Phishing letter | Source: BI.ZONE
The BI.ZONE Threat Intelligence team has released a new report detailing the evolution of the Bloody Wolf cybercrime group, revealing an expansion of their targets and a shift in their tactics. While previously known for primarily targeting organizations in Kazakhstan with the STRRAT malware, Bloody Wolf has now been observed attacking entities in Russia as well, compromising over 400 systems in their latest campaigns.
“Attackers tend to replace malware with legitimate solutions to minimize detection by conventional defenses,” BI.ZONE warns. By leveraging NetSupport, a widely used remote administration tool, the group gains full control over compromised machines while evading many endpoint security solutions.
In previous operations, Bloody Wolf relied on custom malware to establish footholds in target networks. Now, widespread telecommuting has provided new opportunities for attackers, as remote administration tools like NetSupport are increasingly used for legitimate IT support. This allows threat actors to exploit existing software instead of deploying malicious payloads.
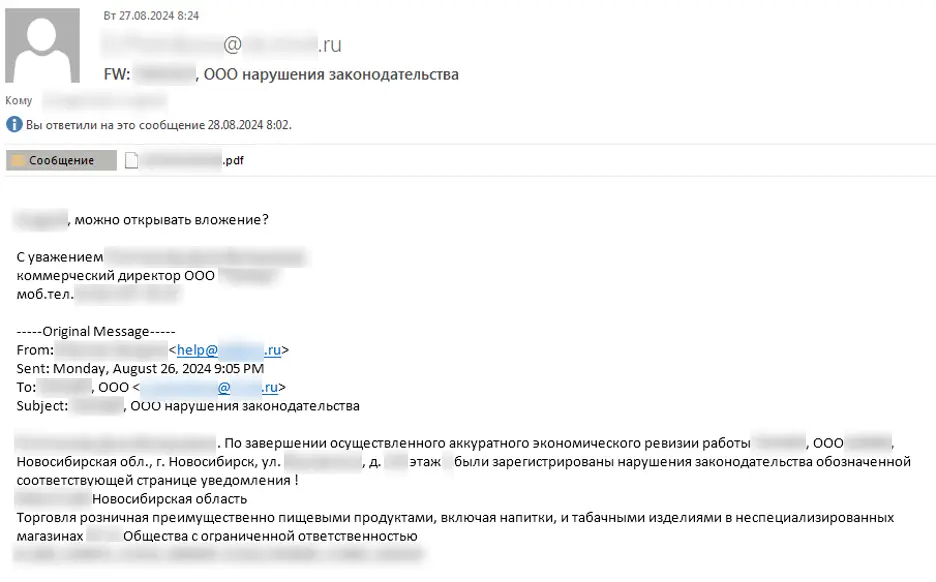
BI.ZONE detected Bloody Wolf’s latest campaign in December 2024, when the group launched a phishing campaign targeting Kazakhstan-based organizations. Attackers disguised their phishing documents as “compliance notices,” tricking victims into downloading a malicious JAR file named NCALayerUpdatedRU.jar.
Once executed, the malicious loader performed several key actions:
- Created a hidden directory in %APPDATA% to store the payload.
- Connected to Pastebin to retrieve URLs for downloading NetSupport components.
- Executed update.bat and run.bat scripts to install and persistently run NetSupport.
- Sent details of the compromised machine to a dedicated Telegram chat controlled by the attackers.
Further analysis of Bloody Wolf’s activity revealed a parallel campaign targeting Russian organizations. Using similar phishing tactics, the attackers disguised malicious PDFs as tax offense rulings. These documents contained phishing links that led to the download of another malicious JAR file, ReshenieJCP.jar.
BI.ZONE points out, “Legitimate remote administration tools often give attackers full access to a compromised system, allowing them to manipulate it in any way they want.” This underscores the importance of behavior-based threat detection, rather than relying solely on blacklists and static indicators.
Related Posts:
- Fortinet FortiGate Firewalls Targeted in Sophisticated Campaign Exploiting Management Interfaces
- C3RB3R Ransomware Strikes Again: Exploiting the Confluence Vulnerability
- Hackers are trying to install NetSupport Remote Access Tool on victim machine through Fake Software Update
- Cisco Talos Warns of Stealthy NetSupport RAT Campaigns