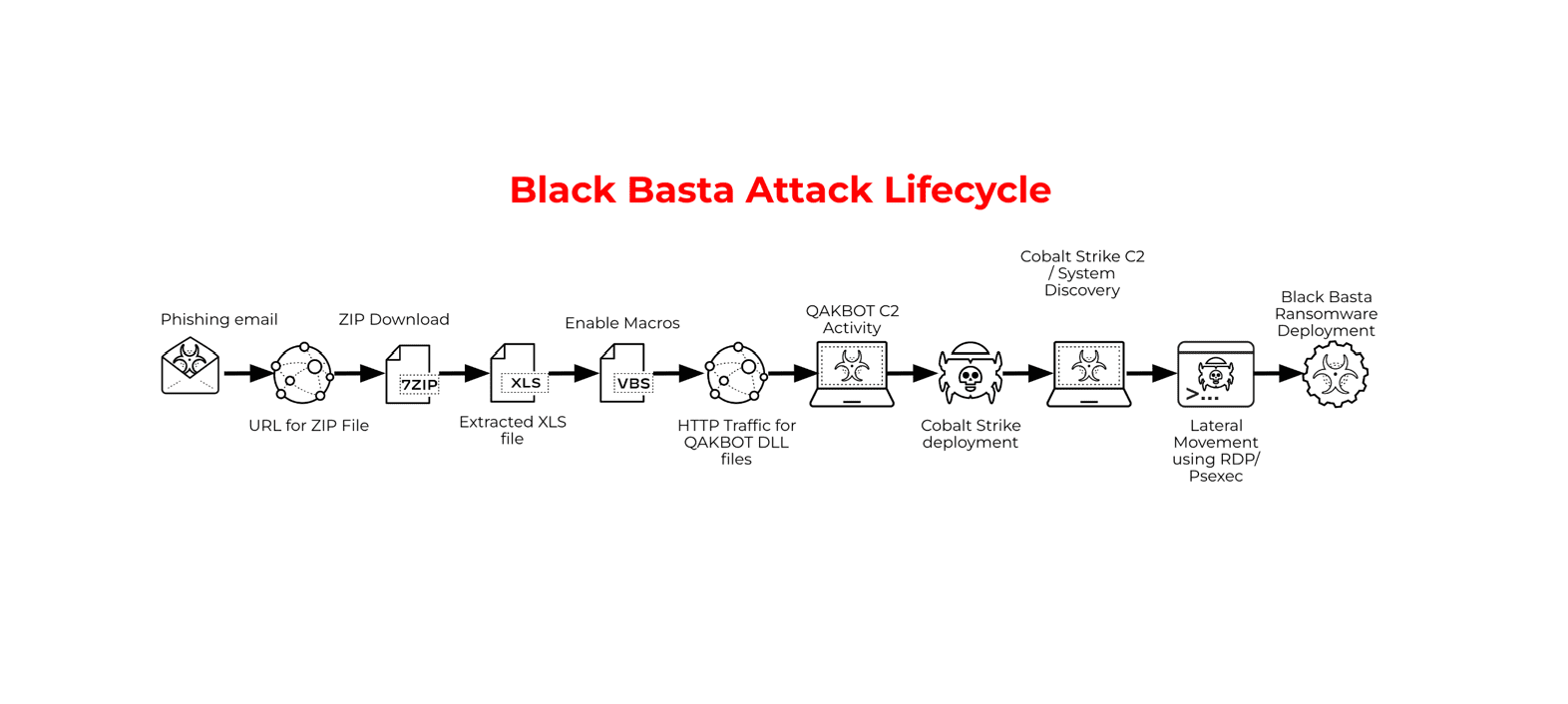
Black Basta attack lifecycle | Image: Unit 42
The ReliaQuest Threat Research Team uncovered an intensified social engineering campaign tied to the ransomware group Black Basta. Known for using email spam to overwhelm users into creating legitimate help-desk tickets, Black Basta has now introduced a range of new tactics that exploit Microsoft Teams chat and malicious QR codes. ReliaQuest reports that these tactics are “targeting many of our customers across diverse sectors and geographies with alarming intensity.”
In one of the most alarming discoveries, Black Basta attackers now use Microsoft Teams chat to communicate directly with targets. This process follows the mass email spam event, where targeted users are added to Teams chats under the guise of external help-desk staff. To mimic legitimate IT support, attackers establish profiles using Entra ID tenants like “supportserviceadmin.onmicrosoft[.]com” or “cybersecurityadmin.onmicrosoft[.]com” and display names like “Help Desk.”
ReliaQuest explains that attackers take this extra step to deceive users: “In almost all instances we’ve observed, the display name included the string ‘Help Desk,’ often surrounded by whitespace characters, which is likely to center the name within the chat.” Most of these actions, according to the time-stamp analysis, seem to originate from Russian time zones.
Another novel twist is Black Basta’s use of QR codes in their phishing arsenal. The attackers have created domains like “qr-s1[.]com” and tailored them to specific targets, such as “companyname.qr-s1[.]com,” in an attempt to make the URLs appear authentic. These QR codes are designed to appear as legitimate company links, further luring users into sharing sensitive information or downloading remote monitoring and management (RMM) tools under the guise of technical support.
While the specific purpose of these QR codes is still under investigation, ReliaQuest notes that it is “realistically possible that the codes direct users to further malicious infrastructure.”
One of the more traditional tactics Black Basta has retained is a high-intensity email spam campaign. “In one incident alone, we observed approximately 1,000 emails bombarding a single user within just 50 minutes,” states ReliaQuest. The barrage of emails pressures users to seek IT help, after which Black Basta impersonates help-desk staff on Microsoft Teams or over the phone. From here, they guide users to install RMM tools like AnyDesk, downloading files like “AntispamAccount.exe” and “AntispamUpdate.exe,” which access credentials and propagate across networks.
Once inside, the threat actors can deploy Cobalt Strike beacons to domains made to look like legitimate organizations, such as “companymartec[.]com.” This technique aims to establish lateral movement across an organization’s network by dumping password hashes with tools like Impacket’s “secretsdump.py.”
ReliaQuest recommends a multi-layered defense strategy encompassing the blocking of known malicious domains, restricting external communication within Microsoft Teams, enforcing stringent anti-spam policies, and enabling comprehensive logging for timely detection and investigation.
Related Posts:
- Black Basta’s Evolving Tactics and the Rising Role of LLMs in Cyber Attack
- ClearFake Campaign Employs Novel Social Engineering Tactic to Deliver LummaC2 Infostealer
- Ransomware Threat Escalates as Scattered Spider and RansomHub Combine Forces
- ZeroLogon to NoPac Vulnerability: Black Basta Group’s Exploit Arsenal Revealed
- Sophisticated Social Engineering Campaign Linked to Black Basta Ransomware