The MITRE timeline details the attack path taken by the threat actor | Image: Unit 42
Cybersecurity researchers at Unit 42 have uncovered a concerning shift in the tactics employed by the notorious threat actor group, Bling Libra. Previously recognized for their involvement in high-profile data breaches, including the Microsoft GitHub and Tokopedia incidents in 2020, Bling Libra has historically focused on monetizing stolen data through underground marketplaces.
However, a recent report from Unit 42 highlights a significant evolution in their modus operandi. In 2024, Bling Libra has pivoted from data theft to extortion, specifically targeting vulnerabilities within cloud environments.
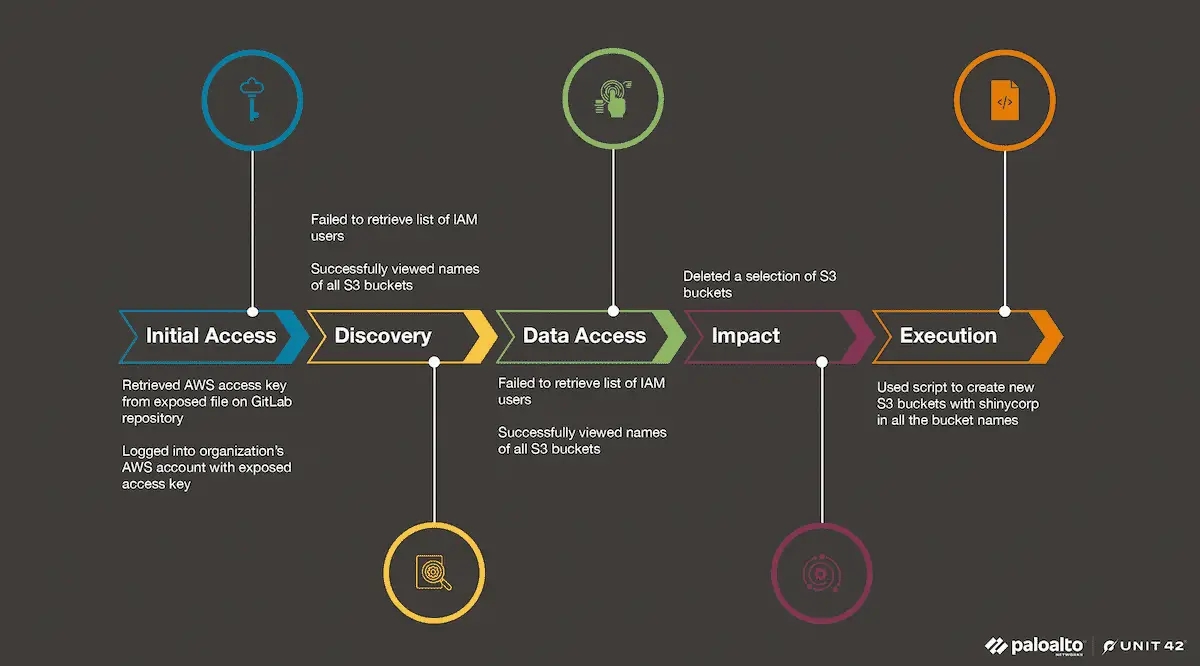
The latest attack detailed by Unit 42 began with Bling Libra obtaining AWS credentials from a sensitive file exposed online. The credentials belonged to an Identity and Access Management (IAM) user, giving the attackers access to the victim’s AWS account. Though the permissions were limited to Amazon S3 resources, Bling Libra exploited these to gain a foothold in the cloud environment.
Once inside, Bling Libra conducted a series of AWS API calls to explore the extent of their access. Using tools like S3 Browser and WinSCP, they methodically mapped out the S3 buckets and determined what data they could exploit. Their discovery phase was carefully executed, leveraging CloudTrail logs to track their activities and ensure they remained under the radar.
After a month of reconnaissance, Bling Libra escalated its attack by using WinSCP to access and manipulate the S3 buckets. They deleted several critical buckets, leaving the organization without crucial data. The absence of S3 server access logging and S3 data logging in the environment meant that much of the attackers’ exfiltration activity went unnoticed until it was too late.
The final phase of the attack saw Bling Libra create new S3 buckets with mocking names, signifying their control over the environment. The group then sent an extortion email, demanding payment in exchange for the return of the data and the cessation of further attacks. The email highlighted their new strategy of using extortion as a primary means of monetizing their breaches.
Unit 42’s report also provides a deep dive into the tools used by Bling Libra, specifically S3 Browser and WinSCP. These tools allowed the threat actors to interact with the AWS environment efficiently, and the detailed analysis in the report helps incident responders differentiate between legitimate tool usage and malicious activity.
Unit 42 strongly recommends organizations adhere to the principle of least privilege and implement robust security measures, such as utilizing IAM Access Analyzer and AWS Service Control Policies, to mitigate the risk of similar attacks.
As organizations increasingly rely on cloud infrastructure, it is imperative to maintain a proactive and vigilant approach to cybersecurity.
Related Posts:
- Muddled Libra Threat Group: A Formidable Threat to the Modern Enterprise
- “Muddled Libra” Hackers Shift Focus to Cloud and SaaS Attacks
- New Phishing Campaigns from Scattered Spider Target Finance and Insurance Industries
- Hackers use social engineering technique to extortion of bitcoin