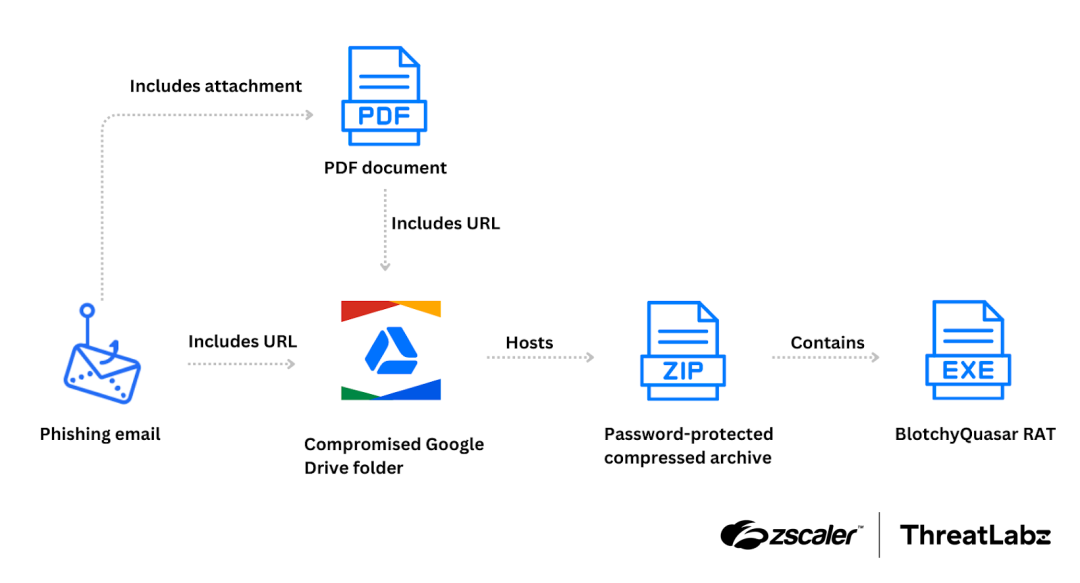
A BlindEagle attack chain | Image: Zscaler
Cybersecurity researchers at Zscaler ThreatLabz have uncovered a new wave of attacks by the BlindEagle APT group, this time zeroing in on the Colombian insurance sector. Utilizing phishing emails masquerading as tax notifications, the threat actors aim to trick victims into downloading a malicious ZIP archive containing the BlotchyQuasar remote access trojan (RAT).
The attack begins with phishing emails impersonating DIAN, Colombia’s National Tax and Customs Authority. The emails, designed to instill urgency, claim the recipients owe back taxes and risk asset seizure. Victims are urged to download a ZIP file from a link in the email or an attached PDF, both of which lead to a BlotchyQuasar RAT payload. This malware enables BlindEagle to infiltrate systems, steal credentials, and monitor banking activities.

The BlotchyQuasar RAT, a variant of QuasarRAT, is heavily obfuscated to evade detection. Once the ZIP file is downloaded, the RAT is deployed using multiple layers of protection, including customized obfuscation tools like DeepSea and ConfuserEx. This layered defense makes reverse engineering the malware difficult, adding to its stealth.
Upon execution, BlotchyQuasar connects to its command-and-control (C2) infrastructure, retrieving the C2 domain via Pastebin. The RAT then begins its malicious activity, which includes logging keystrokes, stealing credentials, and monitoring interactions with specific banking services like Banco Coomeva and PayPal.
BlindEagle shields its infrastructure using dynamic DNS services and compromised VPN nodes. The C2 domains are hosted on services like linkpc[.]net, and traffic is routed through IP addresses associated with Powerhouse Management VPN, known to be used by the threat actor. These tactics make it difficult to trace the origin of the attack, as the group obfuscates its true location.
BlotchyQuasar is particularly dangerous for its ability to target banking and payment services. It monitors victims’ interactions with financial websites by examining the titles of newly opened windows. If a victim accesses a targeted service, BlotchyQuasar logs the interaction and captures credentials, enabling the attackers to siphon off payment details and banking information.
The latest campaign from BlindEagle highlights the evolving threats targeting South America’s insurance sector. With BlotchyQuasar, BlindEagle continues to demonstrate its capabilities in cyber espionage, leveraging phishing and advanced obfuscation to steal sensitive financial data. Organizations, particularly in Colombia, must remain vigilant and strengthen their defenses against these persistent threats.
Related Posts:
- BlindEagle APT Group: A Persistent Threat in Latin America
- Attacker use DDoS attack to hit three major Dutch banks
- Stealthy New Android Trojan Disguised as Popular Apps Steals Your Data