An example of a victim profile on BlackSuit's leak site
In a recent series of events that disrupted major operations, the KADOKAWA Corporation experienced service outages that extended to multiple websites. What initially appeared to be a technical glitch soon escalated into a full-blown ransomware attack orchestrated by the notorious BlackSuit ransomware group. Five weeks ago, BlackSuit claimed responsibility for the attack and issued an ultimatum: meet their ransom demands or face the public release of stolen information on July 1st.
An in-depth analysis by Deep Instinct’s Threat Lab has revealed a disturbing evolution in BlackSuit’s tactics and techniques. The ransomware now employs advanced obfuscation methods, including masking its payload as a legitimate component of the Qihoo 360 antivirus software, significantly reducing detection rates.
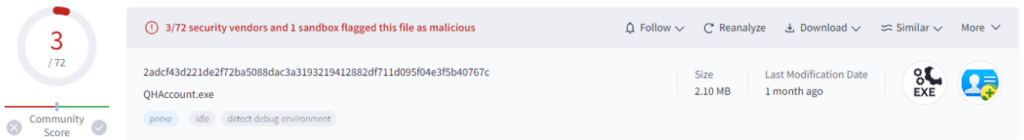
Additionally, Deep Instinct’s research indicates that newer BlackSuit samples exhibit a much lower detection rate compared to earlier versions, suggesting a deliberate effort by the threat actors to evade security measures.
The latest samples feature encoded strings and imported DLLs designed to thwart analysis efforts. A mandatory ID argument bypasses automatic emulation, enhancing evasiveness. One of the most impactful changes involves disguising the ransomware as a legitimate part of the well-known free antivirus software, Qihoo 360. This includes false watermarking, significantly lowering detection rates. The masquerade file, although not signed, closely mimics Qihoo’s real QHAccount.exe file, effectively evading security software.
BlackSuit also incorporates advanced features such as asymmetric key exchange for encryption, deletion of shadow copies to disable easy restores, and the capability to disable safe mode and shut down systems. Encrypted files are appended with the .blacksuit extension, and a ransom note, usually named readme.blacksuit.txt, is dropped.
BlackSuit ransomware employs a variety of initial attack vectors, including RDP with stolen credentials, VPN and firewall vulnerabilities, Office email attachments with macros, torrent websites, malicious ads, and third-party trojans. The attackers also utilize tools like CobaltStrike, WinRAR, PUTTY, Rclone, Advanced IP Scanner, Mimikatz, and GMER. This diverse range of vectors allows BlackSuit to target a broad spectrum of victims, endangering vast amounts of data.

The BlackSuit group operates a news and leak site on the Dark Web, where they publish exfiltrated data of their victims once ransom deadlines pass. These profiles include critical information about the affected organizations, such as industry, employee count, revenue, and contact details.