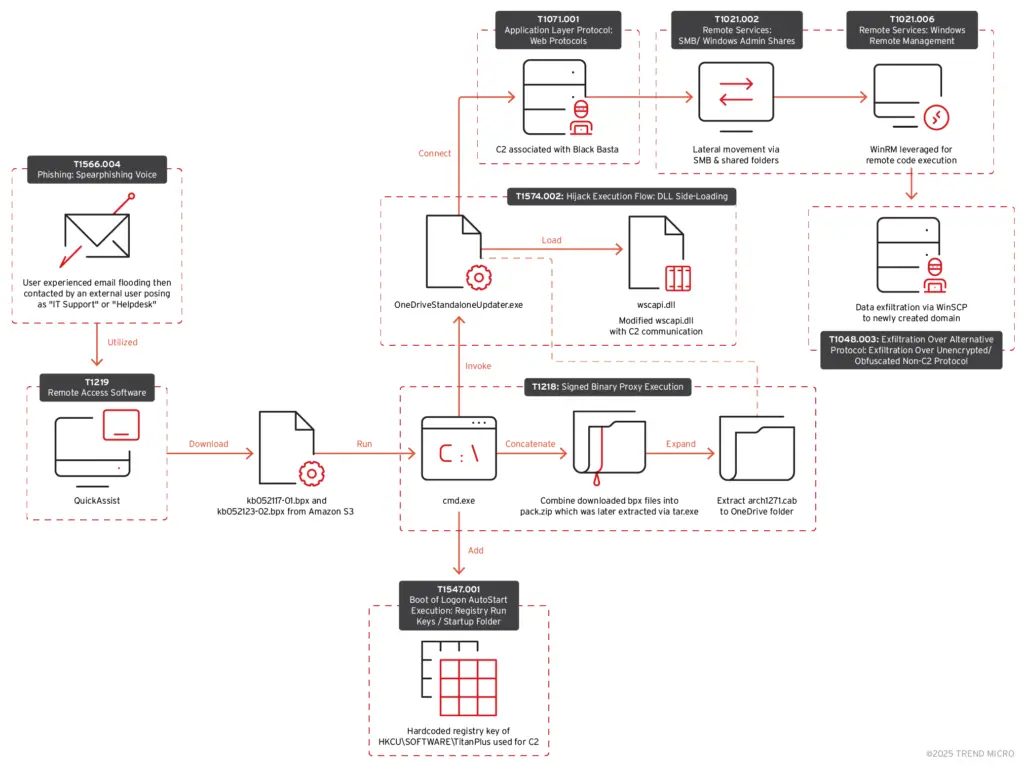
The attack chain of Cactus ransomware | Source: Trend Micro
The Black Basta and Cactus ransomware groups have evolved their attack arsenal, now leveraging the BackConnect malware to fortify their foothold on compromised machines. According to a recent report by Trend Micro’s Managed XDR and Incident Response (IR) teams, these groups have been observed deploying QBACKCONNECT, a strain linked to the infamous QakBot loader malware, which was dismantled during the 2023 Operation Duckhunt crackdown.
The Black Basta and Cactus ransomware groups employ a combination of social engineering, abuse of legitimate tools, and cloud-based infrastructure to blend malicious activity into normal enterprise workflows.
Attackers employ a variety of social engineering techniques to gain access to corporate environments. This includes:
- Microsoft Teams impersonation – Attackers pose as IT personnel to manipulate users into granting access.
- Quick Assist exploitation – A built-in Windows tool abused to establish remote control over victims’ machines.
- OneDriveStandaloneUpdater.exe sideloading – Attackers exploit Microsoft OneDrive’s update process to execute malicious DLLs and install BackConnect malware.
“Attackers utilized social engineering to lure the victims into giving them initial access. Attackers abused Microsoft Teams for impersonation and privilege escalation,” the report states.
Once inside the system, the BackConnect malware establishes a persistent remote connection, allowing attackers to:
- Execute commands and exfiltrate sensitive data.
- Steal login credentials, financial information, and personal files.
- Enable further ransomware deployment.
According to Trend Micro, “this new BackConnect malware (QBACKCONNECT) has artifacts suggesting links to QakBot, a loader malware that was the predominant initial access method used by Black Basta before the takedown.”
Trend Micro’s Threat Intelligence data highlights that since October 2024, Black Basta has executed attacks globally, with a major focus on North America and Europe:
- North America: 21 breaches (17 in the U.S., 5 in Canada)
- Europe: 18 breaches (5 in the U.K.)
- Manufacturing was the most targeted industry, followed by financial consulting and real estate.
“In 2023, the group behind Black Basta reportedly extorted US$107 million in Bitcoins from their victims,” the report writes.
Trend Micro researchers also observed Cactus ransomware operators utilizing similar TTPs (Tactics, Techniques, and Procedures), signaling potential cross-pollination between the two groups.
“Some of the key members of Black Basta have left the group to join the Cactus Ransomware operation, as observed in the TTPs overlaps between the two groups,” the report explains.
Notably, Cactus operators were seen:
- Using email bombing and Microsoft Teams impersonation to deceive users.
- Deploying WinSCP to facilitate file transfers across infected systems.
- Compromising ESXi hosts by disabling security features and deploying SystemBC proxy malware.
The Black Basta and Cactus ransomware groups continue to refine their tactics, leveraging BackConnect malware to enhance their operational resilience. As ransomware actors exploit legitimate enterprise tools to bypass traditional defenses, proactive monitoring and robust security frameworks remain the most effective countermeasures.
Related Posts:
- QBot Resurfaces: New BackConnect Malware Signals a Dangerous Evolution
- Black Basta’s Evolving Tactics and the Rising Role of LLMs in Cyber Attack
- Black Basta Ransomware Group Elevates Social Engineering with Microsoft Teams and Malicious QR Codes
- Sophisticated Social Engineering Campaign Linked to Black Basta Ransomware
- GhostSocks Malware: A New Cyber Threat Leveraging SOCKS5 Backconnect for Evasion